Take your cybersecurity to the next level with tailored threat intelligence solutions from Cyble
Leveraging Security Analytics, AI, and an Extensive Repository of Actionable Intelligence for Empowered Threat Detection
Cyble's Cyber Threat Intelligence Solutions

Attack Surface Management
Identify and mitigate threats across your entire attack surface to ensure your digital security and protect your organization from potential vulnerabilities.

Brand Intelligence
Safeguard your brand against online abuse, including impersonation, phishing, and fraudulent domains. Maintain your brand’s integrity and trust in the digital space.

Cyber Threat Intelligence
Leverage AI-driven analysis and continuous threat monitoring to gain critical insights and enhance your organization’s defence against emerging cyber threats.

Dark Web and Cyber Crime Monitoring
Monitor the dark web and cybercrime activities to stay vigilant and one step ahead of cybercriminals. Protect sensitive information from being exploited.

Vulnerability Management
Utilize advanced scanning, risk evaluation, and efficient remediation strategies to get a real-time view of your exploitable vulnerabilities.
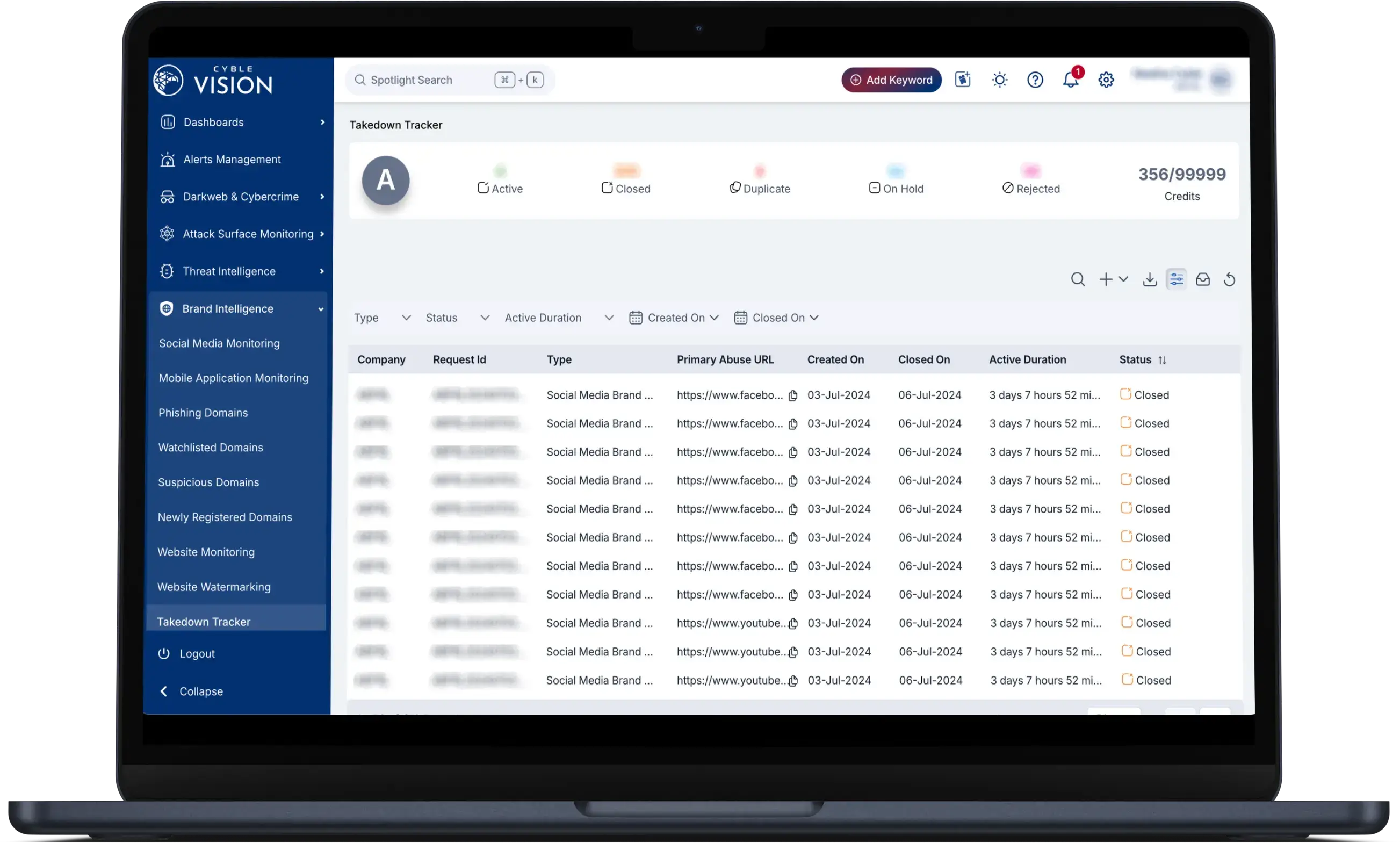
Takedown & Disruption
Combat Online Fraud and Cybercrime with Cyble's Powerful Takedown Services

