Key Takeaways
- Over 20 malicious applications have been discovered actively targeting crypto wallet users.
- The apps impersonate popular wallets such as SushiSwap, PancakeSwap, Hyperliquid, and Raydium.
- They prompt users to enter their 12-word mnemonic phrase to access fraudulent wallet interfaces.
- These apps are distributed through the Play Store under compromised or repurposed developer accounts.
- Threat actors employ a common set of techniques: embedding phishing URLs in privacy policies, reusing package naming patterns, and utilizing frameworks for rapid deployment.
Overview
Cyble Research and Intelligence Labs (CRIL) has identified more than 20 cryptocurrency phishing applications on the Google Play Store. These malicious apps impersonate legitimate wallets like SushiSwap, PancakeSwap, Hyperliquid, and others. They employ phishing techniques to steal users’ mnemonic phrases, which are then used to access real wallets and drain cryptocurrency funds.
These apps have been progressively discovered over recent weeks, reflecting an ongoing and active campaign. Upon discovery, CRIL promptly reported the applications to Google, resulting in the removal of most of them from the Play Store. However, as of the time of publishing, a few of these applications are still live on the platform and have been reported for takedown.


The icons of legitimate wallets that we observed being used by the malicious applications to lure victims into trusting them have been listed below:

We also observed that these malicious applications exhibit consistent patterns, such as embedding Command and Control (C&C) URLs within their privacy policies and using similar package names and descriptions. Despite these similarities, the apps are published under different developer accounts.
These accounts were originally used to distribute legitimate apps, including gaming, video downloader, and live streaming applications, and some have amassed over 100,000 downloads. This behavior suggests that these older developer accounts have likely been compromised and are now being leveraged to distribute malicious applications.

The malicious applications we found on the Play Store stealing Mnemonic Phrases of crypto wallet applications are:
| Name | Package name | Privacy Policy |
| Pancake Swap | co.median.android.pkmxaj | hxxps://pancakefentfloyd.cz/privatepolicy.html |
| Suiet Wallet | co.median.android.ljqjry | hxxps://suietsiz.cz/privatepolicy.html |
| Hyperliquid | co.median.android.jroylx | hxxps://hyperliqw.sbs/privatepolicy.html |
| Raydium | co.median.android.yakmje | hxxps://raydifloyd.cz/privatepolicy.html |
| Hyperliquid | co.median.android.aaxblp | hxxps://hyperliqw.sbs/privatepolicy.html |
| BullX Crypto | co.median.android.ozjwka | hxxps://bullxni.sbs/privatepolicy.html |
| OpenOcean Exchange | co.median.android.ozjjkx | hxxps://openoceansi.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.mpeaaw | hxxps://suietsiz.cz/privatepolicy.html |
| Meteora Exchange | co.median.android.kbxqaj | hxxps://meteorafloydoverdose.sbs/privatepolicy.html |
| Raydium | co.median.android.epwzyq | hxxps://raydifloyd.cz/privatepolicy.html |
| SushiSwap | co.median.android.pkezyz | hxxps://sushijames.sbs/privatepolicy.html |
| Raydium | co.median.android.pkzylr | hxxps://raydifloyd.cz/privatepolicy.html |
| SushiSwap | co.median.android.brlljb | hxxps://sushijames.sbs/privatepolicy.html |
| Hyperliquid | co.median.android.djerqq | hxxps://hyperliqw.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.epeall | hxxps://suietwz.sbs/privatepolicy.html |
| BullX Crypto | co.median.android.braqdy | hxxps://bullxni.sbs/privatepolicy.html |
| Harvest Finance blog | co.median.android.ljmeob | hxxps://harvestfin.sbs/privatepolicy.html |
| Pancake Swap | co.median.android.djrdyk | hxxps://pancakefentfloyd.cz/privatepolicy.html |
| Hyperliquid | co.median.android.epbdbn | hxxps://hyperliqw.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.noxmdz | hxxps://suietwz.sbs/privatepolicy.html |
In addition to the 20 applications that shared similar privacy policies and leveraged the Median framework, we also identified two applications that used different package names and privacy policies. Despite these differences, their underlying objective remained the same: to steal users’ Mnemonic Phrases.
| Application name | Package names | Privacy Policy |
| Raydium | cryptoknowledge.rays | hxxps://www.termsfeed.com/live/a4ec5c75-145c-47b3-8b10-d43164f83bfc |
| PancakeSwap | com.cryptoknowledge.quizzz | hxxps://www.termsfeed.com/live/a4ec5c75-145c-47b3-8b10-d43164f83bfc |
The following section covers the technical details of these malicious applications.
Technical Details
Type 1: Use of the Median Framework
A Threat Actor was observed leveraging the Median framework to develop Android applications. This framework enables rapid conversion of websites into Android apps. Upon analyzing the configuration file, we found that the URL “hxxps://pancakefentfloyd[.]cz/api.php” was being used, which also matches the application’s privacy policy URL.

