The global threat landscape in the first half of 2025 has not only intensified but also splintered across regions with clear intent and growing precision. According to Cyble’s Global Threat Landscape: H1 2025 report, while ransomware attacks and zero-day exploits rose across the board, the distribution of these incidents varied significantly by geography.
Regional targeting is no longer incidental—it is deliberate, adaptive, and often aligned with sectoral weaknesses and geopolitical fault lines.
The report provides a granular analysis of threat activity across five major regions: North America, Europe and the United Kingdom, Asia Pacific, Australia and New Zealand (ANZ), and the Middle East and Africa (MEA). Each region exhibits its own distinct patterns in threat actor behavior, targeted industries, attack vectors, and operational techniques.
In North America, the United States continues to be the most affected country, with over half of all global ransomware incidents originating there.
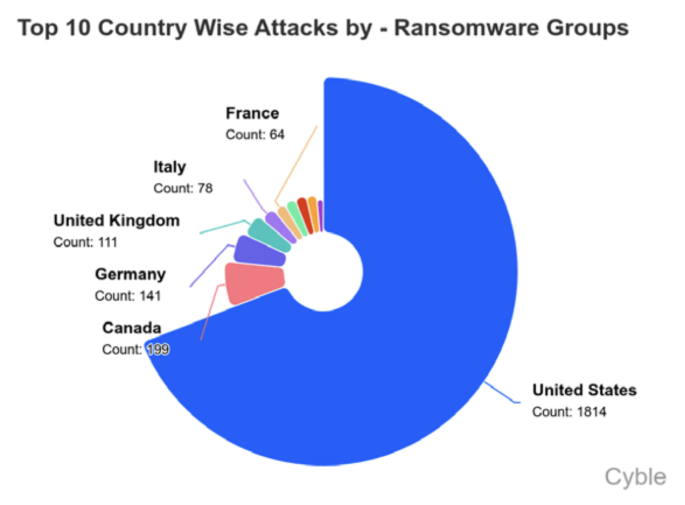
Threat actors such as CL0P, Qilin, and Akira maintained a strong presence in the region, with specific attention toward sectors such as transportation, consumer goods, and professional services. The data indicates that the volume of attacks is not only a reflection of the region’s economic weightage, but also the maturity and density of digital infrastructure—making it a high-value target for data exfiltration and operational disruption.
Across Europe and the United Kingdom, targeted activity has been driven by both established ransomware groups and emerging actors. Germany and the UK remained high on the threat radar, particularly within the manufacturing, construction, and public services domains. The report identifies an increase in infrastructure-level attacks that caused operational delays in transportation and municipal services—indicating a broader shift toward disrupting systems that underpin everyday life.
In the APAC region, ransomware campaigns appear to be closely tied to geopolitical developments. Taiwan, India, Singapore, and Japan were among the most affected nations, with attacks observed against healthcare, IT, BFSI, and manufacturing sectors. Regional adversaries capitalized on vulnerabilities in mid-sized enterprises and service providers, exploiting gaps in cross-border collaboration and regulatory alignment.
Meanwhile, Australia and New Zealand experienced a doubling of ransomware activity compared to the previous year. Small to medium-sized businesses, along with the healthcare and financial services sectors, bore the brunt of this increase. What is particularly notable in the ANZ context is the rising average ransom demand—an indicator of growing confidence among threat actors operating in the region.
In the Middle East and Africa, targeted campaigns were observed against critical infrastructure and energy networks—especially in the UAE and South Africa. The report highlights the role of groups such as Everest and RansomHub in these campaigns, often leveraging supply chain infiltration and zero-day exploits to bypass traditional perimeter defenses. The increased attention on MEA signals a growing trend of adversaries probing regions undergoing digital transformation, where security controls may still be unevenly deployed.
While the attack volume and intensity vary by region, the underlying trend is consistent: threat actors are adapting their operations based on regional infrastructure maturity, political climate, and sectoral exposure. In many cases, the regions experiencing the highest volume of attacks are also those with the most complex digital ecosystems—creating both opportunity and surface area for intrusion.
The Global Threat Landscape H1 2025 report offers an extensive, data-driven view of these regional shifts. From attack timelines and attribution trends to sector-specific breakdowns and threat actor movements, the regional analysis provides security leaders with a strategic lens to assess localized risk.
For multinational enterprises, this intelligence can be instrumental in understanding regional exposure, aligning detection and response strategies, and coordinating security investments across business units. For public sector stakeholders, it offers visibility into the intersection of cyber risk and national infrastructure. And for CISOs, it serves as a critical resource to support threat modeling, vendor management, and regional incident preparedness.
The full report is now available for download, providing actionable insights into how regional threat dynamics are likely to influence cybersecurity decisions in the months ahead.




















