Read Cyble’s take on the notorious RansomHub ransomware group, exposing its modus operandi and attack methods.
RansomHub, one of the most prolific ransomware groups, has quickly captured the attention of cybersecurity experts and industry professionals alike. First identified in February 2024, RansomHub is believed to be the successor or evolution of the notorious Knight ransomware group.
With its technical advanced operations and apparent ties to former affiliates of the ALPHV ransomware group, RansomHub’s presence marks an escalation in the ransomware collectives. Operating under the increasingly popular Ransomware-as-a-Service (RaaS) model, the group has been recognized for its advanced methods and an innovative affiliate prepayment model that sets it apart from other ransomware operations.
The RansomHub group is based upon the foundations laid by older ransomware groups, particularly Knight and ALPHV. The group’s rapid growth can largely be attributed to its implementation of a prepayment system for affiliates. Unlike many other ransomware groups that operate on a revenue-sharing model, where affiliates only pay a percentage of the ransom, RansomHub requires affiliates to pay upfront to join the operation. This approach ensures the group’s financial security while incentivizing affiliates to carry out attacks on their behalf, using RansomHub’s tools and infrastructure in exchange for a share of the profits.

Countries Targeted by the RansomHub Group (Source: Cyble Vision)
The group’s operations span across the globe, targeting high-value organizations in multiple sectors, including aerospace and defense, energy, healthcare, government, telecommunications, pharmaceuticals, and financial services. Their flexibility in selecting targets, from small enterprises to multinational corporations, has helped them maximize the potential for large ransom payouts, further strengthening its reputation within the criminal ecosystem.
Tactics, Techniques, and Procedures (TTPs)
RansomHub’s operational tactics and techniques are highly methodical and deliberate. They employ a range of tools and procedures designed to maximize the impact of its attacks while minimizing the risk of detection.

Cyble Vision Threat Library (Source: Cyble Vision)
The group’s operations typically follow a multi-stage process that begins with gaining initial access to a network, followed by exploiting vulnerabilities, executing commands, maintaining persistence, and eventually encrypting or exfiltrating valuable data. This approach is similar to a surgical strike, where each move is calculated to ensure maximum impact.
Initial Access: Exploiting Vulnerabilities
RansomHub’s attacks begin with an essential phase: gaining initial access. One of the group’s primary techniques is the exploitation of well-known vulnerabilities in public-facing applications. The group has particularly exploited the Zerologon vulnerability, identified as CVE-2020-1472. This vulnerability, which affects Windows Servers, allows attackers to bypass security measures and take control of domain controllers, thereby giving them full access to an organization’s network. By exploiting Zerologon, RansomHub can infiltrate even well-defended systems, making it an effective entry point for its operations.
In addition to Zerologon, RansomHub’s affiliates use phishing (T1566) as another method to gain initial access. Phishing emails, often crafted to appear as legitimate communication from trusted sources, may contain malicious attachments or links that lead to system compromise. These emails are highly personalized, increasing the likelihood that the victim will fall for the ruse. Spear-phishing, a more targeted form of phishing, is also a common tool in RansomHub’s arsenal.
Execution: Lateral Movement and Command Execution
Once inside a network, RansomHub moves quickly to execute its attack, often leveraging tools and techniques to escalate privileges and spread laterally across the compromised environment. A key technique used during this phase is the abuse of Windows Management Instrumentation (WMI) (T1047). WMI allows attackers to remotely execute commands on local and remote systems, facilitating the lateral movement of malware throughout the network. This technique enables RansomHub’s affiliates to gather valuable system information, deploy ransomware, and maintain a foothold within the environment.
PowerShell (T1059.001) is another tool frequently used by RansomHub for executing malicious commands and scripts. PowerShell is a versatile command-line interface that enables attackers to run various operations, including running encrypted payloads and disabling security measures, all while avoiding detection.
Persistence: Maintaining a Footprint
To ensure that they maintain access to compromised systems, RansomHub employs persistence techniques that help them maintain control over networks even if the initial breach is detected. One such method is account manipulation (T1098), in which the attackers modify or create new user accounts to maintain access. In addition, they may elevate privileges by exploiting vulnerabilities in the system, allowing them to create additional backdoors or access points for future attacks.
