Overview
Cyble Global Sensor Intelligence (CGSI) has identified scanning attempts targeting a critical security vulnerability referred to as CVE-2023-49103, reported on Nov 21, 2023, by ownCloud. This vulnerability, having a CVSS score of 10.0, entails the exposure of sensitive information to an unauthorized user. CGSI observed scanning attempts targeting vulnerable ownCloud instances across the globe starting from Nov 23. ownCloud is an open-source software product for sharing and syncing files in distributed and federated enterprise scenarios. It enables organizations and remote users to manage their documents across servers, computers, and mobile devices collaboratively, maintaining a centralized and synchronized state. During our analysis, an online scanner revealed the existence of over 20,000 “ownCloud” instances accessible on the internet. These systems present potential targets for attackers and may be susceptible to recently identified security vulnerabilities. Given below are the top five countries with open instaces of ownCloud.
Note: Multiple honeypots are also visible among these exposed instances.
Attackers often leverage situations involving critical vulnerabilities, such as CVE-2023-49103, to conduct large-scale attacks, as evidenced by recent incidents where ransomware groups exploited vulnerabilities for mass exploitation. The exploitation of recently disclosed vulnerabilities remains a significant threat, with a focus on addressing the risks associated with the ownCloud vulnerability.
The Proof of Concept (PoC) for this exploit is available on GitHub. We encountered numerous instances where threat actors (TAs) were engaged in discussions about this vulnerability. In one particular case, we discovered a post on the WARLOCK DARK ARMY Telegram channel, as depicted in the figure below. The post included the sharing of an exploit specifically crafted for exploiting this vulnerability.
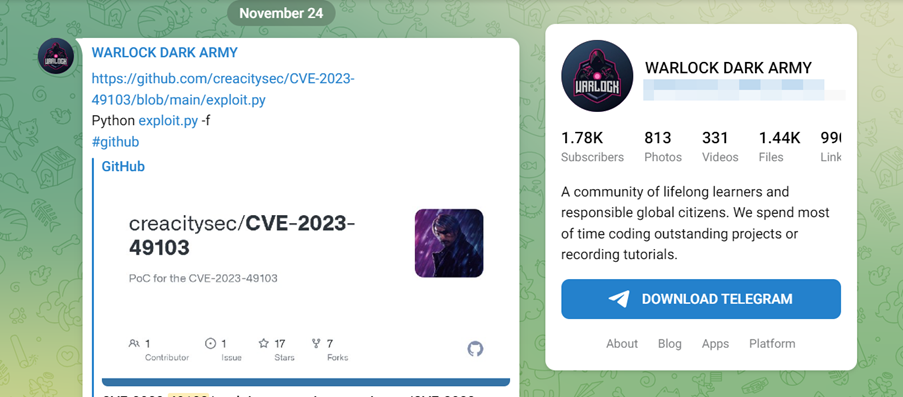
Threat Actors (TAs) behind this telegram channel were also seen selling their ransomware named “WARLOCK DARK ARMY RANSOMWARE” for 600$.
The PoC for this exploit was released on 22 November 2023. Within days of the proof of concept being made public, this vulnerability was actively exploited, which led to the capture of exploitation attempts via CGSI sensors, as shown below.

ownCloud: Exposure of Sensitive Information to an Unauthorized Actor
CVE-2023-49103
CVSSv3.1
10Severity
CriticalVulnerable Software Version(s)
graphapi 0.2.0 – 0.3.0
Description
The “graphapi” app depends on an external library that gives a URL. If you open this URL, it shows the PHP environment’s setup details (phpinfo), which cover all the web server’s environment variables. In containerized setups, these variables might contain sensitive information like the ownCloud admin password, mail server credentials, and license key.Conclusion
The highlighted CVE for ownCloud underscores the importance of addressing security vulnerabilities promptly. The impacts of this vulnerability can be significant, potentially leading to unauthorized access and disclosure of sensitive information. The severity of the issue emphasizes the need for immediate action to patch and secure ownCloud instances. Taking swift measures to apply the necessary updates and safeguards is crucial to ensure the protection of valuable data and maintain a secure computing environment. File-sharing platforms have been consistently targeted for security vulnerabilities, with ransomware groups such as CLOP exploiting these weaknesses in data theft attacks affecting numerous companies globally.Our Recommendations
Here are recommended measures to safeguard against these attacks:-
- Delete the file “owncloud/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php.” Additionally, it is recommended to update the following sensitive information:
-
- OwnCloud admin password
-
- Mail server credentials
-
- Database credentials
-
- Object-Store/S3 access key
-
- Employ vulnerability scanning tools to uncover potential security weaknesses in your systems and applications.
-
- Set up a systematic patch management process, complete with a clearly outlined schedule for routine updates and patches.
-
- Prioritize the timely deployment of critical security patches to enhance overall system security.
Indicators of Compromise (IoCs)
| Indicators | Indicator Type | Description |
| 129[.]146[.]38[.]85 | IP | ownCloud Scanning Attempt |
| 185[.]25[.]51[.]129 | IP | ownCloud Scanning Attempt |
| 154[.]47[.]23[.]51 | IP | ownCloud Scanning Attempt |
| 103[.]73[.]67[.]95 | IP | ownCloud Scanning Attempt |
| 104[.]255[.]175[.]10 | IP | ownCloud Scanning Attempt |
| 15[.]235[.]189[.]156 | IP | ownCloud Scanning Attempt |
| 99[.]245[.]96[.]12 | IP | ownCloud Scanning Attempt |
| 188[.]119[.]57[.]78 | IP | ownCloud Scanning Attempt |
| 207[.]148[.]107[.]193 | IP | ownCloud Scanning Attempt |




















