Cyble showcases its findings on Sofacy, a notorious APT group, and the tactics, targets, tools, and techniques it uses in its cyber espionage activities.
Sofacy, identified by a July 2018 U.S. Department of Justice indictment as being linked to Russia’s Main Intelligence Directorate of the General Staff, is a notable threat group. This group is infamous for compromising the Hillary Clinton campaign, the Democratic National Committee, and the Democratic Congressional Campaign Committee in 2016 with the intent to meddle in the U.S. presidential election. Active since at least 2008, Sofacy has been a persistent and formidable player in the cyber espionage landscape.
Sofacy has been identified orchestrating multiple simultaneous cyberespionage campaigns, underscoring its significant resources and funding. It frequently employs typosquatted domains mimicking legitimate organizations. These typosquatted domains are then used to create email accounts used for phishing, credential harvesting, and other malicious activities, showcasing its sophisticated and well-coordinated efforts.
In its initial campaigns, Sofacy utilized various tactics, including spear-phishing emails and credential harvesting via deceptive websites. As defenses evolved, their campaigns became increasingly sophisticated. Their primary implant, XAgent, has been adapted for multiple operating systems, targeting both standard computers and smartphones, reflecting their advanced and adaptive cyberespionage capabilities.
The Sofacy group has been implicated in a series of cyber assaults on various high-profile targets, including the German and Norwegian parliaments, TV5Monde in France, the White House, NATO, the Democratic National Committee, and the Organization for Security and Co-operation in Europe. They also allegedly targeted the campaign of French presidential candidate Emmanuel Macron. In 2018, a United States Special Counsel indictment identified Fancy Bear as GRU Unit 261651.
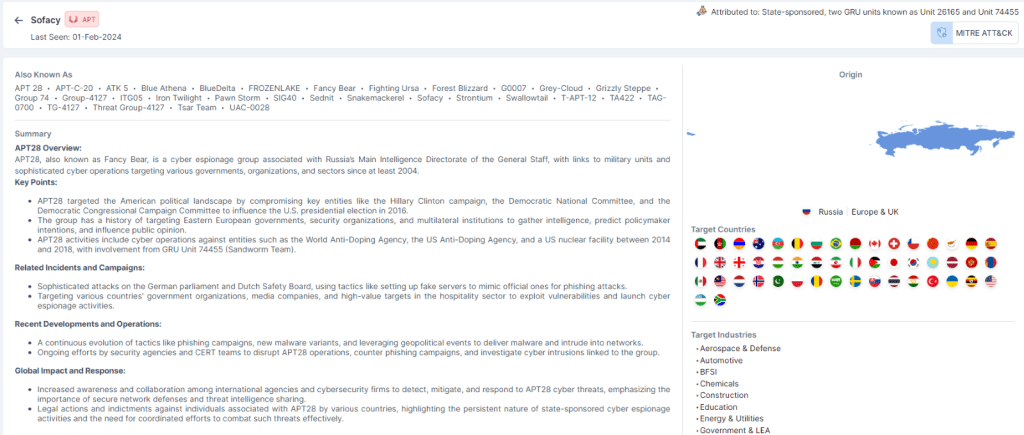
Figure 1 – Cyble Vision Threat Library
Country of Origin
Sofacy is a Russian State-sponsored cyber espionage group that has connections with two known GRU units, Unit 26165 and Unit 74455.
Targeted Countries
Sofacy is known for its extensive cyber espionage endeavours, which encompass a diverse array of countries and regions. These include Afghanistan, Armenia, Australia, Azerbaijan, Belarus, Belgium, Brazil, Bulgaria, Canada, Chile, China, Croatia, Cyprus, France, Georgia, Germany, Hungary, India, Iran, Iraq, Italy, Japan, Jordan, Kazakhstan, Latvia, Malaysia, Mexico, Mongolia, Montenegro, Netherlands, Norway, Pakistan, Poland, Romania, Saudi Arabia, Slovakia, South Africa, South Korea, Spain, Sweden, Switzerland, Tajikistan, Thailand, Turkey, Uganda, UAE, UK, Ukraine, USA, Uzbekistan, NATO and APEC and OSCE.