The persistence techniques used by RansomHub are also designed to minimize the chances of being discovered. By creating new accounts or manipulating existing ones, the attackers can remain hidden and continue their perations without raising suspicions.
Privilege Escalation: Gaining Control
RansomHub is also adept at escalating privileges within a network. Privilege escalation techniques, such as exploiting vulnerabilities (T1068) in operating systems or applications, are key components of the group’s attack lifecycle. By exploiting these vulnerabilities, RansomHub’s actors can gain administrative-level access to systems, allowing them to execute its ransomware payloads on critical systems, further crippling the targeted organization’s operations.
The ability to escalate privileges also enables RansomHub to disable security tools, move laterally within networks, and encrypt data on critical systems. This increased level of access ensures that the attackers can successfully carry out their operations without interference.
Defense Evasion: Hiding from Detection
Evading detection is an essential aspect of RansomHub’s operational success. The group uses a variety of defense evasion techniques to mask their activities and avoid triggering security alarms. For instance, masquerading (T1036) involves altering the names, metadata, or attributes of files to make them appear legitimate. This makes it more difficult for security software to detect malicious activity, allowing the attackers to continue their operations without interference.
RansomHub is also known to use indicator removal (T1070), a technique that involves deleting or modifying logs and traces of its presence within the system. By erasing evidence of its attack, the group can delay the detection and remediation process, extending its control over the compromised network.
Additionally, the attackers may disable security tools such as antivirus software (T1562.001), making it even more difficult for administrators to identify and stop its activities. This combination of tactics allows RansomHub to evade detection for long periods, which significantly increases the damage caused by its attacks.
Credential Access and Exfiltration
Credential theft is another key aspect of RansomHub’s approach to ransomware attacks. By conducting OS credential dumping (T1003), RansomHub’s affiliates can extract sensitive credentials, including password hashes and clear-text passwords, from compromised systems. These stolen credentials can then be used to escalate privileges, move laterally across networks, or access additional systems.
In addition to encrypting data, RansomHub also employs a data exfiltration tactic. By stealing sensitive information, such as financial documents, client data, or intellectual property, RansomHub can pressure organizations into paying a ransom to prevent the public release of this information. The threat of exposing confidential data amplifies the urgency of the ransom demand, often pushing victims to pay quickly to avoid reputational damage.
Industry Impact and Targeted Sectors
RansomHub’s attacks have affected a wide range of industries, with a particular focus on sectors that rely heavily on sensitive data and IT infrastructure. Some of the most common industries targeted by RansomHub include aerospace and defense, energy, healthcare, government agencies, law enforcement, telecommunications, pharmaceuticals, and manufacturing. The group’s ability to identify high-value targets and exploit critical vulnerabilities has made them one of the most prolific ransomware groups in operation today.
Conclusion
RansomHub is a malicious ransomware group that operates under a Ransomware-as-a-Service (RaaS) model. Their innovative affiliate prepayment system, combined with their use of advanced attack techniques and the exploitation of critical vulnerabilities like Zerologon, has allowed them to rapidly gain prominence in the ransomware domain. Its tactics, including encryption, data exfiltration, and the threat of releasing sensitive information, have made them a formidable adversary for organizations worldwide.
Cyble, with its AI-driven threat intelligence platform, helps organizations stay protected from such threats. By continuously monitoring cybercriminal activities and vulnerabilities, Cyble empowers businesses to detect and respond effectively to ransomware groups like RansomHub, strengthening cybersecurity defenses.
Recommendation and Mitigation Techniques
Here are several recommendations to mitigate the risks posed by RansomHub and similar ransomware groups:
-
- Regular Patching and System Updates: Regularly patch all systems and software, especially vulnerabilities like Zerologon (CVE-2020-1472). Use automated patch management tools to ensure that critical patches are deployed swiftly across the network.
-
- Employee Training and Phishing Awareness: Train employees to recognize phishing attempts and suspicious emails through simulated phishing exercises. Implement clear guidelines on how to handle potential threats, such as verifying email addresses or reporting anomalies.
-
- Implement Multi-Factor Authentication (MFA): Enforce MFA for all users accessing critical systems and sensitive data, especially for remote access and administrative accounts.
-
- Comprehensive Backup and Recovery Systems: Maintain regular, secure, and up-to-date backups in air-gapped or offline environments. Test these backups to ensure they can be quickly restored during an attack.
