Industry-Leading
Cloud Infrastructure Entitlement Management (CIEM)
Cyble’s CIEM solution delivers complete visibility and control over identity permissions across cloud environments. It identifies excessive privileges, uncovers risky access paths, and enforces least-privilege policies to prevent unauthorized access and identity-driven breaches.
Integrated with Cyble Vision and Cyble Hawk, the Identity service strengthens cloud identity security with continuous entitlement monitoring and automated governance.
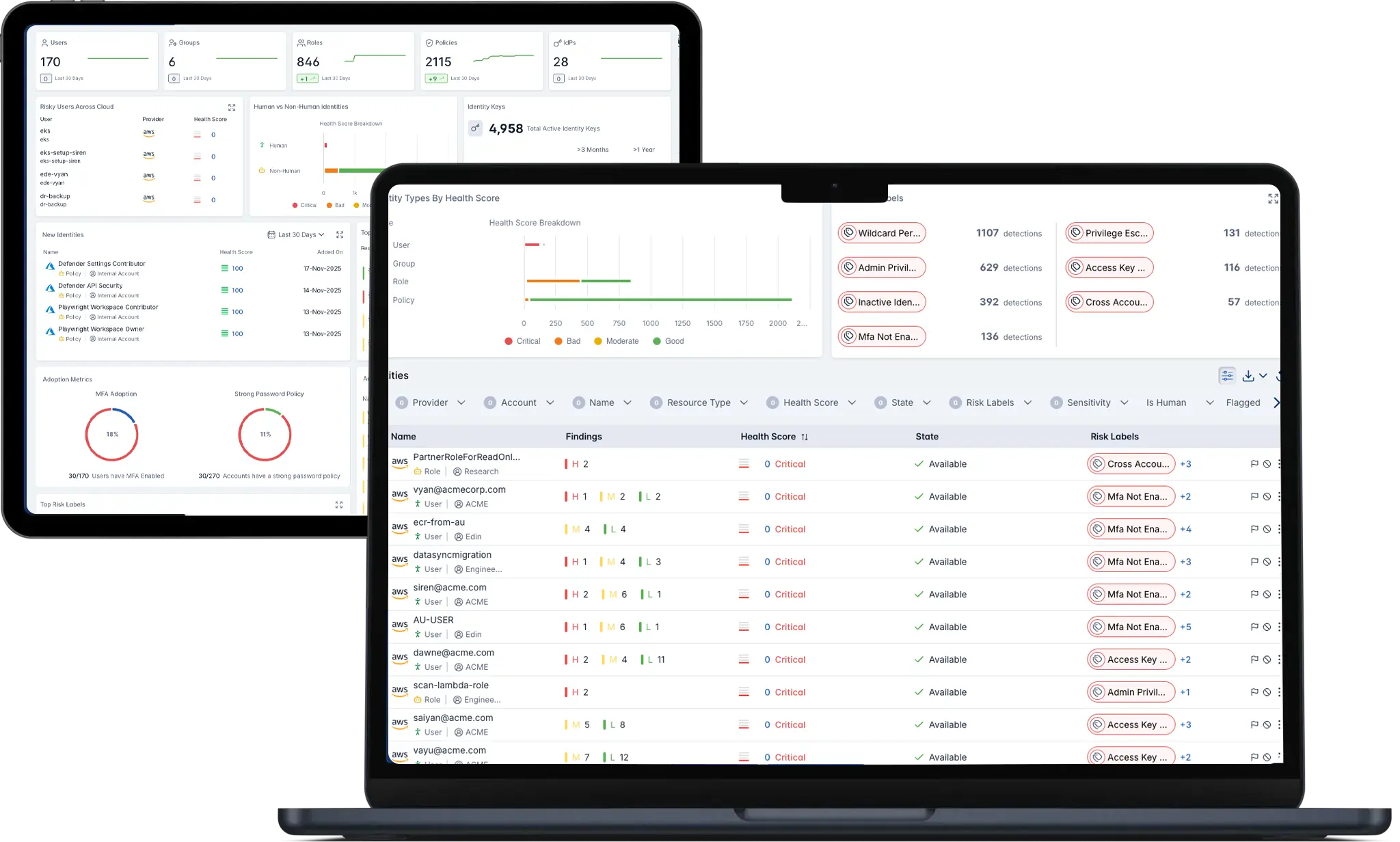
What is Cyble CIEM ?
See Every Identity. Control Every Permission.
Cyble CIEM service goes beyond visibility — it gives organizations the power to govern every identity, permission, and access path across multi-cloud environments. The platform uncovers privilege misuse, closes hidden access gaps, and prevents identity-driven attacks long before they escalate.
Core Features & Capabilities
Identity & Entitlement Discovery
Real-time visibility into all users, service accounts, roles, and permissions across multi-cloud environments.
Privilege & Permission Analysis
Detect over-privileged identities, unused permissions, and privilege-escalation paths.
Least-Privilege Enforcement
Automated, context-based recommendations to right-size permissions and reduce access risk.
Access Anomaly Detection
Spot unusual activity, unauthorized access attempts, and suspicious identity behavior instantly.
Compliance Support
Continuous entitlement auditing aligned with GDPR, HIPAA, SOC 2, and other regulatory frameworks.
Multi-Cloud Compatibility
Unified identity governance across AWS, Azure, GCP, and hybrid cloud environments.
Why Choose Cyble CIEM?
Full Identity Visibility
A consolidated view of every cloud identity and its access relationships.
Automated Access Governance
Continuous mapping and evaluation of entitlements to simplify oversight.
Risk-Driven Privilege Insights
Prioritized findings that help security teams eliminate high-risk permissions first.
Real-Time Identity Alerts
Immediate notifications for suspicious or unauthorized access activity.
Unified with Cyble Vision & Cyble Hawk
Threat detection and identity governance from one integrated platform.
Cyble CIEM Workflow
See the Risks. Fix the Gaps. Secure the Access.
Discover & Map Identities
- Identify every cloud user, service account, and permission.
- Surface hidden or unused entitlements before they become attack paths.
Analyze & Prioritize Risks
- Detect excessive, outdated, or misconfigured privileges.
- Identify privilege-escalation paths and shadow identities.
Enforce Least Privilege
- Apply automated, context-aware permission recommendations.
- Reduce the identity attack surface consistently across clouds.
Detect & Respond Instantly
- Flag unauthorized access attempts, anomalies, and risky behavior.
- Act fast with integrated alerts through Cyble Vision and Cyble Hawk.
FAQs
What is the difference between CIEM and CSPM?
CIEM and CSPM address two different layers of cloud security. CSPM focuses on securing cloud configurations, while CIEM focuses on managing identities and permissions, making it a critical part of modern CIEM in cyber security and overall cloud posture management. CSPM protects cloud infrastructure; CIEM protects who can access that infrastructure. Both together strengthen an organization’s CIEM cloud security strategy.
What are the main CIEM components?
Why is CIEM important for cloud security?
What types of permission risks can CIEM detect?
When should an organization adopt CIEM?
Secure Your Cloud Identities with Cyble CIEM
Gain control over permissions, reduce identity attack surfaces, and enforce consistent access policies across your cloud environments.
Ready to strengthen your cloud identity security?

