A comprehensive threat profile on OilRig – an Iranian-linked cyberespionage group infamous for its sophisticated campaigns targeting individuals and global entities connected to Iranian interests.
OilRig is a cyber espionage group widely believed to be linked to Iran. It has been active since at least 2015. The group primarily targets individuals and organizations in the Middle East, especially those connected to Iranian interests. OilRig is notorious for its campaigns focused on stealing sensitive information, conducting surveillance, and executing espionage activities.
OilRig is primarily focused on gathering sensitive intelligence through spear-phishing campaigns and advanced infiltration techniques. The group has been implicated in high-profile cyberattacks against a wide array of targets in the Middle East, including government agencies, critical infrastructure, telecommunications, and key regional entities.
OilRig continuously develops and refines its tools to evade detection by security solutions and researchers. In addition to its cyberespionage activities, the group is also responsible for conducting disruptive and destructive operations, including ransomware attacks and data-wiping operations.

Figure 1 – Cyble Vision Threat Library
Country of Origin
OilRig is a cyber espionage group hailing from Iran.
Targeted Nations
OilRig is renowned for its extensive cyber espionage operations, targeting a wide range of countries and regions. Its activities span across Albania, Azerbaijan, Bahrain, China, Egypt, Iraq, Israel, Jordan, Kuwait, Lebanon, Mauritius, Oman, Pakistan, Qatar, Saudi Arabia, Turkey, the UAE, the UK, and the USA.
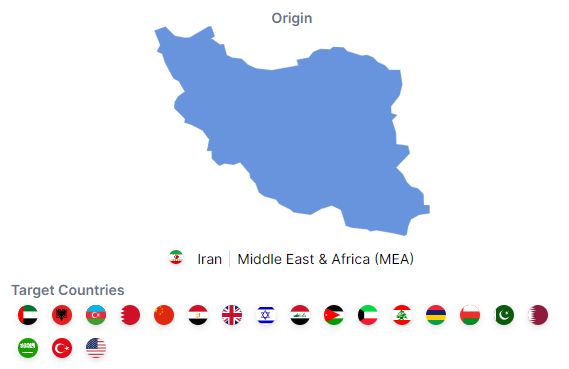
Figure 2 – Origin and Targeted Countries (Source: Cyble Vision)
Aliases
Throughout its decade-long history, OilRig has been known by various aliases, including APT 34, ATK 40, Chrysene, Cobalt Gypsy, Crambus, DEV-0861, EUROPIUM, Evasive Serpens, G0049, Greenbug, Hazel Sandstorm, Helix Kitten, IRN2, ITG13, Scarred Manticore, Storm-0861, TA452, Twisted Kitten, and Yellow Maero.
Targeted Sectors
OilRig has a diverse array of attack vectors and techniques that can be customized for its targets. So far, the group has been observed attacking the following sectors:
- Aerospace & Defense
- BFSI
- Chemicals
- Education
- Energy & Utilities
- Government & LEA
- Hospitality
- IT & ITES
- Technology
- Telecommunication
Links to Other APT Groups
Due to an overlap in infrastructure, researchers suspect that there are links between OilRig and Greenbug.
OilRig Lifecycle
OilRig’s attacks often commence with a spear-phishing email or exploiting public-facing applications that deliver malware to the target system. This malware establishes persistence and subsequently exfiltrates sensitive data from the compromised system. Additionally, OilRig exploits unpatched SharePoint servers to gain access to target systems.
Initial Infection
The threat actors (TAs) behind OilRig strategically leverage spear-phishing emails tailored to various industry-specific themes, such as pricing information and marketing services.
Phishing
OilRig’s phishing campaigns are tailored to bait specific targets, employing spear-phishing attacks to enhance deception and increase the efficacy of their attacks. The figure below shows the phishing email containing a Marketing theme for the attack.
