NightSpire is one of the most competent ransomware groups that surfaced in early March 2025. In just a matter of weeks, it has managed to grab the attention of global cybersecurity analysts. With a modern playbook that blends traditional ransomware tactics with aggressive public shaming and precision targeting, the NightSpire ransomware group represents the latest evolution in organized cyber extortion.
The group’s most visible footprint is its onion-based Data Leak Site (DLS), which went live on March 12, 2025. This dark web portal acts as a central hub for the gang’s double extortion strategy. Victims not only have their systems encrypted but also face the threat of their stolen data being published.
The DLS is laid out efficiently—a “Databases” section lists company names, breach dates, data sizes, and countdown timers ticking toward scheduled public disclosures. This creates immense pressure for organizations to pay ransoms before irreversible reputational and legal damage is done.
Operational Infrastructure and Affiliations
Unlike many cybercrime groups maintaining an enigmatic presence, the NightSpire ransomware group has developed a broad communication infrastructure. It utilizes encrypted platforms like ProtonMail, OnionMail, and Telegram to coordinate ransom negotiations and provide updates on pending data dumps. Through these communication channels, the group maintains operational security while also offering a structured interface for communication with victims.
While it is still unclear whether NightSpire operates under a Ransomware-as-a-Service (RaaS) model or as a centralized syndicate, indicators of organized scaling efforts are already evident. On March 14, 2025, an individual identified as xdragon128—a known malware developer—posted a recruitment ad on BreachForums, seeking a “negotiation specialist” and offering a 20% cut of profits. This recruitment effort hints at a potential affiliate structure, similar to models used by established ransomware operations.
Xdragon128, who also goes by the alias Xdragon333, is no newcomer to the cybercrime scene. In 2024, they were reportedly linked to several other threat groups, including Paranodeus, CyberVolk, and DarkAssault. Alongside another operator known as Cuteliyuan, these actors have been associated with both the NightSpire ransomware group and the earlier Rbfs ransomware group, suggesting an overlap in personnel, infrastructure, or possibly even command hierarchy.
NightSpire’s influence isn’t just technical—it’s psychological. Victims report receiving emails through anonymous accounts designed to intensify the pressure during negotiations, often leveraging Telegram channels to orchestrate public shaming campaigns. These platforms serve a dual function: they amplify the urgency of payment while also signaling power and reaching potential new affiliates or adversaries.
Targeted Regions and Sectors

The group’s reach is notably global. By late April 2025, several incidents had spanned a broad set of nations, including the United States, Canada, France, Brazil, Japan, the United Kingdom, India, South Korea, and Argentina, among many others.
In terms of industries, the NightSpire ransomware group has claimed victims in sectors such as healthcare, education, automotive, manufacturing, government and law enforcement, construction, technology, retail, and logistics.
The pattern suggests a strategic preference for industries where data sensitivity and uptime are critical, making organizations more likely to pay to avoid prolonged outages or data exposure.
Tactics, Tools, and Techniques
From a technical standpoint, NightSpire is no less formidable. The group has been actively exploiting CVE-2024-55591, a critical vulnerability in FortiOS firewall appliances, to gain unauthorized access to internet-facing networks. Successful exploitation allows attackers to escalate privileges—often achieving super-admin access—and move laterally across internal systems.
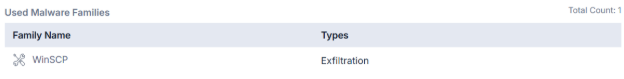
Once inside, the group relies on a combination of legitimate system tools and stealthy execution tactics to stay under the radar. Their toolkit includes WinSCP, MEGACmd, 7-Zip, and Everything.exe, all legitimate programs repurposed for malicious intent. These “living off the land binaries (LOLBins)” allow NightSpire to blend in with normal system activity, reducing the chances of detection by traditional security tools. The use of PowerShell for execution and Windows-native services for lateral movement suggests the group’s operators are highly skilled in exploiting system defaults.
For data exfiltration, the NightSpire ransomware group favors encrypted, cloud-based channels. Data is siphoned from victim networks using WinSCP and MEGACmd and then uploaded to MEGA cloud storage, leveraging asymmetric encrypted non-C2 protocols to avoid triggering intrusion detection systems. Their tactics also include reconnaissance using Everything.exe to index valuable files and network scanners to map internal environments.