This URL leads to a phishing website specifically designed to steal mnemonic phrases and is loaded within a WebView in the application. In this instance, the phishing site impersonates the legitimate “PancakeSwap” wallet and prompts victims to enter their 12-word mnemonic phrase to gain access to their wallet.

Type 2: Loading Phishing URL into Webview
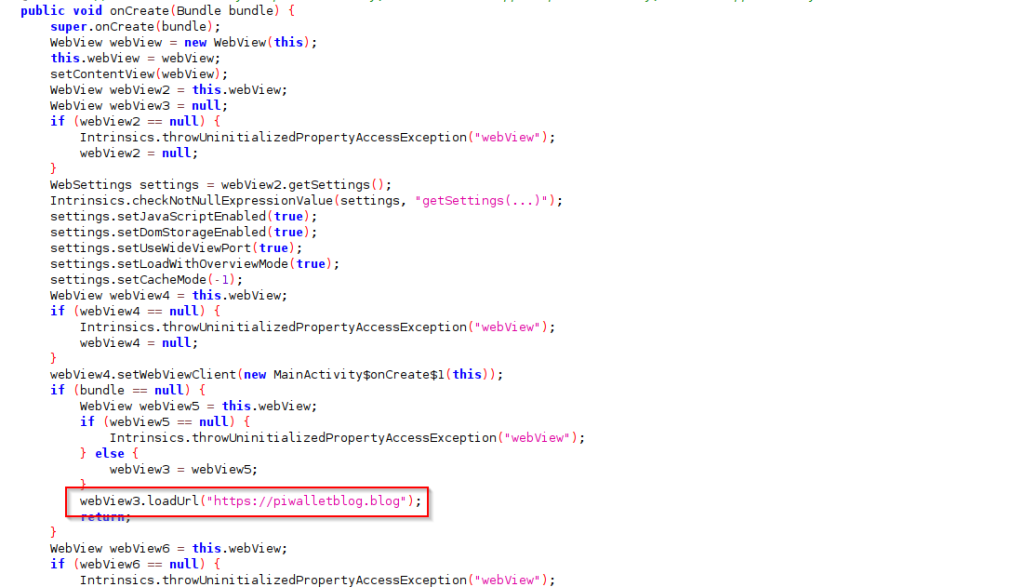
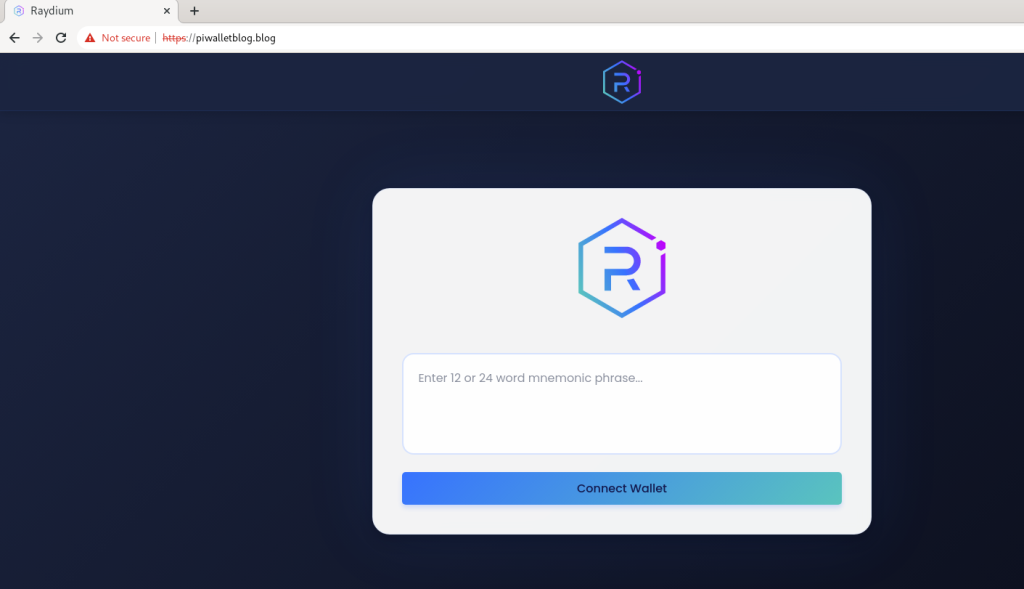
In the second type of malicious application, the Threat Actor directly loads a phishing website into a WebView without using any development framework. The malware opens the URL “hxxps://piwalletblog[.]blog” within the WebView, impersonating the legitimate Raydium wallet. Similar to the previously observed apps, this malicious application also prompts the user to enter their 12-word mnemonic phrase.
The phishing URL “hxxps://pancakefentfloyd[.]cz”, used in one of the observed malicious applications, is hosted on the IP address 94.156.177[.]209. A deeper investigation into this infrastructure uncovered that this IP is associated with over 50 phishing domains, all connected to a broader campaign aimed at stealing mnemonic phrases from users of various cryptocurrency wallets.

