Overview
CyberVolk is a politically motivated hacktivist collective that has progressively transitioned into a hybrid threat actor combining ideological operations with financially driven cybercrime.
Initially known for disruptive attacks aligned with pro-Russian narratives, the group has expanded its operational scope to include ransomware activity. This evolution places CyberVolk in a growing category of actors that blur the line between ideological activism and criminal enterprise.
The group was last observed operating in mid-December 2025, indicating continued activity despite intermittent periods of disruption. CyberVolk has also been linked to broader alliances with other ideologically aligned collectives.
Who is CyberVolk?

CyberVolk operates under multiple names and identifiers, including CyberVolk Group and CyberVolkArcanum, with some aliases appearing intermittently across different platforms and campaigns.
The use of varied naming conventions reflects both deliberate obfuscation and the decentralized nature of hacktivist ecosystems rather than distinct subgroups. CyberVolk is assessed to be part of a broader alliance often referred to as the “Holy League,” a loose coalition of actors sharing geopolitical objectives and infrastructure.
While some references associate the group with organized crime naming conventions, available evidence supports classifying CyberVolk primarily as a politically motivated collective that has adopted criminal tooling rather than a traditional organized crime syndicate.
Origin and Geographic Scope
CyberVolk is assessed to have originated from the Asia-Pacific region, with activity linked to India. Despite this regional association, the group’s operational footprint is global. Observed targeting spans North America, Europe, Asia, and parts of Oceania and South America.
Countries affected by CyberVolk operations include the United States, Mexico, Spain, France, Germany, Belgium, Ireland, Italy, Japan, Pakistan, Russia, Turkey, Ukraine, Australia, Sweden, and Venezuela.
The geographic diversity of targets suggests a combination of ideologically motivated campaigns tied to geopolitical events and opportunistic targeting of exposed or symbolically relevant entities.
Targeted Sectors
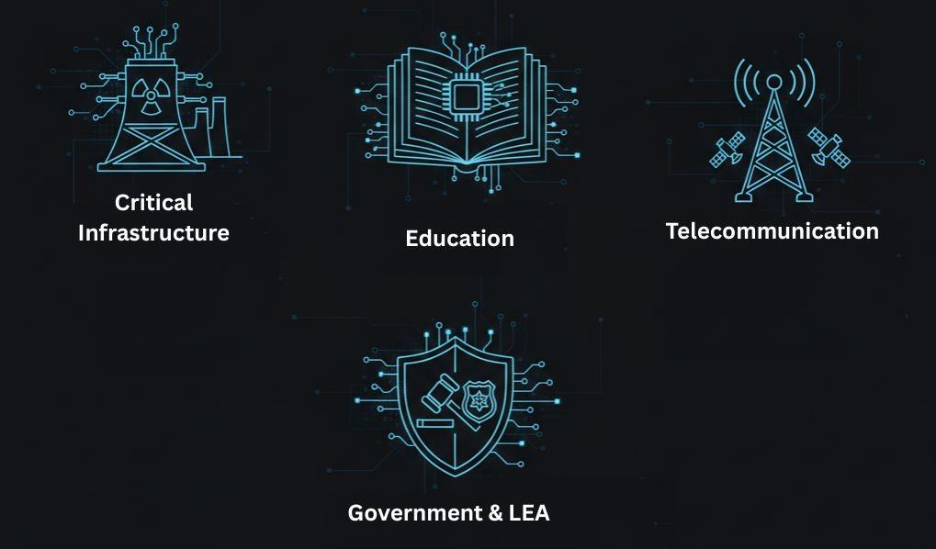
CyberVolk’s operations have focused on sectors with high political, social, or economic visibility. Targeted industries include:
- Government and law enforcement agencies
- Critical infrastructure operators
- Telecommunications providers
- Educational institutions
The emphasis on government and infrastructure entities aligns with hacktivist objectives aimed at disruption, signaling, and public messaging.
Operational Evolution
Historically, CyberVolk activity centered on disruptive attacks such as defacements and denial-of-service campaigns framed as ideological retaliation. Over time, the group demonstrated technical ambition, culminating in the development of proprietary ransomware tooling.

In late 2025, CyberVolk resurfaced after a period of reduced visibility, which analysts attribute in part to earlier takedowns and account bans on messaging platforms. Upon reemergence, the group introduced a ransomware-as-a-service model branded as VolkLocker.