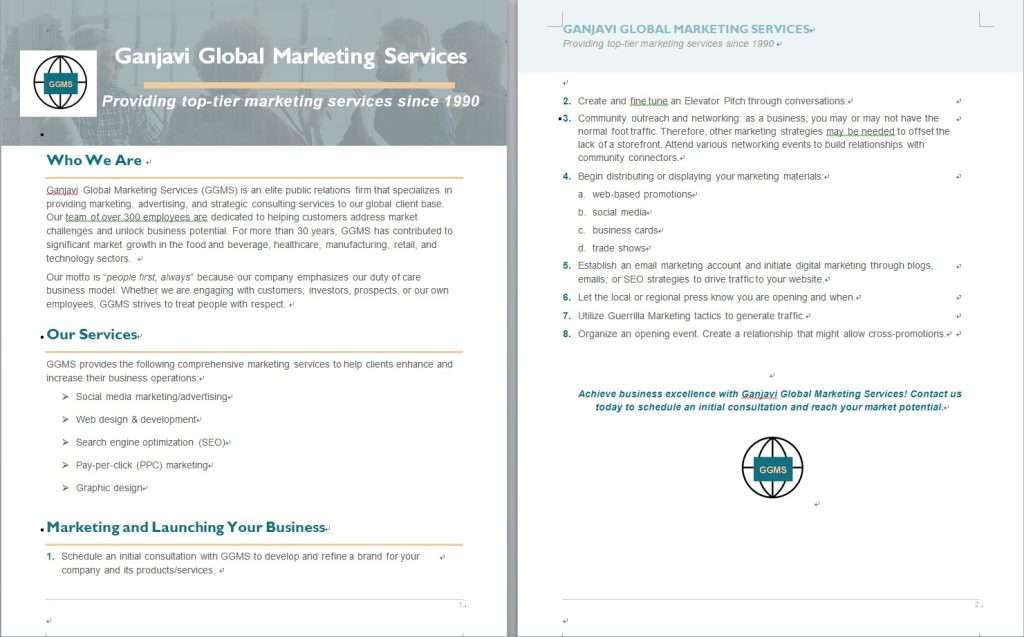
Figure 3 – Decoy Document related to Marketing Services (Source: Nsfocus)
Social Engineering
In late June 2019, FireEye uncovered a LinkedIn phishing campaign orchestrated by APT34. In this campaign, the threat actor masqueraded as a member of Cambridge University to gain victims’ trust, enticing them to open malicious documents and subsequently deploy malware onto their systems.
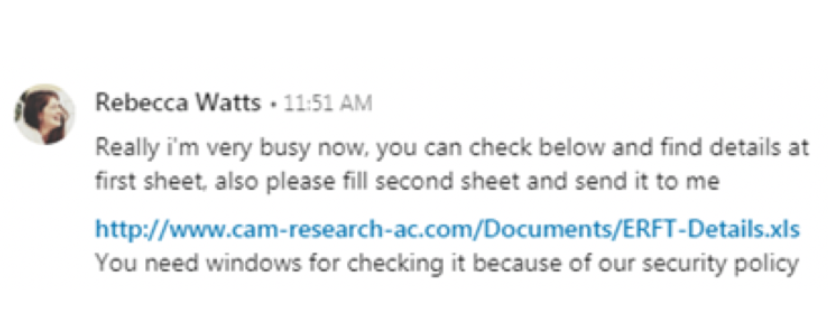
Figure 4 – LinkedIn Message Asking to Download File (Source: Google)
Exploited Vulnerabilities
The OilRig group has exploited various vulnerabilities in its campaigns. Some important vulnerabilities targeted are:
CVE-2019-0604: Microsoft SharePoint Remote Code Execution Vulnerability.
CVE-2017-11882: Microsoft Office Memory Corruption Vulnerability
Persistence
To achieve persistence in the infected system, OilRig drops malicious loaders and VBScript in the victim system and then creates a scheduled task entry for execution. If the initial infection is done by exploiting public-facing applications, then it deploys shellcode on the exploited systems.