Third-Party Risk Management (TPRM)
Identify, assess, and mitigate risks arising from interactions with third parties. TPRM ensures that your business remains secure while collaborating with external entities.

Digital Forensics & Incident Response (DFIR)
At Cyble, we provide comprehensive Digital Forensics and Incident Response (DFIR) services to help businesses effectively manage, mitigate, and recover from cybersecurity incidents.
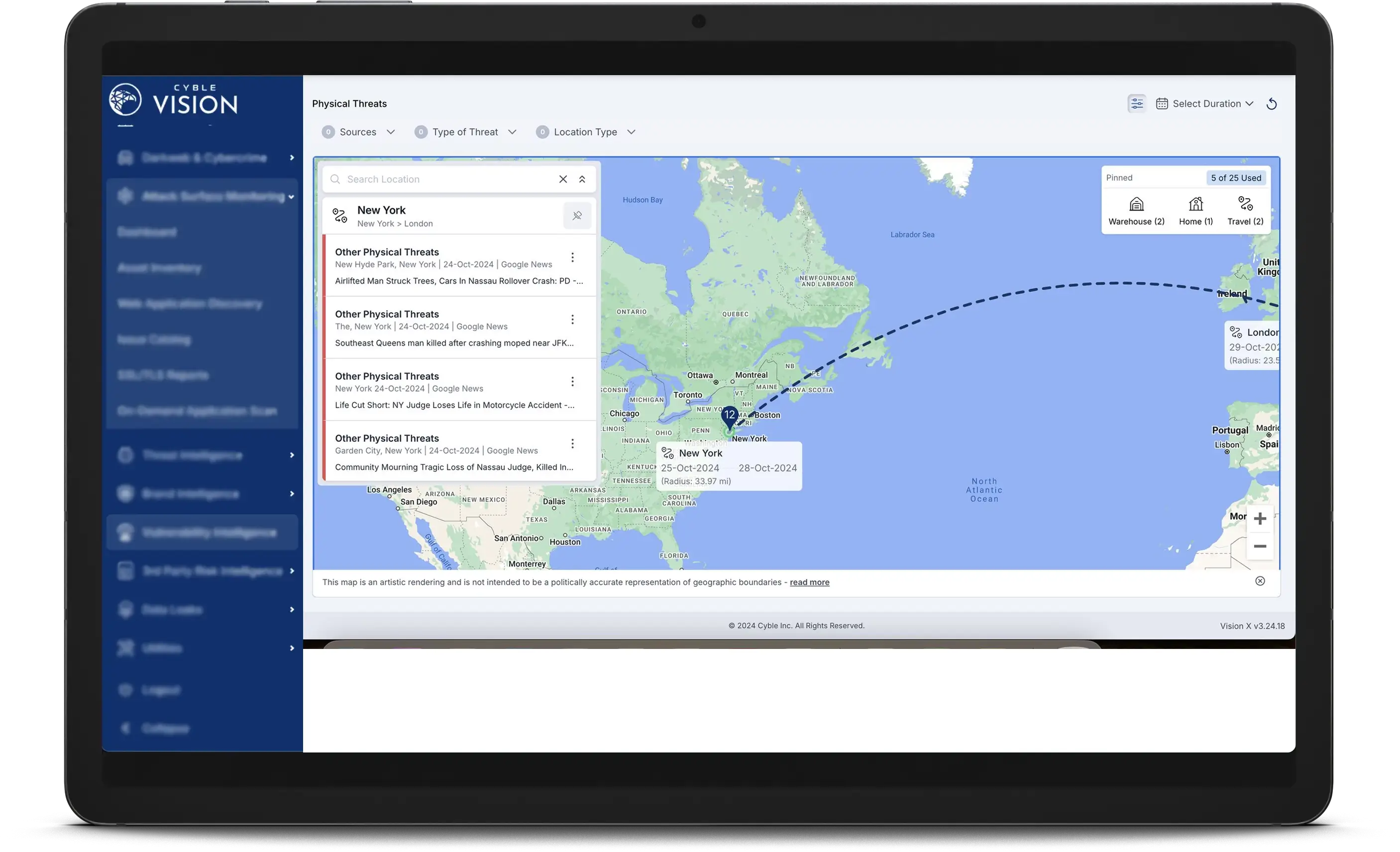
Physical Threat Intelligence
In an unpredictable world where threats can emerge at any time, securing your physical assets and people is no longer just an option—it’s a necessity. Cyble’s Physical Threat Intelligence equips you with cutting-edge insights and real-time updates to ensure you are not just reacting but dominating the ever-evolving threat landscape.

