The FBI and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a well-timed advisory on the Medusa ransomware group last week, as Cyble has detected an acceleration in the group’s activities in recent months.
Medusa ransomware attacks have been a near-daily occurrence so far this year, running nearly 45% higher than the group’s 2024 attack levels, according to Cyble threat intelligence data.
The CISA-FBI advisory examines the Ransomware-as-a-Service (RaaS) group’s tactics, techniques, and procedures (TTPs), indicators of compromise (IoCs), MITRE ATT&CK Techniques, and more, based on recent FBI investigations.
Medusa Ransomware Attacks Surged in February
Cyble has recorded 60 Medusa ransomware victims in the first 72 days of 2025, on a pace for more than 300 attacks this year. That would be up substantially from the 211 Medusa ransomware attacks recorded by Cyble in 2024.
Attack volume peaked in February, with 33 victims claimed by the group in the 28-day month. February was a record month for ransomware attacks in general, as recorded by Cyble data.
Cyble has recorded 414 Medusa ransomware attacks in all, with just over half of the victims of the four-year-old RaaS group coming from the U.S. (image below).
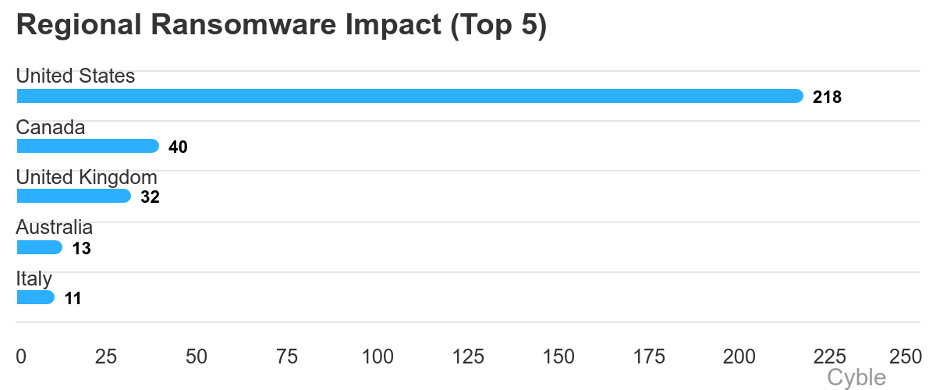
The group has shown a propensity for attacking critical infrastructure. Indeed, CISA and the FBI report that more than 300 of the group’s victims have come from critical infrastructure sectors such as medical, education, legal, insurance, technology, and manufacturing.
CISA-FBI Analysis of Medusa TTPs
Medusa was first identified in June 2021 and, according to the agencies, is unrelated to the MedusaLocker variant and the Medusa mobile malware variant.
Medusa developers recruit initial access brokers (IABs) in cybercrime forums and marketplaces for initial access to potential victims, paying between $100 and $1 million to affiliates, with the opportunity to work exclusively for Medusa. Phishing campaigns are a primary method for stealing credentials.
Unpatched vulnerabilities exploited by the group have included the ScreenConnect vulnerability CVE-2024-1709 and the Fortinet EMS SQL injection vulnerability CVE-2023-48788.
The agencies noted that the group uses living off the land (LOTL) and legitimate tools such as Advanced IP Scanner and SoftPerfect Network Scanner for initial user, system, and network enumeration.
Once presence in a victim network is established, commonly scanned ports include:
- 21 (FTP)
- 22 (SSH)
- 23 (Telnet)
- 80 (HTTP)
- 115 (SFTP)
- 443 (HTTPS)
- 1433 (SQL database)
- 3050 (Firebird database)
- 3128 (HTTP web proxy)
- 3306 (MySQL database)
- 3389 (RDP)
The group primarily uses PowerShell and the Windows Command Prompt (cmd.exe) for network and filesystem enumeration and to use Ingress Tool Transfer capabilities. The threat actors use Windows Management Instrumentation (WMI) to query system information.
Medusa uses PowerShell detection evasion techniques and the threat actors cover their tracks by deleting the PowerShell command line history. Certutil (certutil.exe) is used to avoid detection while performing file ingress.
The group frequently uses remote access tools such as AnyDesk, Atera, ConnectWise, eHorus, N-able, PDQ Deploy, PDQ Inventory, SimpleHelp, and Splashtop, perhaps varying based on tools used within the victim environment to avoid detection. Medusa uses the tools in combination with Remote Desktop Protocol (RDP) and PsExec for lateral movement and to identify files for exfiltration and encryption.
Among the Indicators of Compromise (IoCs) shared by the agencies were three file hashes:
| Medusa Indicators of Compromise (IoCs) | ||
| Files | Hash (MD5) | Description |
| !!!READ_ME_MEDUSA!!!.txt | Redacted | Ransom note file |
| openrdp.bat | 44370f5c977e415981febf7dbb87a85c | Allows incoming RDP and remote WMI connections |
| pu.exe | 80d852cd199ac923205b61658a9ec5bc | Reverse shell |
Ransomware Defenses Remain Critically Important
The FBI-CISA Medusa advisory underscores the importance of strong cybersecurity defenses and resilient architectures for stopping ransomware attacks – or minimizing any that may occur.
Basic cybersecurity practices that protect against ransomware can help an organization’s resilience in the face of any cyberattack.
Such practices include patching web-facing vulnerabilities that can be the starting point for an attack, training employees to recognize phishing and other attack attempts, and implementing zero trust, network segmentation and monitoring, and ransomware-resistant backups.




