Tools used by OilRig
OilRig employs a diverse range of tools as its final payload. These RATs encompass Alma Communicator, BONDUPDATER, certutil, Clayslide, DistTrack, DNSExfitrator, DNSpionage, Dustman, Fox Panel, GoogleDrive RAT, Helminth, ISMAgent, ISMDoor, ISMInjector, Jason, Karkoff, LaZagne, LIONTAIL, LONGWATCH, Mimikatz, MrPerfectInstaller, Nautilus, Neuron, OilRig, OopsIE, PICKPOCKET, Plink, POWBAT, PowerExchange, POWRUNER, PsList, QUADAGENT, RDAT, RGDoor, Saitama, SideTwist, SpyNote RAT, StoneDrill, ThreeDollars, TONEDEAF, TONEDEAF 2.0, TwoFace, VALUEVAULT, Webmask, WinRAR, ZeroCleare, Living off the Land. Researchers can correlate ongoing campaigns by analyzing the IPs and domains associated with past attacks, facilitating the identification and tracking of the group’s activities.

Figure 5 – OilRig Tools (Source: Cyble Vision)
Alma Communicator: The ALMA Communicator Trojan operates as a backdoor utilizing DNS tunneling to exclusively receive commands from adversaries and exfiltrate data. This Trojan specifically retrieves configuration settings from a cfg file initially generated by the Clayslide delivery document.
BONDUPDATER: BONDUPDATER is a PowerShell-based Trojan initially identified by FireEye in mid-November 2017 during OilRig’s targeting of another governmental organization in the Middle East.
Clayslide: ClaySlide documents include malicious macros that present decoy content within spreadsheets while installing a variant of the Helminth backdoor.
DistTrack: DistTrack, also referred to as Shamoon, is a destructive worm that specifically targets a system’s master boot record (MBR). The name “Shamoon” originated from the original payload, which contained debugging information pointing to a programming database file with this distinct name in the path.
DNSExfitrator: The DNSExfitrator tool enables TAs to utilize the DNS over HTTPS (DoH) protocol. Oilrig has extensively employed the DNS protocol for malware communications over an extended period.
DNSpionage: DNSpionage employs DNS tunneling as a covert channel for communicating with the attackers’ infrastructure.
Dustman: Dustman is a form of data wiper malware and is related to ZeroCleare malware.
Fox Panel: A phishing kit that was exposed when OilRig experienced a breach in 2019.
Helminth: Helminth is a backdoor with at least two variants: one written in VBScript and PowerShell, delivered via macros embedded in Excel spreadsheets, and another variant that is a standalone Windows executable.
ISMAgent: ISMAgent employs a DNS tunneling protocol that closely resembles ISMDoor, previously associated with a group known as Greenbug.
ISMDoor: ISMDoor is an information-stealing RAT with an encrypted configuration that includes primary and secondary C&C domains, identifiers, timeouts, and flags. Subsequent C&C commands can modify these settings. A substitution cipher is utilized to decrypt the configuration as required.
ISMInjector: OilRig developed the ISMInjector Trojan specifically to facilitate the installation of the ISMAgent backdoor.
Karkoff: Cisco Talos discovered an undisclosed malware developed in .NET. During analysis, the malware author left two distinct internal names in plaintext: ‘DropperBackdoor’ and ‘Karkoff.’ We opted to adopt the latter as the malware’s name, considering it to be more distinctive and less generic.
Karkoff: MediaPl is a backdoor designed to transmit encrypted communications to its C&C server. It disguises itself as Windows Media Player, a widely used application for storing and playing audio and video files.
Mimikatz: Mimikatz offers a comprehensive suite of tools tailored for gathering and leveraging Windows credentials on targeted systems. These tools enable the retrieval of various credentials such as cleartext passwords, Lan Manager hashes, NTLM hashes, certificates, and Kerberos tickets. While these tools generally run successfully on Windows versions from XP onwards, their functionality may be somewhat restricted on Windows 8.1 and later versions.
LaZagne: LaZagne is an open-source post-exploitation tool designed to retrieve stored passwords from a system. It includes modules for Windows, Linux, and OSX, though it primarily targets Windows systems. LaZagne is openly accessible on GitHub for public use.