Executive Monitoring
The Executive Monitoring module offers comprehensive protection for high-profile executives by detecting and alerting on digital threats such as executive deepfakes , identity theft, public mentions, data breaches, and compromised credentials. This powerful suite of tools enables organizations to proactively safeguard their leadership from reputational and security risks in today’s digital landscape.
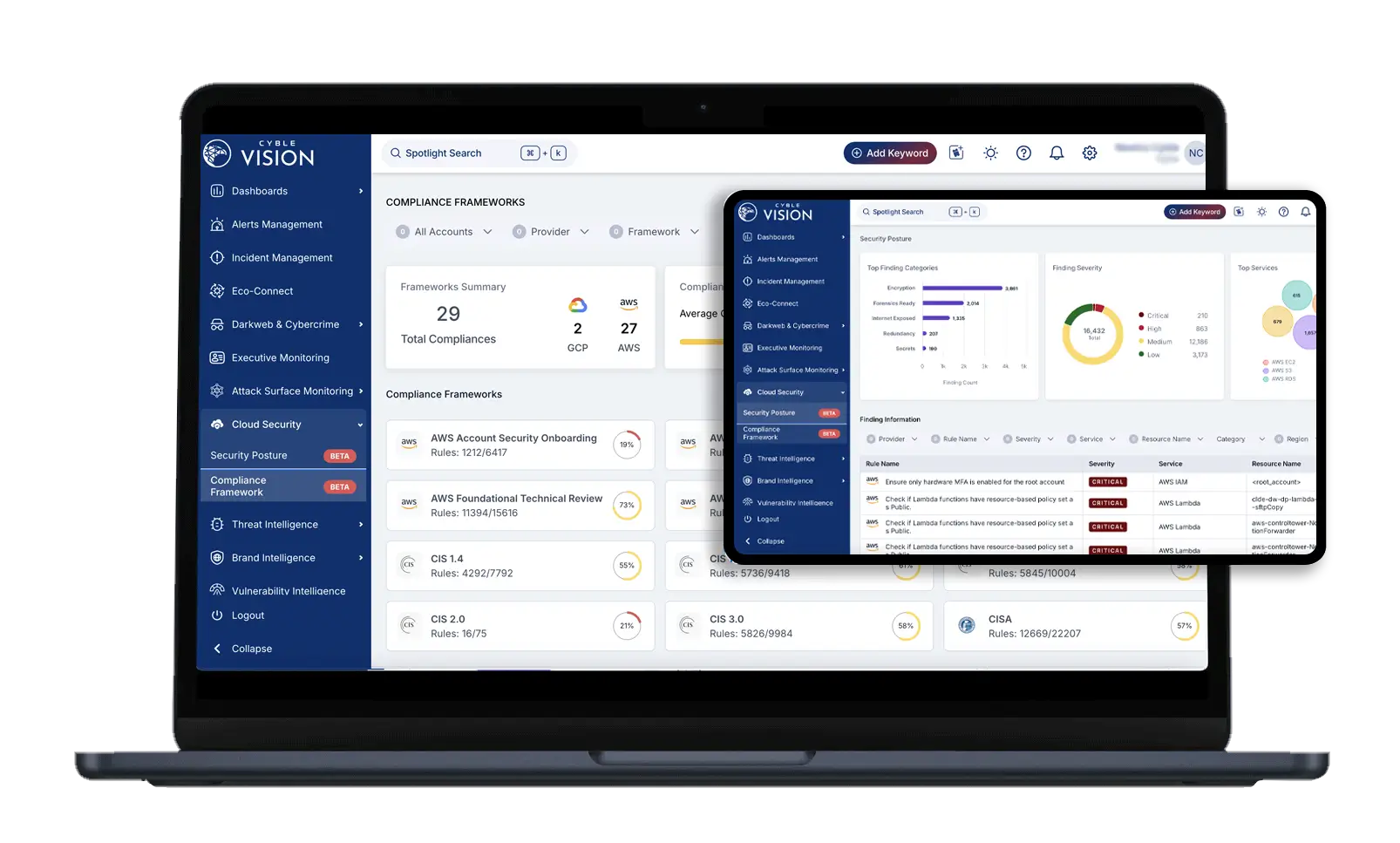
Cloud Security Posture Management (CSPM)
Cyble’s Cloud Security Posture Management (CSPM) solution offers organizations a comprehensive toolset for managing and securing cloud assets, meeting compliance standards, and proactively identifying potential vulnerabilities. Seamlessly integrated with CybleVision and CybleHawk, CSPM provides a holistic approach to cloud security—enabling unified threat detection, real-time compliance, and automated risk management across your cloud and on-premises environments.