Mapping to MITRE ATT&CK Techniques
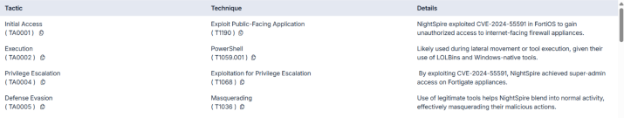
In terms of tactical mapping, NightSpire’s operations align closely with several techniques outlined in the MITRE ATT&CK framework. The group typically gains initial access by exploiting public-facing applications, notably leveraging vulnerabilities in FortiOS (T1190). Once inside, they escalate privileges by exploiting CVE-2024-55591, allowing them to gain super-admin access on compromised systems (T1068). To evade detection, NightSpire employs masquerading techniques (T1036) and executes malicious tasks through legitimate system binaries like WinSCP, blending seamlessly into normal system operations (T1218).
Their discovery and collection tactics involve the use of tools such as Everything.exe to index files and network scanners to map internal infrastructure, matching techniques T1046 and T1083. For lateral movement, the group makes use of common remote services and file transfer protocols, including FTP and possibly Remote Desktop Protocol (RDP) (T1021), to move between systems.
When it comes to data exfiltration, NightSpire relies heavily on MEGACmd, uploading stolen data to cloud storage platforms in a manner consistent with T1567.002 and T1048.002. Their goal is impact, which they achieve by encrypting victim data as part of their double extortion strategy (T1486).
Additionally, threat actor groups such as Storm-1567, UNC4393, and TA2101 have been associated with similar infrastructure or overlapping campaign tactics. However, the precise nature of their connection to NightSpire remains unclear and continues to be a subject of investigation.
Conclusion
What makes NightSpire particularly concerning is its speed of evolution. In less than two months, the group has shifted from pure data extortion to full-scale ransomware encryption, built a functioning leak site, recruited talent publicly, and exploited zero-day vulnerabilities—all while maintaining operational secrecy and an aggressive victim outreach strategy.
To defend against such advanced actors, organizations must adopt a proactive, intelligence-driven security strategy. Cyble, a global leader in threat intelligence, offers AI-powered platforms like Cyble Vision that provide real-time monitoring, vulnerability insights, and deep visibility into threat actor behavior.
Looking for a better threat intelligence service? Schedule a Free Demo today to see how Cyble provides 10X better protection at all times!
Mitigation and Defense Strategies
- Timely Patch Management: Ensure all systems, especially public-facing services like firewalls, VPNs, and email gateways, are regularly updated. Applying patches for known vulnerabilities, such as CVE-2024-55591 in FortiOS, can prevent initial access.
- Endpoint Detection and Response (EDR) Deployment: Use advanced EDR solutions that provide behavioral analysis and threat hunting capabilities. These tools can detect lateral movement, misuse of LOLBins, and unauthorized execution of tools like PowerShell, MEGACmd, and WinSCP.
- Network Segmentation and Access Controls: Use VLANs and strict firewall rules to separate critical infrastructure from less sensitive systems. This limits lateral movement and minimizes damage in case of a breach.
- Multi-Factor Authentication (MFA): Implement MFA across all endpoints, particularly for privileged accounts and remote access solutions like RDP. This adds a critical layer of security even if credentials are compromised.
- Cloud and Data Exfiltration Monitoring: Monitor for unusual traffic to cloud storage services (e.g., MEGA), especially involving tools like MEGACmd. Block or restrict access to known exfiltration channels using proxy filters or data loss prevention (DLP) solutions.
- Implement Threat Intelligence Feeds: Use platforms like Cyble Vision for real-time threat intelligence, IOCs (Indicators of Compromise), and TTPs (Tactics, Techniques, and Procedures) tracking.
MITRE Attack Techniques Associated with the NightSpire Ransomware Group

- Exploit Public-Facing Application (T1190): NightSpire exploited CVE-2024-55591 in FortiOS to gain unauthorized access to internet-facing firewall appliances.
- PowerShell (T1059.001): Likely used PowerShell during lateral movement or for executing tools, leveraging LOLBins and native Windows utilities.
- Exploitation for Privilege Escalation (T1068): By exploiting CVE-2024-55591, NightSpire gained super-admin access on FortiGate firewall appliances.
- Masquerading (T1036): Employed legitimate tools to blend in with system activity, disguising malicious behavior.
- System Binary Proxy Execution (T1218): Used binaries like WinSCP, MEGACmd, and other LOLBins to evade detection.
- Network Service Discovery (T1046): Utilized network scanners to map internal services and infrastructure.
- File and Directory Discovery (T1083): Used Everything.exe to enumerate files and directories on compromised systems.
- Remote Services (T1021): Performed lateral movement using FTP and potentially other remote access methods.
- Remote Desktop Protocol (T1021.001): Used ProtonMail and OnionMail to manage negotiations and internal communications during attacks.
- Email Accounts (T1585.002): Created anonymous or disposable email accounts for phishing, infrastructure acquisition, and social engineering.
- Tool (T1588.002): Leveraged publicly available tools like WinSCP, 7-Zip, Everything.exe, and MEGACmd.