Overview
The U.S. Federal Bureau of Investigation (FBI) has issued a fresh alert warning law firms and cybersecurity professionals about ongoing cyber threat activity linked to the Silent Ransom Group (SRG)—also known as Luna Moth, Chatty Spider, or UNC3753. This threat actor is ramping up operations in 2025, with an increasingly aggressive campaign specifically targeting the legal sector across the United States.
Operating since 2022, Silent Ransom Group expanded its tactics in 2025, shifting from callback phishing emails to direct phone-based social engineering. In this tactic, attackers impersonate IT staff to gain unauthorized remote access. Once inside, they exfiltrate sensitive data and demand ransom payments under the threat of public exposure.
According to Cyble’s Research and Intelligence Labs (CRIL) researchers, SRG is a financially motivated threat actor that executes callback phishing campaigns without using malware or encryption.
“By impersonating IT help desks, they trick employees into installing legitimate RMM tools to gain access and exfiltrate data via tools like WinSCP and Rclone,” CRIL’s researchers said. “They operate with call centers, use tailored infrastructure, and demand ransoms up to $800,000 under the threat of exposure.”
Why Law Firms Are Now a Prime Target
While Silent Ransom Group has targeted various sectors, including insurance and healthcare, the legal industry has become the group’s focal point since spring 2023. According to the FBI, the motivation is clear: law firms hold highly sensitive information, including intellectual property, financial records, and confidential legal strategies—data that can be exploited or sold for significant gain.
SRG’s choice of targets indicates a calculated approach: exploiting industries with low tolerance for data exposure and high incentive to pay ransoms quickly and discreetly.
Inside the Attack Chain: Callback Phishing and Fake IT Support
SRG’s hallmark technique has been callback phishing, which tricks targets into calling a fake support number under the guise of resolving bogus subscription charges. These emails, often appearing to be from legitimate vendors, claim small unauthorized charges—usually under $50—to lower suspicion. Victims are instructed to call a number to cancel the charge.
Once the target calls, SRG actors send a link to download remote access software—commonly Zoho Assist, AnyDesk, or Syncro—under the pretense of processing the cancellation. After the tool is installed, the attacker silently establishes persistent access.
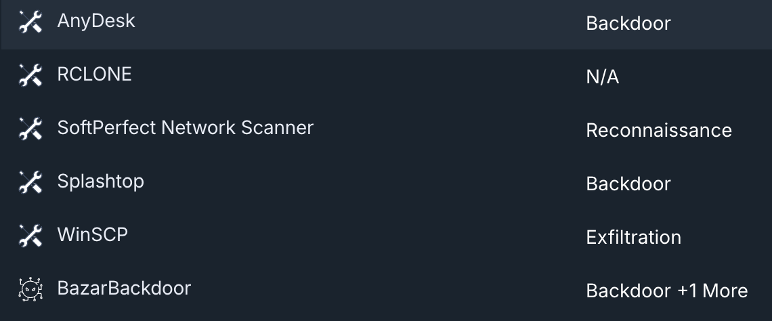
By March 2025, SRG had escalated its tactics by conducting direct phone calls, impersonating IT staff within the victim’s company. Employees are told to join a remote session for “overnight maintenance,” again opening the door for attackers to bypass endpoint protection.
Fast, Quiet, and Dangerous: How SRG Exfiltrates Data
Once remote access is achieved, SRG wastes no time.
- Minimal privilege escalation is needed.
- Data exfiltration tools like WinSCP (Windows Secure Copy) or a stealthy version of Rclone are used immediately.
- If the compromised machine lacks admin privileges, SRG utilizes portable versions of WinSCP to extract data without detection.
The process is silent, fast, and rarely flagged by antivirus software. Once data is exfiltrated, victims receive ransom emails threatening public release unless payment is made. In many cases, SRG follows up with harassing phone calls to company employees, further pressuring firms into negotiation.
Indicators of Compromise (IOCs)
The FBI notes that SRG leaves behind minimal digital footprints. Traditional detection mechanisms may not trigger alerts. However, defenders are advised to watch for these potential IOCs:
- Unauthorized downloads of Zoho Assist, Syncro, AnyDesk, Splashtop, or Atera
- WinSCP or Rclone activity tied to unknown external IP addresses
- Emails or voicemails from anonymous entities claiming data theft
- Subscription-related phishing emails urging callback actions
- Employees receiving suspicious calls from fake IT support claiming to perform routine maintenance
These indicators may not definitively confirm SRG presence but should trigger immediate review and threat hunting protocols.
Recommendations for Defenders
Given SRG’s reliance on social engineering, remote access tools, and stealthy exfiltration methods, the FBI and Cyble strongly recommend the following mitigation strategies:
1. Conduct Employee Awareness Training
Ensure all staff can recognize phishing emails, suspicious calls, and deceptive remote access attempts. Encourage skepticism about unsolicited IT support and unknown subscriptions.
2. Establish Clear IT Authentication Protocols
Organizations should develop and communicate strict procedures for how internal IT departments authenticate themselves. Any deviation should raise immediate red flags.
3. Limit Remote Access Privileges
Disable administrative privileges on employee devices where unnecessary. Implement allowlists for remote access software.
4. Monitor for Unauthorized Tool Usage
Deploy endpoint detection and response (EDR) tools capable of flagging unapproved installations of WinSCP, Rclone, or remote desktop utilities.
5. Backup and Isolate Critical Data
Maintain encrypted, air-gapped backups of essential legal and client files. Test restore procedures regularly to ensure resilience.
6. Implement Multifactor Authentication (MFA)
Require MFA across all employee accounts, especially those with access to sensitive systems or privileged credentials.
Social Engineering is Outpacing Malware
The Silent Ransom Group exemplifies a growing trend in modern cybercrime: human-centered attack vectors that bypass technical controls altogether. By leveraging psychology and trust, SRG infiltrates even well-defended organizations without needing to exploit vulnerabilities or drop malware.
Law firms are ideal targets due to their reputation-centric business models and access to confidential data. These attacks show the importance of treating social engineering threats with the same urgency as traditional cyber intrusions. With attackers evolving their playbooks every few months, defenders must evolve faster.




















