Overview
According to an analysis of Cyble threat intelligence data, U.S. ransomware attacks have surged to the start of 2025, up nearly 150% from the first five weeks of 2024.
Ransomware attacks on U.S. targets have been climbing since a few organizations paid ransoms to attackers in highly publicized cases last year, making the country a more attractive target for ransomware groups.
That’s likely the main reason for the increase. Regardless of the timeframe or changes in the most active ransomware groups, U.S. ransomware attacks have increased substantially in the last year and have been climbing steadily since the fall.
We’ll examine the changing ransomware landscape in the U.S. and other frequently attacked countries and consider what changes may be in store as we approach 2025.
The Effect of Ransomware Payments
In the first five weeks of 2024, Cyble documented 152 ransomware attacks on U.S. targets, in line with late 2023 trends.
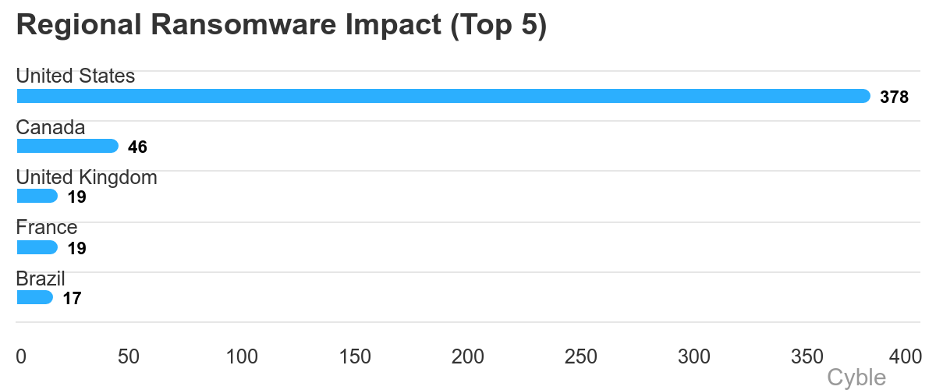
In the first five weeks of 2025, that number soared to 378 attacks on U.S. targets, a 149% year-over-year increase. Compared to the end of 2024, attacks are up a still significant 29% so far in 2025, up from 282 in the last five weeks of the year.
Perhaps owing to geographical proximity, Canada has also seen a significant increase in ransomware attacks, up from 14 in the year-ago period to 28 at the end of 2024, and nearly doubling again to 46 to start 2025.
Even as North American ransomware attacks have soared, the next-most attacked regions have stayed relatively stable. France, for example, had 18 attacks to start in 2024 and has seen 19 thus far in 2025 (chart below).
The North American trend has held even as the most active ransomware groups have changed. LockBit was the most active ransomware group at the start of 2024, then RansomHub took over after LockBit was interrupted by law enforcement actions. This year CL0P and Akira have been the most active groups in the U.S., as RansomHub has slipped back to number 5 (image below). With LockBit planning a comeback, the most active groups will likely change further in the months ahead.

The Most Attacked Sectors in the U.S.
Ransomware targets in the U.S. thus far in 2025 have been a mix of opportunity and reward.
Sectors traditionally lagging in cybersecurity, such as construction, professional services and healthcare, have been hit hard. But information technology (IT) companies also appear high on the list of exploited sectors, as the potential reach of IT companies, including the possibility of software supply chain attacks, can attract motivated hackers.
On the other end of the attack spectrum, only 10 attacks on a rich target like banking and financial services suggest that the finance sector may be doing better than most at cybersecurity. Indeed, the industry is a leading adapter of cyber threat intelligence platforms like Cyble.
Below are ransomware attacks in the U.S. by sector thus far in 2025.
| 2025 Ransomware Surge (source: Cyble) | |
| Sector | Number of attacks |
| Construction | 50 |
| Professional Services | 47 |
| Healthcare | 33 |
| Manufacturing | 31 |
| IT and IT services | 29 |
| Transportation | 24 |
| Consumer Goods | 22 |
| Food and Beverages | 22 |
| Education | 18 |
| Real Estate | 11 |
| Technology | 11 |
| Banking and Finance | 10 |
| Energy and Utilities | 10 |
| Automotive | 9 |
| Agriculture | 8 |
| Retail | 8 |
| Hospitality | 7 |
| Pharma and Biotech | 7 |
| Nonprofit | 5 |
| Telecom | 4 |
| Aerospace and Defense | 3 |
| Chemicals | 3 |
| Government | 3 |
| Media and Entertainment | 2 |
| Mining | 1 |
A Growing Refusal to Pay Ransoms
One bit of good news recently came from blockchain intelligence company Chainalysis, which reported that ransomware payments fell by 35% last year, due to law enforcement actions and “a growing refusal by victims to pay.”
It would be good news if that trend continues, but whether it’s enough to overcome some widely publicized ransom payments made by U.S. organizations remains to be seen.
Regardless of ransom payment trends, ransomware attacks are here to stay. Organizations should tap into the power of advanced cybersecurity tools like Cyble and implement cybersecurity best practices such as zero trust, risk-based vulnerability management, segmentation, tamper-proof backups, and network and endpoint monitoring. Getting the basics right can go a long way toward reducing risk and limiting any cyberattacks that do occur.





















