The current digital landscape necessitates an approach to sharing content on social media for significant user engagement and click-through rates. This is where the Open Graph Protocol (OGP) comes into play. Developed by Facebook, Open Graph allows web developers to control how their web pages appear when shared across various platforms. Developers use specific meta tags in a webpage’s HTML to define essential elements such as the title, description, and image that accompany shared links.
Attackers have long exploited the Open Graph Protocol for malicious activities. Recently, Cyble Research and Intelligence Labs (CRIL) also observed a threat actor on a Russian underground offering a toolkit dubbed ‘OG Spoof’ for similar operations. The toolkit was designed for phishing campaigns, aiming to mislead users and artificially inflate click-through rates by exploiting flaws in the Open Graph protocol.
Overview
The importance of Open Graph (OG) tags cannot be overstated. The OG tags enhance the visibility of content, making it appealing to a broader base of potential viewers and more likely to garner views and clicks.

Several content management systems (CMS), such as WordPress and Magento, come equipped with built-in functionalities or plugins that automatically generate these tags based on the post’s content. This automation ensures that when links are shared, they are presented in an engaging manner while accurately previewing their content.
The TA released the ‘OG Spoof’ kit for sale in October 2024 at a staggering USD 2,500 price and claimed that it was initially designed for their own fraudulent operations. However, as they developed advanced methods, the toolkit was released for sale exclusively to three buyers.
The toolkit leveraged Open Graph spoofing techniques, allowing attackers to manipulate the preview of web pages represented on social media platforms. This manipulation is executed through a convenient Telegram bot, which enables attackers to alter the metadata associated with URLs.
One of the toolkit’s key features was its ability to generate links—often shortened URLs—that appear to originate from trusted sources. This deceptive tactic exploits Open Graph metadata, making it easier for attackers to lure unsuspecting victims into clicking on harmful links.

Fraudulent links with preview sourced from the original domain (L), Original domain with preview (R)
OG Spoof’s Functionalities
Their toolkit featured four core functionalities:
Domain Management
- The toolkit integrates automatically with Cloudflare, allowing attackers to manage their domain settings, including DNS configurations, without manual intervention.
- Attackers can add new domains to the toolkit and monitor their real-time status, enabling continuous tracking of domain uptime and DNS health.
Advanced Link Spoofing
- The toolkit allows attackers to customize how their links appear when shared on social media.
- It enables the configuration of distinct URLs: one for displaying the preview (Open Graph metadata) and another for redirecting users after they click the first link.
- The toolkit includes an “Instant Update of Redirect” feature, allowing attackers to quickly change the destination of a link without altering the shared URL. This capability lets them modify links in real-time based on user engagement or detection efforts by social media platforms.
Integration with Advertising Systems
- The toolkit is designed to seamlessly interface with X Ads (formerly Twitter) and can also be easily integrated with Facebook Ads, Google Ads, Telegram, and any other platform that supports the Open Graph Protocol.
Team Management
- The toolkit supports multiple users and provides analytics for each link created by individual users, indicating its suitability for fraudulent groups with several members.
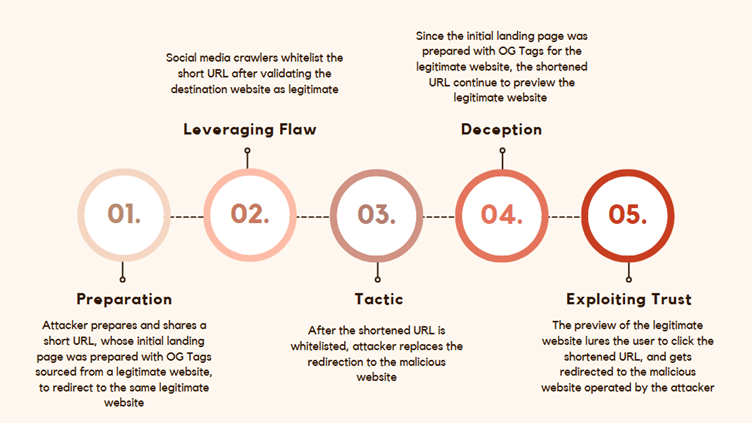
Toolkit’s Mode of Operation
- The TA claimed that the toolkit leverages a vulnerability in the Open Graph Protocol to bypass moderation checks (security checks).
- Apparently, social media platforms typically moderate content based on its source and metadata, and if the toolkit can make the link appear as if it comes directly from an original resource, it may evade scrutiny and be approved for sharing without raising red flags.
- This is possibly done by leveraging an alleged flaw that once the link is approved and shared, any subsequent changes made by the attacker (like altering where the link redirects) do not trigger additional moderation or security checks. This means that after initial approval, they can modify the destination of the link without having to go through moderation again, allowing them to redirect users to potentially harmful or misleading content.
- This means that the attacker could initially direct users to legitimate domains but switch to a malicious domain later without needing new approvals.
A flow chart explaining the likely mode of operation of the toolkit follows:
Conclusion
The OG Spoof toolkit featured simple techniques to support sophisticated operations that manipulate technological flaws and employ tactics to create initial trust and foster a false sense of security, ultimately leading victims to be deceived.
Such ready-made toolkits lower the barrier to entry, attracting both proficient and new actors seeking financial gain through these tactics. Such kits also simplify spear-phishing, a key initial attack vector used by Advanced Persistent Threat (APT) groups to deliver malware. Moreover, with the rise of cryptocurrency scams and fraudulent activity on platforms like X (formerly Twitter), including schemes involving high-profile accounts and fake giveaways, these toolkits are likely to be leveraged in such campaigns, making caution paramount.




















