Overview
Cyble’s vulnerability intelligence unit examined 30 vulnerabilities and 14 dark web exploit claims in recent reports to clients, and flagged eight of the vulnerabilities as meriting high-priority attention by security teams
Cyble said the eight vulnerabilities – found in products from Microsoft, VMware, Apple, Google, and others – “can lead to system compromise, data breaches, or full application control.”
The Top IT Vulnerabilities
Here are the eight vulnerabilities highlighted by Cyble in recent reports.
CVE-2025-2783 is a yet unrated vulnerability affecting Google Chrome on Windows prior to version 134.0.6998.177, where an incorrect handle provided in unspecified circumstances in Mojo allows a remote attacker to perform a sandbox escape via a malicious file. Researchers have reported that the vulnerability has been exploited to deploy malware in espionage attacks targeting Russian media outlets and education organizations.
CVE-2025-22230 is an authentication bypass vulnerability caused by improper access control in VMware Tools for Windows. A malicious actor with non-administrative privileges on a guest VM may gain the ability to perform certain high-privilege operations within that VM.
CVE-2025-26633 is a zero-day improper neutralization vulnerability in Microsoft Management Console that could allow an unauthorized attacker to bypass a security feature locally. Microsoft notes that the vulnerability has been exploited even though the attack complexity is high.
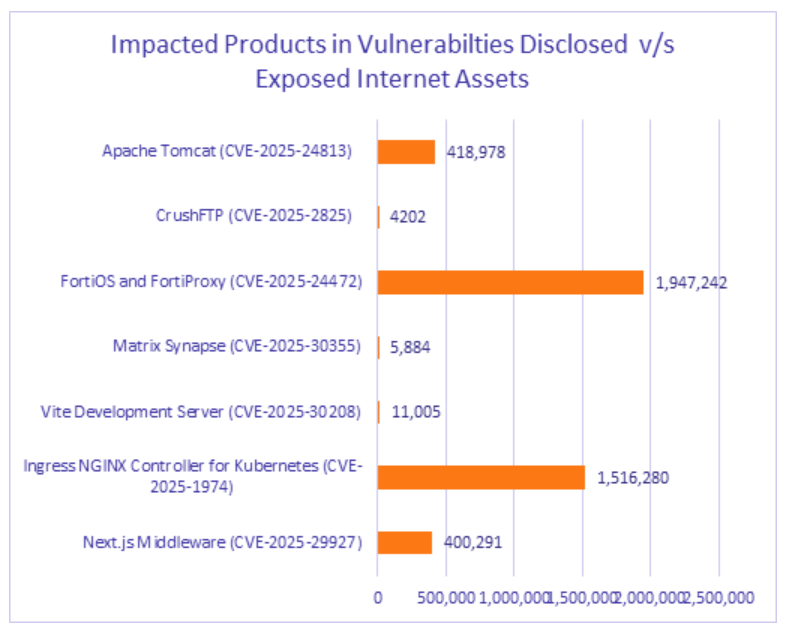
CVE-2025-29927 is a critical authorization bypass vulnerability affecting the Next.js framework, which is widely used for building web applications. The vulnerability allows attackers to bypass middleware-based authentication and authorization protections, potentially granting unauthorized access to sensitive areas of applications that utilize vulnerable versions of Next.js. Cyble observed the vulnerability under discussion by threat actors on underground forums, raising the likelihood that it could be exploited. Cyble detected more than 400,000 exposed Next.js instances (image below).
CVE-2025-23120 is a 9.9-severity vulnerability in Veeam Backup & Replication software. The vulnerability arises from a deserialization flaw in the .NET-based components of the software, specifically within the Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary classes. It could allow authenticated domain users to execute arbitrary code remotely, posing a significant risk to backup infrastructures.
CVE-2025-2825 is a 9.8-rated authentication bypass vulnerability affecting CrushFTP, a widely used enterprise file transfer solution. The vulnerability could allow remote, unauthenticated attackers to bypass authentication and gain unauthorized access to vulnerable CrushFTP servers without requiring valid credentials. In a note to clients, Cyble said, “This vulnerability is particularly concerning because it can be exploited remotely with low complexity, making it a high-priority security concern for organizations using CrushFTP.”
CVE-2025-24201 is an out-of-bounds write vulnerability in WebKit, the browser engine that powers Safari and all web browsers on iOS. The vulnerability could potentially impact any HTML parsers that use WebKit, including but not limited to Apple Safari and other browsers on iOS. The vulnerability was also added to CISA’s Known Exploited Vulnerabilities Catalog, indicating that it is actively being exploited in the wild.
CVE-2024-20439 is a critical vulnerability in the Cisco Smart Licensing Utility involving an undocumented, static user credential for an administrative account, which could allow an unauthenticated, remote attacker to log in to an affected system using these static credentials. Researchers have observed threat actors chaining CVE-2024-20439 with another critical vulnerability, CVE-2024-20440. This enables unauthenticated attackers to access sensitive log files containing API credentials by sending specially crafted HTTP requests to vulnerable devices and exploiting excessive verbosity in debug log files.
Cyble Recommendations
To protect against vulnerabilities and exploits, Cyble recommends that organizations implement the following best practices:
- Regularly update all software and hardware systems with the latest patches from official vendors.
- Develop a comprehensive patch management strategy that includes inventory management, patch assessment, testing, deployment, and verification. Automate the process where possible to ensure consistency and efficiency.
- Divide your network into distinct segments to isolate critical assets from less secure areas. Use firewalls, VLANs, and access controls to limit access and reduce the attack surface exposed to potential threats.
- Create and maintain an incident response plan that outlines procedures for detecting, responding to, and recovering from security incidents, including ransomware-resistant backups. Regularly test and update the plan to ensure its effectiveness and alignment with current threats.
- Implement comprehensive monitoring and logging solutions to detect and analyze suspicious activities. Use SIEM (Security Information and Event Management) systems to aggregate and correlate logs for real-time threat detection and response.
- Subscribe to security advisories and alerts from official vendors, CERTs, and other authoritative sources. Regularly review and assess the impact of these alerts on your systems and take appropriate actions.
- Conduct regular vulnerability assessment and penetration testing (VAPT) exercises to identify and remediate vulnerabilities in your systems. Complement these exercises with periodic security audits to ensure compliance with security policies and standards.
Conclusion
Actively exploited vulnerabilities – and those at high risk of exploitation – should be a top priority for security teams as they prioritize their patching efforts while also looking at other indicators of risk, such as web exposure and data and application sensitivity.
Implementing strong security practices is essential for protecting sensitive data and maintaining system integrity. A comprehensive attack surface management solution like Cyble can monitor for threats, vulnerabilities, and leaks specific to your environment, helping you harden cyber defenses and respond quickly to events before they become bigger incidents.
To access full IT vulnerability and other reports from Cyble, click here.




















