Industry-Leading
Cyble Cloud Security Posture Management (CSPM)
Secure Your Cloud. Master Your Posture.
Cloud environments bring agility and scale—but they also introduce new risks and blind spots. Cyble’s Cloud Security Posture Management (CSPM) solution delivers continuous visibility, governance, and protection across your entire cloud infrastructure. As one of the leading Cloud Security Posture Management companies, Cyble helps you detect misconfigurations, maintain compliance, and defend cloud workloads with precision.
Take control. Reduce risk. Stay compliant with confidence.
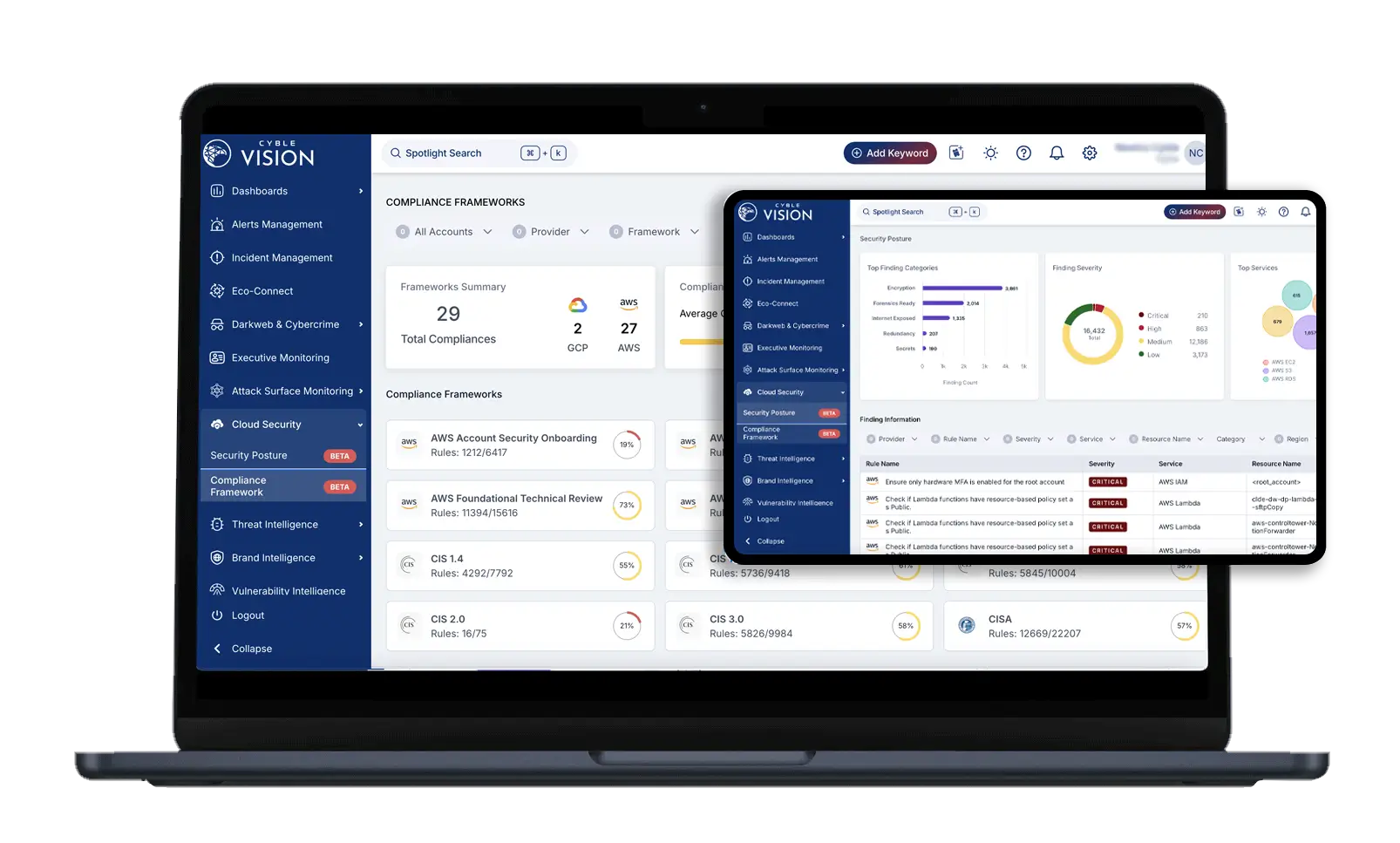
What is CSPM?
Real-Time Cloud Asset Visibility. Unified Governance. Automated Remediation.
Cyble’s CSPM solution monitors your cloud environment in real time, identifying misconfigurations, vulnerabilities, and policy drift. It empowers teams to maintain a strong security posture across complex, multi-cloud ecosystems. With Cyble’s advanced Cloud Security Posture Management tools, your team gains the automation, clarity, and control required to stay ahead of cloud risks.
Core Features & Capabilities
Comprehensive Cloud Visibility
Identify and map all cloud assets across providers, giving you real-time insight into resources, workloads, and configurations—essential for modern Cloud Security Posture Management solutions.
Continuous Compliance Monitoring
Automatically assess configurations against regulatory and industry frameworks such as GDPR, HIPAA, and PCI-DSS with audit-ready reporting.
Misconfiguration Detection & Prioritization
Detect risky cloud settings (public buckets, overly permissive IAM roles, unsafe network rules) and prioritize remediation using intelligence-backed risk scoring.
Agentless Multi-Cloud Support
Cyble, one of the trusted CSPM vendors, supports agentless deployment across multiple cloud providers, ensuring fast onboarding and effortless scaling.
Integration & Automation
Integrate with CI/CD pipelines, cloud APIs, ticketing systems, SIEM/SOAR platforms, and more—turning your CSPM into a fully automated cloud governance engine.
Why Choose Cyble CSPM
Proactive Risk Reduction
Cyble’s CSPM tools provide continuous risk monitoring and early detection—helping you prevent misconfiguration-driven breaches.
Simplified Compliance & Governance
Built-in controls, policy mapping, and automated reporting streamline the compliance lifecycle for audits, assessments, and certifications.
Scalable for Cloud-First Enterprises
Whether you operate across AWS, Azure, GCP, hybrid, or multi-cloud setups—Cyble’s CSPM solution scales smoothly with your environment.
Unified Cloud Governance
Gain a single, consolidated view of cloud assets, risks, compliance posture, and remediation activities—all in one intelligent dashboard.
How It Works
How You Stay Protected
Discover
Assess
Prioritize
Remediate
Report
Industry Use Cases & Customer Impact
How Our Solutions Work for You
Technology & SaaS
Financial Services
Healthcare & Life Sciences
Manufacturing & Critical Infrastructure
Public Sector & Government
“Cyble’s CSPM made our cloud audits faster and more accurate. We now have full confidence in our security posture.”
- Cloud Security Manager, Global SaaS Provider
FAQs
What is the difference between CSPM and SIEM?
CSPM (Cloud Security Posture Management) focuses on identifying and managing cloud misconfigurations, compliance risks, and visibility gaps across cloud environments. It ensures that cloud resources follow best practices, security baselines, and regulatory frameworks.
SIEM (Security Information and Event Management), on the other hand, collects and correlates security logs from various systems (including cloud, endpoints, network devices, and applications) to detect threats, anomalies, and security incidents in real time.
Key difference:
- CSPM = Preventive, configuration-focused
- SIEM = Detective, event/log-focused