Figure 2 – Origin and Targeted Countries (Source: Cyble Vision)
Aliases
APT28, Fancy Bear, Sednit, Group 74, TG-4127, Pawn Storm, Tsar Team, Strontium, Swallowtail, SIG40, Snakemackerel, Iron Twilight, ATK 5, T-APT-12, ITG05, TAG-0700, UAC-0028, FROZENLAKE, Grey-Cloud, Grizzly Steppe, Forest Blizzard, BlueDelta, TA422, Fighting Ursa and Blue Athena
Targeted Sectors
- Automotive
- Aviation
- Chemical
- Construction
- Defense
- Education
- Embassies
- Energy
- Engineering
- Financial
- Government
- Healthcare
- Industrial
- IT
- Media
- NGOs
- Oil and gas
- Think Tanks
- Intelligence organizations
Links to Other APTs
Researchers suspect that Sofacy may be linked to Hades, although it is also possible that this connection is a false flag.
Reconnaissance
Sofacy demonstrates a thorough understanding of their targets’ applications and infrastructure by scanning for known vulnerabilities that can be exploited. Through spearphishing emails with malicious attachments, Sofacy not only launches attacks but also collects valuable information about the target systems and potential entry points. They also conduct active network scanning to identify live hosts, open ports, and running services, thereby gaining a deeper understanding of the network topology and pinpointing vulnerabilities for exploitation.
Resource Development
Sofacy demonstrates advanced capabilities through the development of sophisticated malware strains such as CORESHELL, Downdelph, and OCEANMAP, which are designed to exploit vulnerabilities, maintain persistence, and exfiltrate data. They also create custom tools like STEELHOOK for stealing data from web browsers and various PowerShell scripts to enhance their operational efficiency. By using shared infrastructure with other cybercriminals and freely available hosting providers like firstcloudit[.]com, Sofacy can stage their payloads, blend in with legitimate traffic, and evade detection. Additionally, they register domains that closely mimic legitimate organizations to create phishing sites for credential harvesting, significantly aiding their spearphishing campaigns.
Initial Infection
This group is renowned for employing a variety of initial access techniques, including spear phishing, credential theft, exploitation of public-facing infrastructure, and leveraging access obtained from other threat actors.
The Sofacy APT group registers domains that closely mimic those of their target organizations, creating phishing sites that replicate the appearance of the victims’ web-based email services. Their goal is to harvest credentials through these deceptive sites. Sofacy employs a dual strategy of sending phishing messages and using spoofed websites to gather login information.
The group has also exploited lures related to the ongoing Israel-Hamas conflict to deliver a custom backdoor called HeadLace. Additionally, they have targeted Ukrainian government entities and Polish organizations with phishing messages designed to deploy specialized implants and information stealers, such as OCEANMAP, MASEPIE, and STEELHOOK.
Phishing
The phishing campaign customizes its bait to specific targets using a variety of lures. These documents, disguised as official communications, target multiple governments across Europe, the Americas, Central Asia, and the South Caucasus. These topics cover a wide array of themes, including finance, critical infrastructure, executive engagements, cybersecurity, maritime security, healthcare, and defense industrial production.
The figure below displays unique Spanish-language lure files, likely mimicking official documents aimed at the Executive Branch of the Argentine Republic, as identified in a past campaign.

Figure 3 – Lure Document Targeting Argentina (Source: X-Force)
Exploited Vulnerabilities
The Sofacy group has exploited various vulnerabilities in its campaigns. We have listed some important vulnerabilities targeted below:
CVE-2024-21413: Microsoft Outlook Remote Code Execution Vulnerability
CVE-2024-21413: Microsoft Exchange Server Elevation of Privilege Vulnerability
CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
CVE-2023-23397: Microsoft Outlook Information Disclosure Vulnerability
CVE-2023-38831: RARLAB WinRAR Code Execution Vulnerability
CVE-2022-38028: Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2021-34527: Microsoft Windows Print Spooler Remote Code Execution Vulnerability
CVE-2021-1675: Microsoft Windows Print Spooler Remote Code Execution Vulnerability
Execution
Sofacy employs social engineering tactics to entice users into executing malicious payloads, frequently using spearphishing emails with appealing attachments or links. They utilize command and scripting interpreters, such as PowerShell, bash scripts, and command-line utilities, to run malicious scripts and commands on targeted systems. To ensure persistent execution, Sofacy leverages scheduled tasks, enabling their programs to run at specific times or intervals. Additionally, they exploit vulnerabilities such as the Print Spooler service (CVE-2022-38028), PrintNightmare (CVE-2021-34527 and CVE-2021-1675), and the WinRAR vulnerability (CVE-2023-38831) in client applications, including web browsers and document readers, to execute arbitrary code and gain control over targeted systems.