-
- Continuous Network Monitoring: Deploy advanced threat detection systems such as SIEM (Security Information and Event Management) tools and behavioral analytics to continuously monitor networks for suspicious activity.
-
- Enforce Least Privilege and Access Control: Apply the principle of least privilege (PoLP) to limit user access to critical systems based on job roles. Regularly review access rights and implement privileged access management (PAM).
MITRE attack Techniques Associated with the RansomHub Group
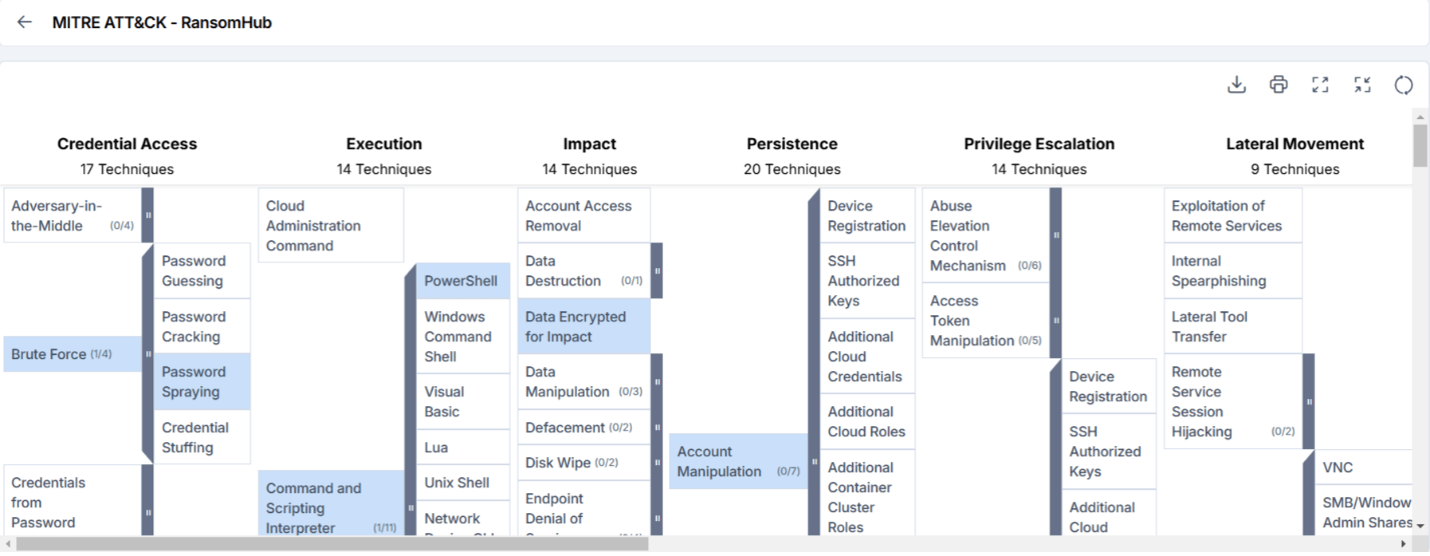
MITRE ATT&CK (Source: Cyble Vision)
-
- Exploit Public-Facing Application (T1190): Exploiting weaknesses in internet-facing applications (e.g., websites, databases) can provide an adversary with initial access. Vulnerabilities in cloud environments can also be leveraged.
-
- Phishing (T1566): Sending malicious emails or using social engineering via platforms like social media to deceive victims into executing harmful code or revealing credentials.
-
- Windows Management Instrumentation (T1047): Adversaries can use WMI to execute commands remotely or locally, enabling lateral movement and data gathering.
-
- PowerShell (T1059.001): PowerShell commands and scripts are used for executing malicious code, downloading additional payloads, and performing administrative tasks on compromised systems.
-
- Account Manipulation (T1098): Modifying account credentials or permissions ensures continued access to systems and potentially elevates privileges.
-
- Create Account (T1136): Creating new accounts, locally or within domains, establishes persistence without relying on remote access tools.
-
- Exploitation for Privilege Escalation (T1068): Exploit vulnerabilities in software to escalate user privileges from normal user to administrative or system-level access.
-
- Account Manipulation (T1098): Modifying accounts to grant higher privileges can help adversaries escalate their access within the network.










