The Play ransomware group, also known as Playcrypt, has been an active and persistent cybercriminal entity since at least 2022. Specializing in double-extortion ransomware attacks, Play has targeted various sectors across North America, South America, and Europe, causing disruption to organizations worldwide. Known for its meticulous operational methods, the Play ransomware group exploits vulnerabilities to infiltrate systems, encrypt data, and exfiltrate sensitive information to extort ransom payments.
Play’s reach has extended across a wide array of countries and regions, with notable activity in both developed and new markets. The group has affected entities in North America, South America, and Europe, targeting businesses, critical infrastructure, government agencies, and various other sectors. Countries like the United States, United Kingdom, France, Germany, Canada, Australia, and Argentina have been frequent targets of Play’s ransomware campaigns, with the group showing no hesitation in going after critical sectors.
Targeted Countries and Industries

Cyble Vision Threat Library (Source: Cyble Vision)
Some of the key nations targeted by Play include:
- United States (US)
- Canada (CA)
- United Kingdom (GB)
- Germany (DE)
- France (FR)
- Australia (AU)
- Argentina (AR)
- Switzerland (CH)
- South Korea (KR)
- South Africa (ZA)
Play is also noted for its attacks across diverse sectors, affecting industries like aerospace and defense, healthcare, education, government, and telecommunications. Critical sectors such as energy, utilities, transportation, and logistics are also at high risk, given their reliance on interconnected, often vulnerable systems.
The Double-Extortion Model
Play ransomware operates using a double-extortion strategy. This method involves not only encrypting a victim’s data, thereby rendering their systems inoperable, but also exfiltrating sensitive information. This two-pronged approach increases the pressure on the victim to pay the ransom. While encryption locks the data, the threat of having sensitive or confidential information leaked or sold amplifies the extortion demands.
One of the distinguishing features of Play’s ransom notes is their lack of immediate ransom demands. Instead, victims are directed to contact the attackers via email. This covert approach adds an additional layer of secrecy to the group’s operations, keeping them under the radar longer than other ransomware actors that might be more direct in their demands.
Tools and Tactics Used by Play Ransomware Group
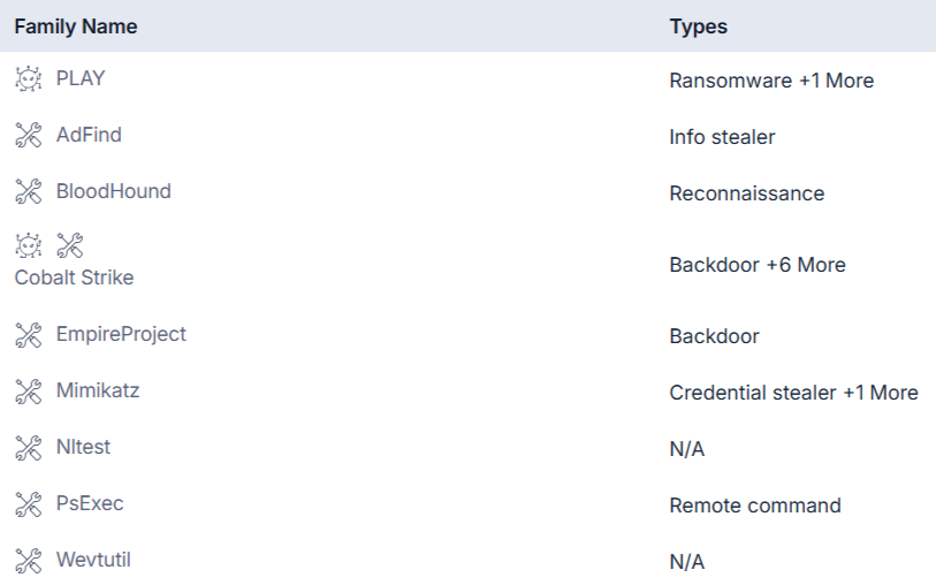
Tools and Tactics Used by Play Ransomware (Source: Cyble Vision)
Play ransomware actors employ a sophisticated arsenal of tools and techniques, leveraging various malware families and attack methods to ensure their success. Their toolkit enables them to compromise systems, escalate privileges, exfiltrate data, and avoid detection. Notably, Play has utilized the following tools:
- Play Ransomware: The group’s namesake, which encrypts victim data.
- AdFind: An Active Directory query tool used to gather critical information about the victim’s network infrastructure.
- BloodHound: A reconnaissance tool used for Active Directory enumeration and network mapping.
- Cobalt Strike: A popular backdoor tool commonly used for post-exploitation activities, including lateral movement within networks.
- EmpireProject: A PowerShell-based backdoor tool designed for system exploitation.
- Mimikatz: A well-known credential stealer that allows Play to harvest passwords and authentication tokens for further network penetration.
- PsExec: A remote execution tool that facilitates the lateral movement of ransomware across compromised networks.
- Wevtutil: A command-line tool used to erase Windows Event Logs, covering the group’s tracks during and after an attack.
These tools are employed at various stages of the attack lifecycle, from initial access to data exfiltration and encryption. For instance, Play actors use AdFind to probe the network for sensitive data and identify vulnerabilities in the target’s Active Directory infrastructure. Once they have gathered enough information, they deploy Cobalt Strike and EmpireProject for lateral movement and to establish persistence within the system.
In addition, Play uses advanced anti-detection techniques to evade antivirus and endpoint security measures. Tools like GMER and IOBit are used to disable or bypass security mechanisms, including Microsoft Defender and other antivirus programs. The group also frequently leverages PowerShell scripts to manipulate security software and disable logging, making it more challenging for defenders to trace their actions.
Recent Activity and Impact
The Play ransomware group has maintained a strong operational presence, with notable activity in 2023 and 2024. According to the FBI, as of October 2023, approximately 300 entities had been identified as victims of Play. Particularly concerning is Play’s focus on critical infrastructure and government entities, as these sectors are often ill-equipped to deal with the sophisticated nature of these attacks.
In Australia, the first recorded instance of Play activity was observed in April 2023, and subsequent incidents continued through November 2023. This trend suggests a growing global reach, with Play rapidly expanding their target base across different regions.
Conclusion
As the Play ransomware group continues to advance, businesses and government entities must remain vigilant in strengthening their defense mechanisms. By staying informed about the tactics and tools used by cybercriminals like Play, organizations can better protect their systems and data.
To enhance their cybersecurity posture, leveraging advanced threat intelligence is essential. Cyble, with its cutting-edge AI-powered cybersecurity platforms, such as Cyble Vision, offers critical insights and real-time threat monitoring to help businesses stay protected. By utilizing Cyble’s comprehensive solutions, organizations can better protect against ransomware attacks and other malicious activities.
Defensive Measures and Recommendations
Some key recommendations for mitigating threats like the Play ransomware group include:
- Regular Patch Management: Ensuring all systems and software are up to date can reduce the risk of exploitation via known vulnerabilities.
- Employee Training: Since phishing remains a common entry point, organizations should invest in comprehensive cybersecurity awareness programs for their employees.
- Endpoint Protection: Advanced endpoint detection and response (EDR) solutions should be deployed to identify and block ransomware at early stages.
- Network Segmentation: Isolating critical systems can prevent the lateral movement of ransomware across an entire organization.
- Backups: Regular, offline backups of critical data are essential to minimize the impact of ransomware attacks and facilitate quick recovery without succumbing to ransom demands.










