If we talk about the terminology “security”, then we can say that no company is 100% secure or even close to it. Just recently last week at the RSA security conference, it was mentioned that 99.9% of the Microsoft enterprise accounts that were being compromised by the cybercriminals lacks Multi-Factor Authentication (MFA).
Microsoft itself stated that on an average around 0.5% of its accounts get hacked every month, as it just recently happened in January which included the compromising of about 1.2 million number of accounts approximately. Taking note of the current situation and concerns, Alex Weinert the director of Identity Security said, “If you have an organisation of 10000 users, 50 of them are going to be compromised this month”.
Among the total of 480,000 compromised accounts, 40% of those accounts were breached via password spraying technique, in which the hackers tried breaking into the Microsoft accounts just by using some of the most commonly and frequently used passwords.
Since Jan 2020, Cyble researchers have uncovered over 13,000 unreported data breaches which have affected over 500 million accounts, which includes sensitive information such as PII, financial records and others. Cybercrime market is becoming prosperous with fresh players, from developers to affiliate networks, entering on a daily basis due to attractive economics behind it. The trend does not appear to slow down anytime soon. In one of its reports, Cyble evaluated and ranked the cyber risk exposure of the Australia stock exchange-listed Top 50 companies’ assessment, based on their traces, and mentions on the darkweb and deepweb. The report highlighted that the financial and banking sector, along with Energy, Utilities and Mining was at the most significant risk based on their information exposure in darkweb.
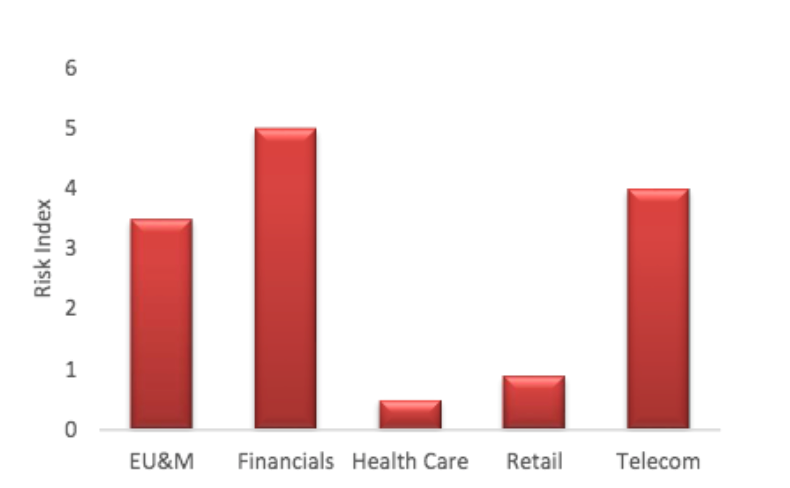
The graph from the Cyble Darkview Index Q3 2019- Download here
The above graph, which is from the Cyble Darkview index Q3 2019, indicates or represents the level of risk exposure of the different Australian business sectors. As identified by Cyble, the Financials sector is the one with the highest level of cyber risk exposure, which most often could be because of the financial motive and gains.
Due to the proliferation of data breach incidents, Cyble also launched its ‘freemium’ service called amibreched.com, where consumers, including enterprise, can perform free searchers to determine their exposure in darkweb and deepweb.
So, if we talk in simple terms, not using of MFA mechanism open the doors for hackers to enter the organisation and access the data by just knowing one valid password of one of their employees. Several threat actors’ groups have been using password spraying attacks on US organisations such as a recent report citing “Magnallium” group targeting US utility sector. Citrix Systems suffered a cyber-attack and perpetrators gained access to their sensitive data such as employee records, financial data etc. It is alleged that the hackers gained initial access to their systems through password spraying attacks.
When multi-factor authentication is implemented correctly, it is significantly more difficult for a cybercriminal to steal a complete set of credentials as the user has to prove they have physical access to a second factor that either they have (e.g. a physical token or software certificate) or are (e.g. a fingerprint or iris scan).
About Cyble:
Cyble Inc.’s mission is to provide organizations with a real-time view of their supply chain cyber threats and risks. Their SaaS-based solution powered by machine learning and human analysis provides organizations’ insights to cyber threats introduced by suppliers and enables them to respond to them faster and more efficiently.
Cyble strives to be a reliable partner/facilitator to its clients allowing them with unprecedented security scoring of suppliers through cyber intelligence sourced from open and closed channels such as OSINT, the dark web and deep web monitoring and passive scanning of internet presence. Furthermore, the intelligence clubbed with machine learning capabilities fused with human analysis also allows clients to gain real-time cyber threat intel and help build better and stronger resilience to cyber breaches and hacks. Due to the nature of the collected data, the company also offer threat intelligence capabilities out-of-box to their subscribers.





