This shift indicates a strategic move toward sustained financial operations while retaining ideological messaging; a pattern observed among modern hacktivist collectives.
Malware and Tooling
VolkLocker represents CyberVolk’s most notable technical development. Written in Golang, the ransomware is designed for cross-platform deployment, with confirmed support for both Windows and Linux environments. This expansion broadens the group’s potential victim pool, particularly among infrastructure and enterprise systems.
The ransomware is designed for automation, allowing operators to generate new variants by supplying configuration parameters such as cryptocurrency payment details, encryption deadlines, and communication tokens. Control and victim interaction are handled almost entirely through Telegram-based bots, enabling attackers to manage infections, issue instructions, and coordinate campaigns using a single platform.
Encryption is performed using AES-256 in Galois/Counter Mode, with a randomly generated nonce applied per file. However, the implementation suffers from significant key management weaknesses.
A single master key is reused across files and stored insecurely, undermining the effectiveness of the encryption scheme. Analysts assess that this flaw likely originated from a development or testing feature that was never removed.
Persistence and Destructive Capabilities
On Windows systems, VolkLocker attempts to weaken host defenses by disabling security controls and recovery mechanisms. Observed behaviors include registry modifications, execution of PowerShell commands, and efforts to block access to administrative tools such as Task Manager and the command line.
Persistence is achieved by copying the ransomware binary into multiple directories commonly overlooked by users. Once active, the malware presents a dynamic ransom note with a countdown timer intended to pressure victims into payment. While the visual timer itself is not authoritative, a separate destructive routine activates after the deadline, initiating file deletion, shadow copy removal, and forced system crashes through native system calls.
Linux variants demonstrate similar encryption logic and rely on the same Telegram-based command infrastructure, reinforcing the group’s preference for centralized control with minimal external dependencies.
Linked Groups and Collaboration
CyberVolk maintains relationships with other ideologically aligned collectives, including AlixSec. These collaborations appear opportunistic rather than hierarchical, often forming shared geopolitical interests or coordinated campaigns. Such partnerships reflect a broader trend of fluid alliances within the hacktivist ecosystem, where tools, access, and messaging are shared across loosely affiliated groups.
Conclusion
CyberVolk operates as a hybrid threat actor that merges ideological hacktivism with monetized ransomware activity, creating a sustained risk for government, public-sector, and critical infrastructure organizations. Although its tooling exhibits technical shortcomings, the group’s continued adaptation, cross-group collaboration, and expansion into ransomware operations demonstrate a level of operational intent that should not be underestimated.

Addressing hybrid threats like CyberVolk requires clear visibility into attacker infrastructure, tooling, and campaign activity. Cyble provides actionable, AI-driven threat intelligence that helps security teams detect new cyber threats early, track adversary behavior, and respond with confidence.
Book a personalized demo today or explore how Cyble’s threat intelligence solutions strengthen your security posture.
Recommendation and Mitigation Strategies
- Strengthen Backup and Recovery Practices: Maintain offline, immutable backups for both Windows and Linux systems to ensure rapid restoration in the event of ransomware activity and to mitigate destructive post-encryption routines.
- Harden Endpoint Security Controls: Enforce endpoint protection capable of detecting suspicious behavior such as unauthorized registry changes, abnormal PowerShell execution, and attempts to disable security tools.
- Restrict Messaging Platform Abuse: Monitor and control the use of external messaging platforms, including Telegram, within enterprise environments to reduce the risk of command-and-control abuse and unauthorized automation.
- Apply Least-Privilege Access Models: Limit administrative privileges and routinely audit user permissions to reduce the impact of ransomware attempting to modify system settings or establish persistence.
- Enhance Network Monitoring: Deploy network-level monitoring to identify unusual outbound connections, particularly encrypted or automated traffic patterns that may indicate ransomware coordination or data exfiltration.
- Patch and Secure Cross-Platform Systems: Ensure timely patching and configuration hardening across both Windows and Linux environments, with particular attention to infrastructure and server systems.
- Conduct Threat Intelligence–Driven Assessments: Incorporate up-to-date threat intelligence to track CyberVolk-related indicators, new tactics, and affiliated groups, enabling proactive defense against evolving hybrid campaigns.
MITRE ATT&CK Techniques Associated with CyberVolk

- PowerShell (T1059.001): PowerShell commands and scripts are abused to execute code, download and run payloads from the internet, perform system discovery, and execute actions locally or remotely, often without directly invoking the powershell.exe binary to evade detection.
- Windows Command Shell (T1059.003): The Windows command prompt is leveraged to execute commands and payloads, run batch scripts, and interactively control compromised systems, including remote execution via command-and-control channels.
- Bypass User Account Control (T1548.002): User Account Control mechanisms are bypassed to elevate privileges by abusing auto-elevated Windows binaries, Component Object Model (COM) objects, or injecting malicious code into trusted processes without triggering user prompts.
- Obfuscated Files or Information (T1027): Files and payloads are encrypted, compressed, encoded, or split into multiple components to hinder detection and analysis, including the use of obfuscated scripts and hidden plaintext strings.
- Virtualization/Sandbox Evasion (T1497): Techniques are used to detect virtual machines or sandbox environments by checking for analysis artifacts, security tools, or lack of user activity, allowing malware to delay execution, alter behavior, or remain dormant to evade analysis.
- Command Obfuscation (T1027): Commands are obscured using environment variables, aliases, special characters, or language-specific features to bypass signature-based detection and application control mechanisms.