These domains impersonate well-known crypto services and are designed to be loaded directly within mobile applications using WebView, making detection more challenging. The threat actor appears to be reusing this infrastructure across multiple fake apps and wallet brands, indicating a centralized and well-coordinated operation.
Conclusion
This campaign highlights a well-coordinated phishing operation targeting the rapidly growing user base of cryptocurrency wallets. By distributing over 20 counterfeit Android applications through the Google Play Store, the threat actors impersonate legitimate wallets such as PancakeSwap, SushiSwap, Raydium, and others to steal users’ mnemonic phrases—the essential keys to accessing their digital assets.
What makes this campaign particularly dangerous is the use of seemingly legitimate applications, hosted under previously benign or compromised developer accounts, combined with a large-scale phishing infrastructure linked to over 50 domains. This not only extends the campaign’s reach but also lowers the likelihood of immediate detection by traditional defenses.
If successful, these attacks can result in irreversible financial losses for victims, particularly since cryptocurrency transactions are not easily reversible or safeguarded like those in traditional banking. As the crypto ecosystem continues to expand, users must remain vigilant, and ecosystem stakeholders—including app stores, security vendors, and developers—must take proactive measures to swiftly identify, block, and report such threats.
Our Recommendations
We have outlined essential cybersecurity best practices that serve as the first line of defense against attackers. We recommend that our readers adhere to the best practices listed below:
- Download apps only from verified developers. Check app reviews and avoid apps that request sensitive information, such as mnemonic phrases.
- Use a reputable antivirus and internet security software package on your connected devices, including PCs, laptops, and mobile devices.
- Create strong passwords and implement multi-factor authentication wherever possible.
- Where applicable, enable biometric security features, such as fingerprint or facial recognition, to unlock your mobile device.
- Be cautious about opening any links received via SMS or emails that land in your phone.
- Ensure that Google Play Protect is enabled on Android devices.
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 4b35a1ed93ab68f0401de34d4eb5dbb582465ee2a8428e16d0beac8bf87a09af | SHA256 | Crypto phishing app impersonating Pancake Swap |
| f288c626be0ba452e098d11b207867793522373c | SHA1 | Crypto phishing app impersonating Pancake Swap |
| b703efe31690b6f84676e795d33f6283 | MD5 | Crypto phishing app impersonating Pancake Swap |
| hxxps://pancakefentfloyd[.]cz/api.php | URL | Phishing URL loaded into Webview |
| 4aa3659c50616d21ef0bda1389cba1ad3fe768b9dd25eee09289ece97cd3623f | SHA256 | Crypto phishing app impersonating Raydium Wallet |
| 265970e7f8f5c9618ffc215c7612eff4fe97f20a | SHA1 | Crypto phishing app impersonating Raydium Wallet |
| b2e6fd5f9662c4215f89240c8c960977 | MD5 | Crypto phishing app impersonating Raydium Wallet |
| hxxps://piwalletblog[.]blog | URL | Phishing site loaded into WebView |
| cryptoknowledge[.]click raydi-commerce[.]cz cetusdi[.]sbs suiscanfl[.]sbs suivisionsl[.]sbs suietsiz[.]cz openoceansi[.]sbs bravebn[.]sbs bullxni[.]sbs walrusod[.]sbs raydifloyd[.]cz meteorafloydoverdose[.]sbs bitunixflo[.]sbs pancakefentfloyd[.]cz suietwz[.]sbs hyperliqw[.]sbs pumpjake[.]sbs raydiumsm[.]sbs harvestfin[.]sbs staratlas[.]sbs bubblemapsblogs[.]sbs sushijames[.]sbs aerodromeaz[.]sbs meteorablog[.]site aerodromesblogs[.]site suietwallets[.]site jumperblogs[.]site sushiblogsite[.]site raydiumblogs[.]site pancakws[.]ru solscanpv[.]ru meteorasp[.]ru | Domain | Crypto phishing domain |




















