Overview
The Carbanak group is a financially motivated cybercriminal organization that has been active since late 2013, primarily targeting banks, financial institutions, and related sectors. Known for orchestrating technical campaigns that result in substantial monetary losses, Carbanak’s operations revolve around exploiting human trust and leveraging digital vulnerabilities. Unlike state-sponsored actors who often pursue espionage objectives, Carbanak’s motivation is strictly financial.
The group has demonstrated remarkable persistence despite ongoing law enforcement efforts aimed at dismantling their operations. Their campaigns typically combine spear phishing, malware deployment, and web traffic manipulation to compromise targeted systems. Once inside a network, Carbanak actors extract sensitive data and gain access to banking systems, often executing thefts that can result in multi-million-dollar losses.
Origin and Geographical Footprint
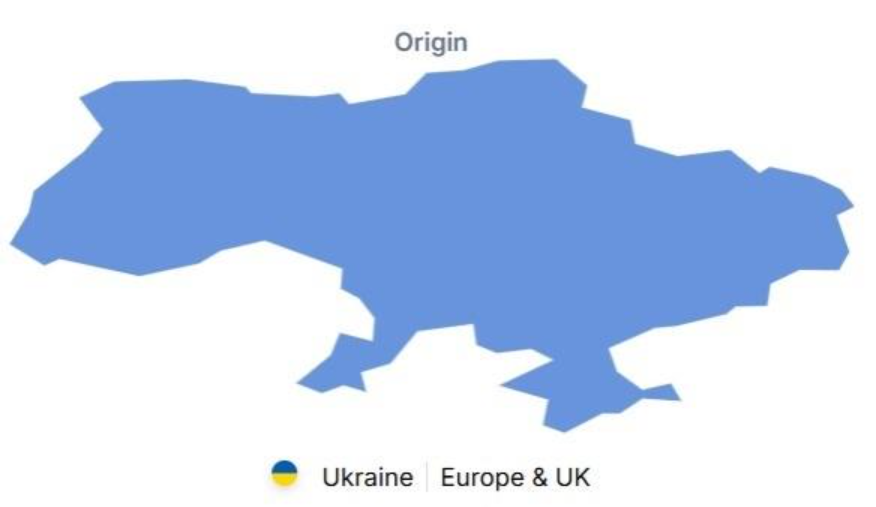
Carbanak is believed to have originated in Ukraine, with activities reported across Europe and the United Kingdom. The group’s targets span the globe, affecting countries including the United States, Canada, Germany, France, the United Kingdom, Austria, Australia, Brazil, China, India, Russia, and many others. This broad reach illustrates the group’s ability to adapt its methods to diverse regional and technological environments.
The industries most affected by Carbanak’s operations include banking, financial services, insurance (BFSI), healthcare, energy and utilities, agriculture, food and beverages, and hospitality. This range reflects the group’s strategic focus on sectors with high-value financial assets or critical operational infrastructure.
Attack Methodology
Carbanak’s campaigns typically begin with spear phishing emails designed to appear legitimate. These emails often impersonate banking communications or other trusted sources, with attachments that carry hidden malware payloads. When recipients open these attachments, the malware is deployed, granting attackers access to the organization’s network.
In addition to phishing, Carbanak frequently redirects web traffic related to financial transactions to exploit kits. These kits take advantage of vulnerabilities in web browsers and plugins to compromise user systems, allowing the group to extend its access and infiltrate critical financial applications.
Once inside the network, Carbanak actors employ a combination of malware families and tools to establish control, maintain persistence, and exfiltrate sensitive information. Their approach blends reconnaissance, credential theft, lateral movement, and covert data extraction.
Tooling and Malware Families
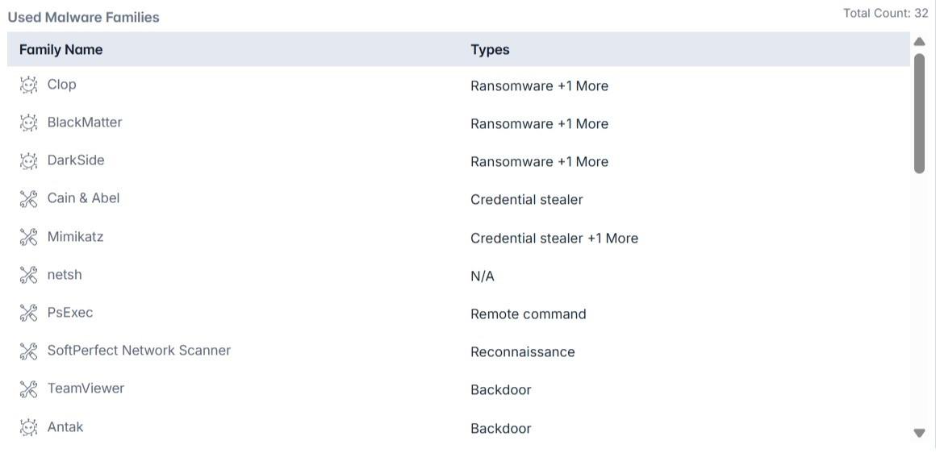
Carbanak is associated with over thirty malware families, each serving specific functions within their campaigns. Key examples include:
- Ransomware Families: Clop, BlackMatter, DarkSide
- Credential Stealers: Cain & Abel, Mimikatz, FOXGRABBER
- Backdoors: TeamViewer, Antak, Bateleur, POWERSOURCE
- Reconnaissance Tools: SoftPerfect Network Scanner, DRIFTPIN, HALFBAKED
- Tunneling and Remote Access: BABYMETAL, DNSMessenger, DNSRat
For instance, BlackMatter and DarkSide ransomware families are employed to encrypt victim files and demand ransom payments. BlackMatter uses a unique encryption method that appends random character strings to encrypted files and leaves ransom notes, while DarkSide is known for its stealthy, methodical approach and threatening disclosure of stolen data to coerce payments.