Persistence
Sofacy ensures persistence on compromised systems through various techniques. They utilize scheduled tasks to guarantee their malicious programs run at specified times or intervals. The group employs malicious CMD, LNK, and BAT files to create startup entries, ensuring payload execution at system startup. Additionally, Sofacy modifies folder permissions within victims’ mailboxes to enhance persistence and exploit email accounts. By leveraging these compromised email accounts, Sofacy maintains ongoing access to sensitive information and sustained control over the targeted systems.
Defense Evasion
Sofacy employs a multifaceted approach to evade detection and maintain covert operations. They discreetly execute commands using PowerShell and bash scripts, employing XOR-based string obfuscation to conceal malicious code. Exploiting vulnerabilities like Print Spooler and PrintNightmare bypasses security measures. Modifying folder permissions and utilizing legitimate system functionalities grant elevated privileges. They create startup entries resembling legitimate programs, blending seamlessly with normal operations. Leveraging shared infrastructure and public hosting providers obscures their activities amidst legitimate traffic. Additionally, they utilize public services like webhook[.]site and Mockbin for tracking infections and data transfer, adding a guise of legitimacy to their actions.
Tools used by Sofacy
Sofacy employs a diverse range of tools in its cyberespionage operations. These tools include Cannon, certutil, Computrace, CORESHELL, DealersChoice, Downdelph, Drovorub, Foozer, GooseEgg, Graphite, Headlace, HIDEDRV, Impacket, JHUHUGIT, Koadic, Komplex, LoJax, MASEPIE, Mimikatz, Nimcy, OCEANMAP, OLDBAIT, PocoDown, ProcDump, PythocyDbg, Responder, Sedkit, Sedreco, SkinnyBoy, SMBExec, STEELHOOK, USBStealer, VPNFilter, Winexe, WinIDS, X-Agent, X-Tunnel and Zebrocy.
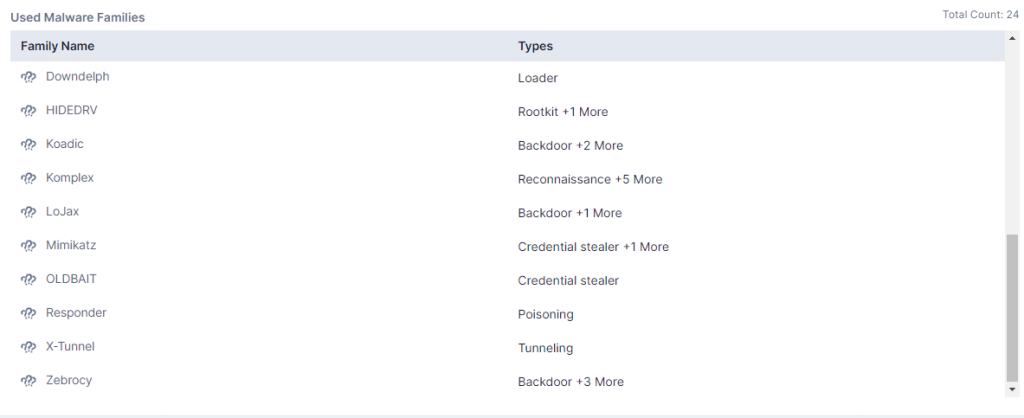
Figure 4 – Sofacy Tools (Source: Cyble Vision)
Cannon: The tool, written in C#, derives its name from the malicious code contained within a namespace called “cannon.” This Trojan primarily functions as a downloader, using email communication to connect with its C&C server. It sends emails to designated addresses via SMTPS over TCP port 587 to facilitate this communication.
Certutil: Certutil is a command-line utility used to obtain information about certificate authorities and configure Certificate Services.
Computrace: Absolute Software’s Computrace agent is a service designed to recover lost or stolen computers. It utilizes technology based on the LoJack Stolen Vehicle Recovery System. In 2005, Absolute Software licensed the LoJack name and tracking technology to enhance its efforts in recovering stolen computers.
CORESHELL: APT28 employs CORESHELL, a downloader. Earlier iterations of this malware were identified as SOURFACE, while newer variants are referred to as CORESHELL.
Downdelph: Sofacy operators sparingly deploy Downdelph, a first-stage component. It allows them to install X-Agent and Sedreco on compromised systems.