LIONTAIL: The LIONTAIL framework comprises advanced custom loaders and shellcode payloads residing in memory. LIONTAIL implants leverage undocumented features of the HTTP.sys driver to extract payloads from incoming HTTP traffic. Various observed variants of LIONTAIL-related malware indicate that Scarred Manticore generates bespoke implants for each compromised server. This approach enables malicious activities to camouflage within legitimate network traffic, making detection more challenging.
LONGWATCH: LONGWATCH is a keylogger that records keystrokes and logs them to a file named log.txt in the Windows temporary folder.
SideTwist: SideTwist is a C-based backdoor equipped with functionalities such as downloading and uploading files, as well as executing shell commands.
Neuron: The Neuron backdoor comprises both client and server components, both developed using the .NET framework with shared codebase elements. The Neuron client infects and extracts sensitive data from victim endpoints. Meanwhile, the Neuron server targets network infrastructure like mail and web servers, functioning as a local command and control (C&C) system for the client component.
Nautilus: Nautilus closely resembles Neuron in its focus on targeting mail servers and the method of client communications. This malware is named Nautilus, derived from its embedded internal DLL name “nautilus-service.dll”, which shares similarities with Neuron. The Nautilus service actively listens for HTTP requests from clients, enabling it to handle tasking requests such as executing commands, deleting files, and writing files to disk.
PICKPOCKET: PICKPOCKET is a credential theft tool designed to extract website login credentials from Chrome, Firefox, and Internet Explorer, saving them to a file. This tool was first identified during a Mandiant incident response in 2018 and has since been exclusively associated with the activities of OilRig.
Plink: Plink, also known as PuTTY Link, is a widely used utility for tunneling RDP sessions. It facilitates secure shell (SSH) network connections between systems and supports flexible configuration of source and destination ports.
PsList: PsList is a tool designed to display a comprehensive list of processes currently active within the operating system. It is an integral component of the SysInternals Tools suite.
RDAT: RDAT is a backdoor employed by OilRig specifically aimed at the telecommunications sector.
Saitama: The Saitama backdoor utilizes the DNS protocol for its C&C communications, which offers a stealthier approach compared to traditional methods like HTTP. Additionally, the actor employs techniques such as compression and extended random sleep intervals to camouflage malicious traffic within legitimate network activity.
SpyNote RAT: SpyNote RAT is a group of malicious Android applications. The SpyNote RAT builder tool enables the creation of malicious apps incorporating the malware’s functionalities.
TONEDEAF: TONEDEAF is a backdoor that communicates with C&C servers via HTTP or DNS. It supports various commands, such as collecting system information, uploading and downloading files, and executing arbitrary shell commands. Despite its capability to communicate through DNS requests to its predefined C&C server, TONEDEAF remains versatile in its communication methods.
Network Activities
OilRig’s primary objective is to ensure covert C&C communication by employing a range of techniques and tools. Their malware communicates with C2 servers through both HTTP and DNS queries. In several campaigns, OilRig has utilized targeted exchange servers to relay communications discreetly. Additionally, they have employed HTPSnoop implants for clandestine network communication with C&C infrastructure. OilRig also utilizes protocol tunneling to enhance the stealthiness of its network communications.
Conclusion
OilRig’s campaigns are characterized by sophisticated strategies aimed at achieving stealthy C&C communication. Utilizing diverse techniques such as HTTP and DNS for C&C channels, along with leveraging targeted exchange servers, OilRig ensures effective and covert operations. The deployment of HTPSnoop implants underscores their commitment to clandestine network communication. With protocol tunneling enhancing their tactics, OilRig demonstrates a persistent pursuit of evasive measures in cyber espionage. These efforts solidify OilRig’s reputation for adeptness in maintaining covert operations, making it a significant player in the cybersecurity landscape focused on the Middle East and beyond.
