The Medusa ransomware group is one of the most menacing cybercrime groups, with a notorious reputation in the cyber underworld. Operating under the Ransomware-as-a-Service (RaaS) model, Medusa has claimed over 300 victims worldwide, targeting sectors ranging from healthcare and education to manufacturing and legal services. Its aggressive tactics and advanced techniques have placed it firmly on the radar of cybersecurity professionals worldwide.
As of April 22, 2025, the group remains active, demonstrating no signs of slowing down. Behind Medusa is a threat actor tracked as Spearwing, believed to be at the core of its development and operational infrastructure. Despite the name similarity, Medusa is unrelated to MedusaLocker or the Medusa mobile malware.
What makes Medusa particularly dangerous is its double extortion strategy. After infiltrating a victim’s network and encrypting critical data, the group doesn’t just stop there. Victims are then threatened with the public release of sensitive information unless ransoms—often between $100,000 and $15 million—are paid. This approach pressures victims from both an operational and reputational standpoint.
To support this extortion, Medusa maintains a data leak site (DLS) known as the “Medusa Blog”, where it showcases stolen data from non-compliant organizations. These disclosures are designed to publicly shame companies and amplify the urgency of payment.
Targeted Regions and Sectors

The group’s operations span more than 45 countries, including the United States, the United Kingdom, Germany, Australia, Canada, India, France, Brazil, Spain, and South Africa. Their geographic targets often include profitable organizations and Small and medium-sized enterprises (SMEs). The group prefers countries and sectors with advanced digital infrastructures and sectors rich in sensitive, high-value data.
The Medusa ransomware group has demonstrated a truly global reach, targeting organizations across a wide range of countries. Notable among these are the United States, Germany, the United Kingdom, Australia, India, France, Canada, Brazil, and Italy. However, their operations extend far beyond these, impacting dozens of other nations across Europe, Asia, the Middle East, Africa, and South America.
In terms of industry focus, Medusa’s attacks are equally broad and strategic. The group has struck sectors including healthcare, education, technology, manufacturing, and insurance, as well as media and entertainment, government and law enforcement, energy and utilities, transportation and logistics, and retail and consumer goods. This deliberate targeting of industries that handle vast amounts of sensitive data and rely heavily on operational continuity suggests a carefully calculated approach designed to maximize pressure on victims and increase the likelihood of ransom payment.
Public Channels and Psychological Warfare
Interestingly, the group is not confined to the shadows. Medusa maintains a presence on social media and communication platforms, including a Telegram channel, a Facebook profile, and an X (formerly Twitter) account branded as “OSINT Without Borders.” These channels are allegedly managed by personas using the names Robert Vroofdown and Robert Enaber, adding a public-facing element to their extortion tactics.
These platforms serve dual purposes: to increase public pressure on victims and to demonstrate their capabilities to the broader cybersecurity community. There’s also an associated OSINT Without Borders website, which may be used to coordinate further attacks or amplify exposure.
The Role of Frozen Spider
Threat intelligence links Medusa’s operations to a known organized cybercriminal entity dubbed “Frozen Spider.” While the exact structure of this relationship remains unclear, it is believed that Frozen Spider either operates in tandem with Medusa or as a parent organization.
Additionally, Medusa has repeatedly used the RAMP cybercrime forum to seek partners and access credentials. They’ve shown particular interest in targets located in the United States, Canada, Australia, the UK, Italy, and Germany, underlining a clear strategic preference.
Associated Malware and Tools
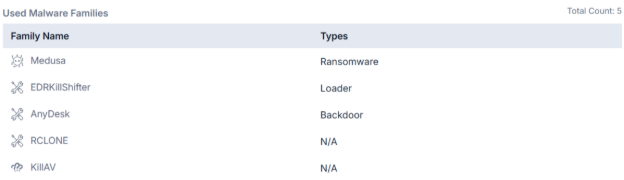
The Medusa group uses a wide range of malware families and tools in its campaigns:
- Medusa Ransomware (primary encryption tool)
- EDRKillShifter (loader)
- AnyDesk (backdoor and RMM tool)
- RCLONE (used for data exfiltration)
- KillAV (for disabling antivirus programs)
Each of these tools contributes to the group’s broader goal: to remain undetected, maintain control, and ensure maximum leverage over victims.
Conclusion
The Medusa ransomware group is far from a typical cyber threat. With a highly organized structure, advanced techniques, and a bold online presence, Medusa uses both technical precision and psychological pressure to extort victims worldwide. Its aggressive tactics—ranging from exploiting public-facing vulnerabilities to disabling security tools—demand a better, proactive defense.
To counter threats like Medusa, organizations should adopt a better threat intelligence service that counters threats like Medusa and mitigate potential threats before they can do more harm.
This is where Cyble steps in. As one of the world’s leading threat intelligence providers, Cyble offers AI-powered platforms like Cyble Vision to monitor ransomware activity, uncover indicators of compromise, and deliver actionable insights. Trusted by enterprises and governments alike, Cyble enables defenders to stay protected from cybercrime actors like Medusa.
Mitigation and Defense Strategies
- Timely Patch Management: Regularly update and patch critical systems to prevent exploitation of known vulnerabilities.
- Enhanced EDR Tools: Use advanced EDR solutions, such as EDRKillShifter and AnyDesk, to monitor and block malicious activities.
- Multi-Factor Authentication (MFA): Implement MFA on all accounts, especially for privileged and remote access.
- Network Segmentation & Backup: Isolate critical data networks and maintain offline, encrypted backups to limit ransomware spread.
- Behavioral Monitoring: Monitor endpoints and network traffic for unusual activity, even if traditional security tools are disabled.
- Phishing Awareness: Train employees to recognize phishing emails to prevent initial access points for Medusa.
- Threat Intelligence: Leverage platforms like Cyble for real-time updates on new ransomware threats.
MITRE Attack Techniques Associated with the Medusa Ransomware Group

- Exploit Public-Facing Applications (T1190): Medusa exploits known vulnerabilities (e.g., CVEs) in publicly accessible applications such as Microsoft Exchange and VPN appliances.
- Phishing (T1566): Initial Access Brokers (IABs) associated with Medusa deploy phishing campaigns to deliver malware.
- Windows Management Instrumentation (T1047): WMI is used to remotely execute code and gather system information from compromised endpoints.
- PowerShell (T1059.001): Scripts automate tasks such as system reconnaissance, lateral movement, and payload deployment.
- Software Deployment Tools (T1072): Tools like PDQ Deploy and IBM BigFix are hijacked to push the ransomware payload across multiple endpoints.
- Obfuscated Files or Information (T1027): Strings in scripts are split, encoded, or hidden to prevent detection by security scanners.
- Encrypted/Encoded Commands (T1027.013): Commands are base64-encoded or encrypted to avoid detection by SIEMs and endpoint defenses.
- Disable or Modify Tools (T1562.001): Endpoint Detection and Response (EDR) and antivirus tools are disabled using custom loaders (e.g., EDRKillShifter).
- Network Service Discovery (T1046): Scans the network using tools like nmap, net view, or scripts to identify active services and open ports.
- System Information Discovery (T1082): Gathers OS version, hardware configuration, installed software, and other host details.