Drovorub: Drovorub is a Linux malware toolset that comprises an implant with a kernel module rootkit, a file transfer tool, and a C&C server. It allows direct communication, file manipulation, root-level command execution, and network traffic forwarding.
GooseEgg: GooseEgg is a loader binary designed to stealthily execute simple commands from the C&C server.
Graphite: Graphite is malware that utilizes the Microsoft Graph API and OneDrive for C&C communication. It operates in-memory only and functions as a downloader for Empire.
Headlace: Headlace is multi-component malware consisting of a dropper, a VBS launcher, and a backdoor that uses MSEdge in headless mode to continuously download secondary payloads, likely for exfiltrating credentials and sensitive information.
HIDEDRV: The rootkit HIDEDRV is designed to conceal itself and Downdelph from the user and inject Downdelph into explorer.exe.
Impacket: Impacket is an open-source Python library for creating and manipulating network protocols, featuring tools for remote execution, Kerberos, credential dumping, and attacks.
JHUHUGIT: A simple tool designed for downloading and persisting a next-stage payload, it gathers system information and metadata to distinguish real targets from sandbox environments. It checks internet connectivity using search engine domains like Google and employs XOR-based string obfuscation with a 16-byte key.
Koadic: Koadic is a Windows post-exploitation framework and penetration testing tool. It is available publicly on GitHub and can be executed via the command line.
Komplex: The Komplex Trojan is used in attack campaigns targeting the OS X operating system. It can download, execute, and delete files and interact directly with the system shell.
LoJax: LoJax is a trojanized version of the popular LoJack anti-theft software. It can implement the UEFI/BIOS module as a persistence mechanism.
MASEPIE: MASEPIE is a Python-based malware that establishes persistence by modifying the Windows registry and dropping an LNK file in the startup folder.
Mimikatz: Mimikats is a very popular tool for duplicating credentials from a Windows system. It can retrieve cleartext passwords, Lan Manager hashes, NTLM hashes, certificates, and Kerberos tickets.
Nimcy: The Nimcy backdoor, developed in the Nimrod/Nim programming language, targeted Malaysian and Thai entities. It represents Zebrocy’s latest addition to its collection of languages for creating core functionalities in new backdoors.
OCEANMAP: OCEANMAP, a C# backdoor, executes base64-encoded commands via cmd.exe and ensures persistence by creating a ‘VMSearch.url’ file in the Windows Startup folder. It discreetly receives IMAP commands stored as email drafts with command details.
OLDBAIT: OLDBAIT is a credential harvester that installs itself in %ALLUSERPROFILE%\Application Data\Microsoft\MediaPlayer\updatewindws.exe. The directory name for MediaPlayer lacks a space, and the filename is missing the ‘o’ character. Both internal strings and logic are obfuscated and unpacked at startup.
PocoDown: PocoDown utilizes the POCO C++ cross-platform library and XOR-based string obfuscation, along with SSL library code. It also has string overlaps with X-Tunnel and shares infrastructure with X-Agent, suggesting it has been active since around mid-2018.
Responder: Responder is an open-source tool that conducts LLMNR, NBT-NS, and MDNS poisoning. It features a built-in rogue authentication server that supports various protocols like HTTP, SMB, MSSQL, FTP, and LDAP. It also supports NTLMv1, NTLMv2, LMv2, Extended Security NTLMSSP, and Basic HTTP authentication.
Sedkit: Sedkit, also known as the Sednit exploit kit, is exclusively employed for targeted attacks. It initiates through targeted phishing emails containing URLs that mimic legitimate ones. Our knowledge extends to October 2016 as the last documented usage of Sedkit.
Sedreco: Sedreco functions as a spying backdoor, offering extendable functionalities through dynamically loaded plugins. It comprises two distinct components, including a dropper responsible for installing the persistent payload.
SMBExec: An accelerated attack akin to PsExec utilizing Samba tools.
STEELHOOK: A collection of PowerShell scripts named ‘STEELHOOK’ is utilized to extract data from Chrome-based web browsers, targeting sensitive information such as passwords, authentication cookies, and browsing history.
USBStealer: Sofacy has employed USBStealer since at least 2005. It extracts information from air-gapped networks. Although it is incapable of internet communication, it is often used alongside Sedreco.
VPNFilter: VPNFilter is malware that infects various network routers and storage devices. It appears to target serial networking devices, particularly those using the Modbus protocol to communicate with and manage industrial hardware commonly found in factories and warehouses.