Recommendations:
To mitigate the threat posed by OilRig, consider the following recommendations:
Patch Management: Regularly update and patch all software and systems to mitigate vulnerabilities commonly exploited by OilRig.
Email Security: Enhance email security measures to detect and block spear-phishing attempts, a common initial attack vector used by OilRig.
Network Monitoring: Implement robust network monitoring to detect suspicious activities, especially DNS tunneling and unusual HTTP traffic patterns associated with OilRig’s operations.
Endpoint Protection: Deploy advanced endpoint protection solutions that include behavior-based detection to identify and block malicious activities associated with OilRig malware.
Access Control: Implement the principle of least privilege and enforce strong authentication mechanisms to limit access to sensitive systems and data.
Incident Response: Develop and regularly test an incident response plan specific to cyber espionage threats like OilRig to ensure swift detection, containment, and mitigation of attacks.
Threat Intelligence: Use threat intelligence sources to stay informed about OilRig’s latest tactics, techniques, and procedures (TTPs) to enhance proactive defense measures.
Employee Training: Conduct regular cybersecurity awareness training for employees to educate them about phishing techniques and the importance of vigilance in detecting suspicious activities.
MITRE attack Techniques Associated with OilRig
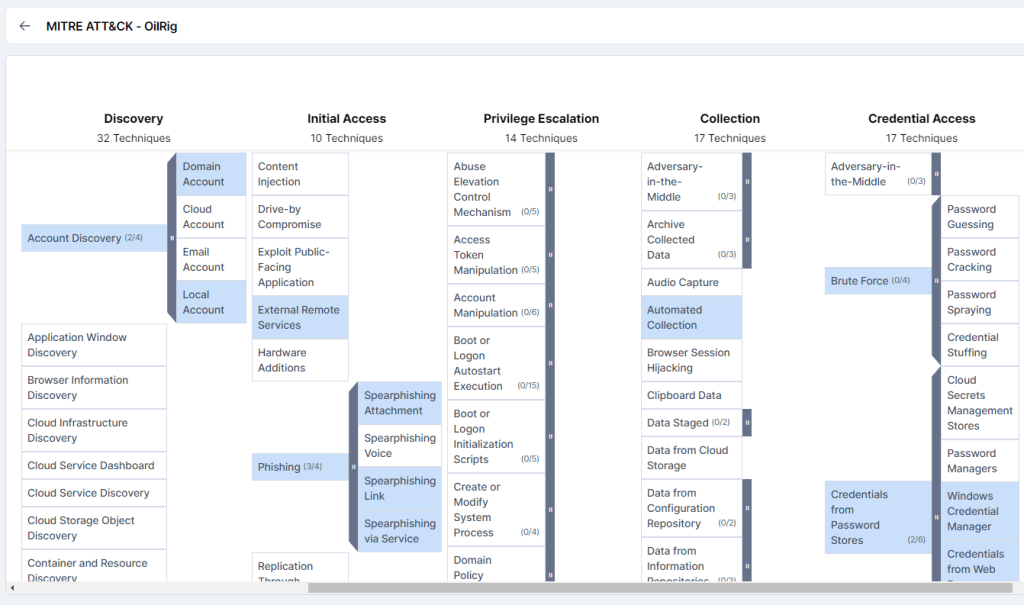
Figure 6 – MITRE ATT&CK (Source: Cyble Vision)
Spearphishing Attachment (T1566.001): OilRig commonly employs spear-phishing emails containing malicious attachments as the initial stage of their attacks.
Spearphishing Link (T1566.002): The OilRig group also distributes its payloads by sending spear-phishing emails with malicious links.
User Execution (T1204): OilRig employs social engineering tactics to persuade users to execute its malicious payloads.
Scheduled Task (T1053.005): The OilRig group utilizes scheduled tasks to maintain persistence on compromised systems.
Exfiltration Over Alternative Protocol (T1048): The OilRig group might exfiltrate stolen data using alternative protocols as a tactic to evade detection.
Data from Local System (T1005): During their operations, OilRig collects sensitive information from local systems.