Legitimate tools are also exploited. PsExec allows attackers to execute commands remotely and move laterally within networks. Netsh, a Windows utility, can be misused to manipulate network configurations and create covert backdoors. SoftPerfect Network Scanner is often repurposed for reconnaissance, enabling attackers to identify vulnerable devices and services on a network.
Techniques and Tactics
Carbanak employs a wide range of tactics, techniques, and procedures (TTPs) consistent with modern financially motivated threat actors. These include:
- Initial Access: Spear phishing emails with malicious attachments or links, compromise of public-facing applications, and supply chain attacks.
- Execution: Malicious files, DDE-enabled Word documents, and reverse shells initiated through command-line tools.
- Persistence: Scheduled tasks and backdoors to maintain continuous access.
- Reconnaissance and Lateral Movement: Mapping networks and using administrative utilities to escalate privileges.
- Credential Theft and Exfiltration: Capturing login credentials, accessing stored passwords, and extracting sensitive data.
Conclusion
Carbanak exemplifies a financially motivated threat actor capable of causing losses through targeted and persistent cyberattacks. Their use of spear phishing, malware, and network exploitation continues to challenge organizations worldwide. While law enforcement has disrupted parts of their infrastructure, Carbanak’s adaptability makes it a persistent threat.
Platforms like Cyble, the world’s first intelligence-driven AI-native security platform, give organizations the foresight to stay ahead. With Blaze AI, Cyble predicts, hunts, and neutralizes threats in real time, turning intelligence into actionable defense.
When threat actors strike, Cyble has you covered.
Get a Free Threat Assessment and uncover hidden risks before attackers do.
Recommendation and Mitigation Strategies
Organizations facing threats from groups like Carbanak should adopt a multi-layered defense strategy:
- Implement multi-factor authentication to mitigate stolen credentials.
- Harden email and web security with phishing simulations, link scanning, and attachment filtering.
- Monitor endpoints with behavioral detection tools to identify unusual activity indicative of malware.
- Limit lateral movement by network segmentation and strict access controls.
- Conduct continuous threat monitoring and maintain incident response playbooks for rapid containment.
Proactive security awareness training remains critical, as Carbanak’s reliance on social engineering makes human error the primary entry vector.
MITRE ATT&CK Techniques Associated with the Carbanak Group
- Replication Through Removable Media (T1091): FIN7 mailed USB drives containing malware that downloads and installs various backdoors, sometimes for ransomware.
- Exploit Public-Facing Application (T1190): FIN7 exploited CVE-2021-31207 in Microsoft Exchange to compromise organizations.
- Compromise Software Supply Chain (T1195.002): FIN7 gained access by compromising a victim’s software supply chain.
- Spearphishing Attachment (T1566.001): FIN7 sent spearphishing emails with malicious Microsoft Documents or RTF files.
- Windows Management Instrumentation (T1047): FIN7 used WMI to install malware on targeted systems.
- Windows Command Shell (T1059.003): Carbanak executed commands to create reverse shells.
- Malicious Link (T1204.001): FIN7 used links to lure victims into downloading malware.
- Malicious File (T1204.002): Victims were tricked into double-clicking images that executed hidden LNK files.
- Dynamic Data Exchange (T1559.002): Malicious Word documents with DDE execution were used in FIN7 spearphishing campaigns.
- Scheduled Task (T1053.005): FIN7 created scheduled tasks to maintain malware persistence.
- Valid Accounts (T1078): Carbanak used legitimate banking employee credentials to perform fraudulent operations.
- Local Account (T1136.001): Carbanak can create local Windows accounts for access.
- Windows Service (T1543.003): Malware installs itself as a Windows service to gain SYSTEM privileges and persistence.