Winexe: Winexe is a lightweight, open-source tool similar to PsExec that enables system administrators to execute commands on remote servers. It is a GNU/Linux-based client.
X-Agent: X-Agent, also known as CHOPSTICK, is a modular backdoor malware family utilized by APT28. Operating since at least 2012, it typically serves as second-stage malware, although it has been observed as first-stage malware in some instances. Available in Windows and Linux variants, it is distinct from the X-Agent for Android.
X-Tunnel: X-Tunnel is a network proxy tool that adopts a custom network protocol encapsulated within the TLS protocol. win.xtunnel_net, a reimplementation of win.xtunnel, emerged in late 2017, utilizing the .NET framework.
Zebrocy: Zebrocy, a Trojan employed by APT28 since November 2015, exists in multiple programming language variants such as C++, Delphi, AutoIt, C#, and VB.NET.
Network Activities
Sofacy employs various methods to communicate with its C&C server. In a previous campaign, Sofacy utilized a third-party criminal proxy botnet for espionage, blending its espionage traffic with other cybercrime-related activities. It often uses infrastructure shared with other cybercriminals to host its malware and exploits.
In a campaign this March, Sofacy leveraged the freely available hosting provider firstcloudit[.]com to stage payloads for ongoing operations. Additionally, Sofacy’s operations heavily rely on public services like webhook[.]site to closely monitor infections. While webhook services are legitimate development tools, they are frequently abused for malicious purposes.
For C&C communication, the OCEANMAP backdoor uses IMAP, checking the inbox every minute for commands from the sender. Researchers also observed the use of Mockbin, an API endpoint generation tool, and mock APIs to transfer stolen data, such as NTLM hashes and command outputs.
Conclusion
The Sofacy APT group employs sophisticated, multifaceted attack strategies and persistence mechanisms. By exploiting a range of vulnerabilities, including those in Print Spooler, PrintNightmare, and WinRAR, they effectively infiltrate and maintain access to targeted systems. Their use of various scripts and malicious files, alongside leveraging legitimate services for C&C communication, demonstrates their adaptability and resourcefulness in cyber espionage, posing a significant threat to global cybersecurity.
Recommendations:
To defend against the sophisticated tactics employed by Sofacy, consider implementing the following recommendations:
Patch Management: Regularly update and patch all systems, applications, and network devices to protect against known vulnerabilities, such as Print Spooler (CVE-2022-38028), PrintNightmare (CVE-2021-34527, CVE-2021-1675), and WinRAR (CVE-2023-38831).
Endpoint Protection: Deploy advanced endpoint protection and detection solutions to identify and block malicious CMD, LNK, and BAT files.
Email Security: Implement robust email security measures, including phishing protection and attachment scanning, to prevent the delivery of malicious payloads via email.
User Education: Conduct regular cybersecurity training to educate users on recognizing phishing attempts and other social engineering tactics.
Access Controls: To limit the impact of a potential breach, enforce strict access controls and least privilege principles, particularly for administrative accounts.
Network Segmentation: Segment networks contain any potential intrusions and limit lateral movement by attackers.
Logging and Monitoring: Implement comprehensive logging and monitoring to detect unusual activities, such as unauthorized scheduled tasks or changes to startup folders and mailbox permissions.
Public Service Monitoring: Monitor the use of public services, like webhooks, for any unauthorized or suspicious activities.
Incident Response Plan: Develop and regularly update an incident response plan to swiftly address any security breaches.
Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and mitigate potential security weaknesses.
MITRE attack Techniques Associated with Sofacy

Figure 5 – MITRE ATT&CK (Source: Cyble Vision)
Vulnerability Scanning (T1595.002): Scanning for known vulnerabilities to exploit.
Spearphishing Attachment (T1566.001): Using spearphishing emails with malicious attachments to initiate attacks.
User Execution (T1204): Relying on social engineering to persuade users to execute malicious payloads.
Scheduled Task (T1053.005): Leveraging scheduled tasks to maintain persistence on compromised systems.
Command and Scripting Interpreter (T1059.003): Utilizing command and scripting interpreters to run malicious scripts and commands.
Exfiltration Over Alternative Protocol (T1048): Exfiltrating stolen data using alternative protocols to evade detection.
Data from Local System (T1005): Gathering sensitive information from local systems during operations.