CSPM strengthens cloud posture, while SIEM centralizes monitoring and incident detection.
What features should a CSPM tool have?
A strong CSPM solution should include:
- Continuous cloud posture assessment
- Automated misconfiguration detection & remediation
- Compliance monitoring (e.g., CIS, GDPR, SOC 2, ISO 27001, PCI-DSS)
- Visibility across multi-cloud infrastructures (AWS, Azure, GCP)
- Identity & permission analysis (IAM security)
- Threat detection powered by AI/ML
- Risk scoring and prioritization
- Integration with DevOps pipelines (shift-left security)
- Alerting & reporting dashboards
- Mapping cloud assets and relationships
These capabilities ensure proactive cloud security management.
How does CSPM improve cloud security?
CSPM improves cloud security through:
- Identifying and fixing misconfigurations before attackers exploit them
- Enforcing consistent policies across all cloud environments
- Providing visibility into cloud assets, identities, and data flows
- Automating security checks so teams catch issues early
- Maintaining compliance with industry regulations
- Reducing risk exposure by prioritizing vulnerabilities and configuration gaps
By continuously monitoring cloud posture, CSPM minimizes the likelihood of cloud-based breaches and improves overall resilience.
Can CSPM detect misconfigurations?
Yes — detecting misconfigurations is one of the core functions of CSPM.
CSPM tools identify incorrect, risky, or non-compliant cloud configurations such as:
- Publicly exposed storage buckets
- Over-permissive IAM roles
- Unencrypted data stores
- Misconfigured security groups
- Disabled logging or monitoring
- Missing MFA on accounts
CSPM not only detects these issues but can also automate remediation or guide teams on how to correct them.
Which industries need CSPM most?
Industries that rely heavily on cloud infrastructure benefit most from CSPM, especially:
- Financial services & fintech
- Healthcare & life sciences
- E-commerce & retail
- Technology & SaaS companies
- Government & public sector
- Telecommunications
- Manufacturing & industrial IoT
Any organization storing sensitive data or operating in regulated environments requires strong cloud security posture management.
Can CSPM stop data breaches?
CSPM reduces the risk of data breaches but does not eliminate them entirely.
It helps prevent breaches by:
- Closing misconfigurations attackers commonly exploit
- Enforcing encryption and access control standards
- Maintaining compliance
- Providing visibility into cloud risk
- Detecting anomalies and policy violations
While CSPM cannot stop every threat (like insider attacks or sophisticated zero-days), it significantly lowers the attack surface, making breaches far less likely.
How to choose the right CSPM platform?
When selecting a CSPM platform, evaluate:
- Multi-cloud support (AWS, Azure, GCP)
- Depth of AI-driven detection & automation
- Breadth of compliance frameworks
- Ease of deployment and scalability
- Integration with CI/CD pipelines and DevOps tools
- Quality of dashboards, reporting, and visibility
- Accuracy of misconfiguration detection
- Remediation workflows (auto or guided)
- Identity and access risk analysis
- Vendor reputation, support, and expertise
A strong CSPM platform should offer continuous monitoring, intelligent risk prioritization, and automated remediation to maintain a secure cloud environment.
Trusted by Global Leaders in Cybersecurity
From Fortune 500s,to government organizations, leading teams rely on Cyble’s solutions to detect, respond, and stay ahead of evolving threats.
IT Manager – Miscellaneous

Cyber Security Operations Manager – Miscellaneous

CISO – Manufacturing

Deputy General Manager – Consumer Goods

Director of Engineering – IT Services

Manager of IT Services – IT Services

Resources

Cloud Security Posture Management (CSPM)
Data Sheets

