Recently, Cyble Research Team identified and verified a database leak of WeLeakData, which comes in the list of one of the largest database leaks and cracking communities operating since 2019.
Sample advertisement of the group on another cybercrime forum:
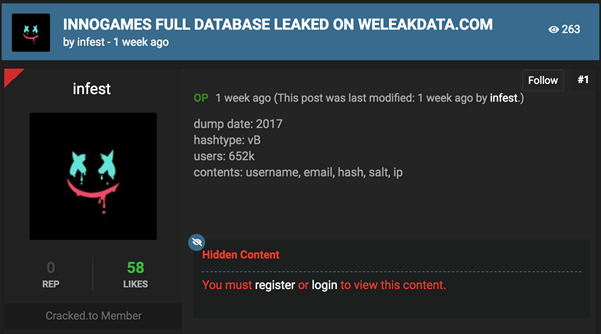
Earlier in January this year, the site was brought offline for unknown reasons – there are public reports which claim it was seized by the Federal Bureau of Investigations (FBI). The claims are unsupported – Cyble researchers got the intelligence from the members of the forum that it was not the case though. The reputation of the forum is undoubtedly there and is seen as a competitor to RaidForums. The business model of the forum was quite straightforward- it was mainly a criminal forum that specializes in the trade of leaked databases and uses the third-party e-commerce platform Shoppy for membership upgrades.

Cyble researchers have explored the group in the past, and it seemed to be quite well managed. Their admin and moderators have strong ties to several hacking groups and data brokers, which spiked their group’s reputation and the number of members. Several members of other hacking forums expressed their desires to hack WeLeakData due to various reasons such as here:-

After a brief time of being offline, allegedly, the site was sold to a new member of the forum, and came back online. Around the same time, we noticed a new fork cracking site – leaksmarket.com which was strikingly the same site (operated by a new actor with no credibility), with all the same content.

It was clear to us by then, the original WeLeakData database has been compromised, or the original owner has decided to re-brand it. However, when they came back online in April, the second hypothesis got nulled, and we then had a high degree of the confidence level of a data breach, at one of the largest cracking communities itself.
Our researchers looking into more details, and noticed certain members, with low or no reputation selling it such as below:
On April 2020, Cyble researchers managed to gain access to the WeLeakData.com database from a darkweb market seller and identified several interesting aspects from the database file.


The database includes interesting information of its members, who are mostly researchers, hackers, cybercriminals and crackers.
- Username
- Password
- Private Messages
- IP addresses
Here are some sample conversations:


There are unconfirmed reports in the darkweb market that WeLeakData.com owner has been arrested as part of the Europol’s recent crackdowns. Cyble researchers have verified the alias of WeLeakData owner is unresponsive and unreachable, however, the arrest claim is unverified at the time of writing this. Several cybercrime operators have mentioned that their operations have been disrupted due to the crackdown. However, Cyble is also observing new players entering as well.
Regardless, this is one of the interesting developments in the cybercrime market. Weleakdata is now offline.
Cyble has indexed the entire database of WeLeakData.com at their data breach monitoring and notification platform, amibreached.com
About Cyble:
Cyble Inc.’s mission is to provide organizations with a real-time view of their supply chain cyber threats and risks. Their SaaS-based solution powered by machine learning and human analysis provides organizations’ insights to cyber threats introduced by suppliers and enables them to respond to them faster and more efficiently.
Cyble strives to be a reliable partner/facilitator to its clients allowing them with unprecedented security scoring of suppliers through cyber intelligence sourced from open and closed channels such as OSINT, the dark web and deep web monitoring and passive scanning of internet presence. Furthermore, the intelligence clubbed with machine learning capabilities fused with human analysis also allows clients to gain real-time cyber threat intel and help build better and stronger resilience to cyber breaches and hacks. Due to the nature of the collected data, the company also offer threat intelligence capabilities out-of-box to their subscribers.




