BotShield
BotShield protects your network from botnet-driven threats, providing insights into DDoS attacks and malicious C2 structures.
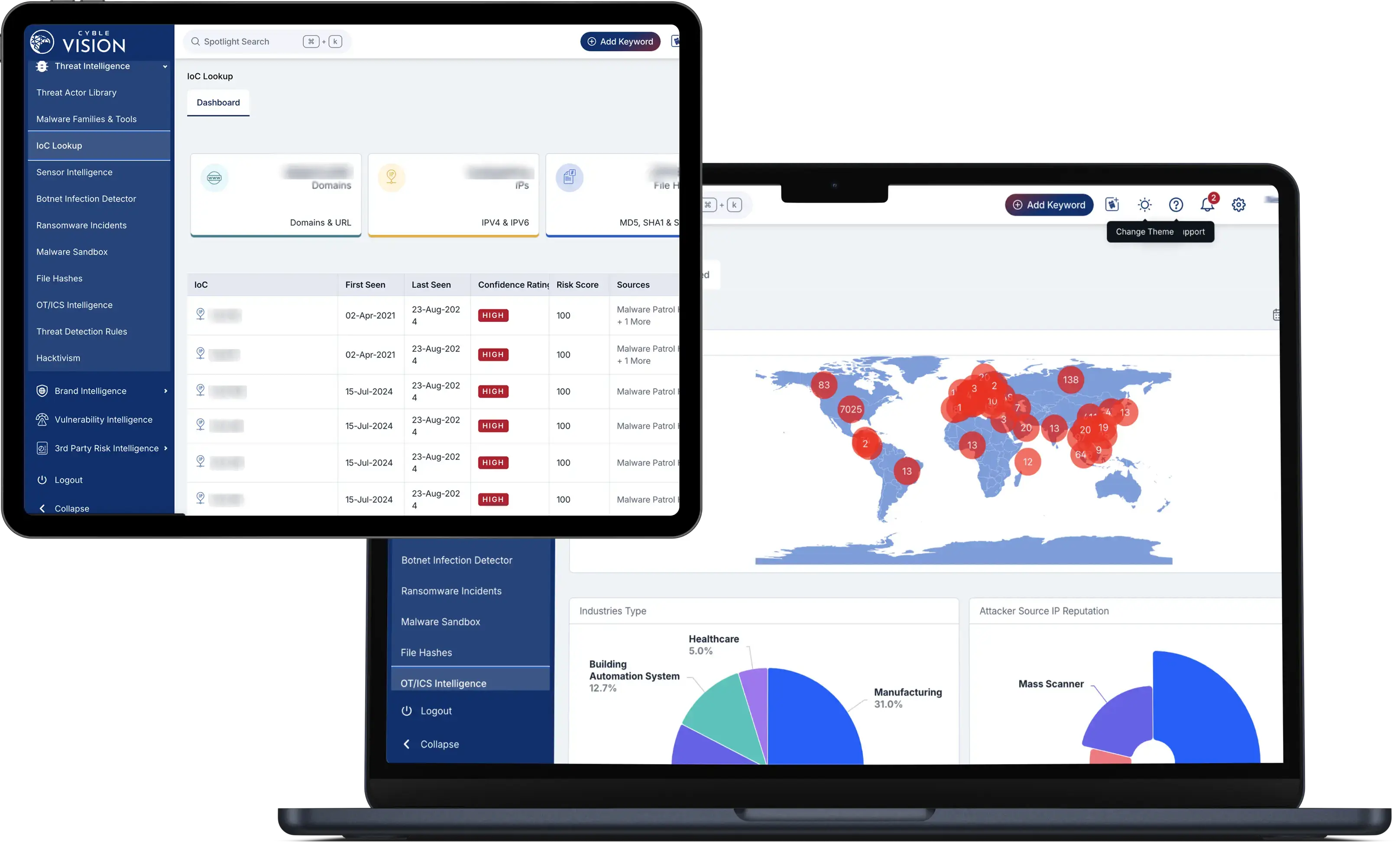
Incident Management
Group alerts into incidents for faster resolutions, enhanced collaboration, and efficient SOC operations. Features include dashboards, audit logs, and role-based permissions.
Cyber Threat Intelligence Solutions by Industry

Financial Services
Financial fraud and social engineering scams are a growing threat to businesses and individuals alike.

Retail and CPG
As online shopping gains popularity, cybercriminals launch scams against your business, supply chain, and employees through counterfeit products.

Healthcare & Pharmaceuticals
In the healthcare industry, patients rightfully expect robust data security measures to protect their sensitive information.

Technology Industry
The technology industry is susceptible to cyber attacks. These attacks cannot be thwarted by basic firewalls alone.

Educational Platform
Cyberattacks are not restricted to any specific age group, and that’s why the Cyble Platform is essential to ensure ongoing.

Information Security
A cybersecurity solution is crucial for information security due to the expanding coverage of enterprise information.

Corporate Security
The rise of social and digital platforms has introduced a new dimension of risk to corporate security.

Marketing
Secure your business from threats that can harm your revenue, including your brand, social reputation.

