The RALord is a new ransomware group identified as early as March 25, 2025. The group operates within the broader infrastructure of NOVA RaaS, a platform that enables affiliates to launch ransomware campaigns in exchange for a share of the profits. The revenue model is enticing: affiliates retain 85% of the revenue, while the NOVA platform takes a 15% cut. This affiliate-driven structure incentivizes widespread adoption, enabling rapid proliferation of attacks by actors with varied levels of skill.
However, what sets RALord apart isn’t just its business model—it’s the menu of services it offers. Unlike many RaaS operations, RALord provides standalone access to its encryption tool without requiring full subscription to the platform. In addition, it engages in data sales, promotes its activities across Tor-based networks, and maintains an aggressive data leak site (DLS) showcasing victims and stolen data.
RALord’s extortion strategy goes beyond basic file encryption. It applies multi-layered pressure on victims by combining operational disruption, reputational damage, and public humiliation. On their DLS, the group publishes in-depth reports about each attack, often highlighting how they bypassed existing security controls, naming the specific security products that failed, and pointing out poor cybersecurity hygiene within the organization.
Victim profiles on the DLS often include:
- Screenshots of encrypted directories (marked by the “.nova” or “.RALord” extension)
- Listings of internal network structures,
- Sample files proving data theft,
- And in some cases, the implications of supply chain risks affect partners and clients.
These tactics aim to shame organizations into compliance, making the consequences of non-payment seem more damaging than the ransom itself.
Targeted Sectors and Geographic Focus

RALord does not confine its operations to a single industry or region; instead, it targets a broad range of high-value sectors and vulnerable organizations worldwide. The group has focused its efforts on industries such as healthcare, education, hospitality, IT and IT-enabled services, media and entertainment, construction, and agriculture. These sectors are often rich in sensitive data and are typically reliant on continuous operations, making them prime targets for ransomware attacks.
Geographically, RALord’s activities span several countries, including Norway, Portugal, the United Arab Emirates, Saudi Arabia, Taiwan, Brazil, Spain, France, and Argentina. This global footprint demonstrates a calculated approach, selecting regions with well-developed digital infrastructures and critical economic sectors.
Among the most recent victims are ARRCO AS in Norway (media and entertainment), Newhotel Software SA in Portugal (IT and ITES), Al Hejailan Group in Saudi Arabia, HASBCO Medical Supplies in the UAE (healthcare), and Ecole Centrale de Nantes in France (education). The selection of both the industries and countries indicates a strategic targeting methodology, focusing on entities where the operational and reputational impact of a ransomware attack is likely to be severe.
Technical Details: Two Variants in Play
The RALord ransomware group uses two primary types of ransomware payloads:
- The “.nova” variant, which is widely distributed by affiliates.
- A more advanced Rust-based variant developed in-house by RALord, which appends the “.RALord” extension to encrypted files.
Both variants are accompanied by ransom notes instructing victims to reach out via secure messaging apps, most commonly qTox—an encrypted peer-to-peer communication tool known for its resistance to surveillance. Interestingly, RALord maintains a public blog (accessible via Tor) that details ongoing updates to their tools, signaling a continued investment in innovation and scalability.
Possible Affiliations and Recruitment Activities
While no definitive link has been established, researchers have noted similarities between RALord and the older RAWorld group, both in terms of code structure and messaging tone. Adding to this intrigue is a recruitment post spotted on the RAMP forum in March 2025, authored by a user named “ForLord.” The ad sought candidates with experience in:
- Rust and Python programming
- Exploiting CVEs
- Network penetration
- Bypassing security measures
Although the identities of RALord and ForLord haven’t been definitively linked, the parallels in naming conventions and technical goals suggest a possible connection.
Conclusion
The RALord ransomware group poses a serious threat due to its technologically advanced and strategically multi-layered approach. Unlike many cybercriminal groups relying on basic tools, the RALord ransomware group uses custom-built ransomware, detailed victim profiling, and data exposure to maximize impact. Their active recruitment and technical tactics suggest a well-resourced, scaling operation.
As ransomware becomes a profit-driven business model, proactive cybersecurity is essential. Cyble helps organizations stay protected with its AI-powered threat intelligence, providing tools to defend against cyber threats like RALord and ensuring businesses remain protected in the cyber landscape.
Mitigation and Defense Strategies
- Strengthen Endpoint and Network Defenses: Deploy advanced EDR solutions and enforce network segmentation to detect and contain malicious activity, especially lateral movement and unauthorized encryption.
- Patch Critical Vulnerabilities Promptly: Prioritize patching of known CVEs exploited by RALord, particularly in VPNs, firewalls, and remote access systems, to close entry points.
- Use Multi-Factor Authentication (MFA): Secure all remote access points with MFA and limit access to essential users and services to reduce exposure.
- Maintain Offline, Tested Backups: Ensure regular, encrypted backups are stored offline or in isolated environments, and routinely test restoration procedures to avoid ransom payments.
- Leverage Threat Intelligence Platforms: Utilize platforms like Cyble Vision for real-time monitoring, IOCs, and dark web activity tracking to stay protected.
MITRE Attack Techniques Associated with RALord Ransomware Group
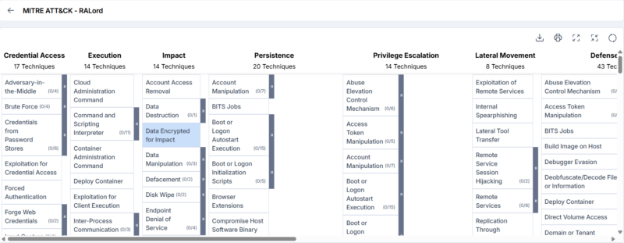
- Execution (TA0002): Leverages OS APIs (e.g., CreateProcess, fork) for process creation and system-level operations; may use syscalls to bypass user-mode hooks.
- Persistence (TA0003): Hijack Execution Flow (T1574): Alters program/library execution paths via registry or file path poisoning for recurring malicious execution.
- Privilege Escalation (TA0004): Hijack Execution Flow (T1574): Same method as used in persistence to gain elevated privileges.
- Defense Evasion (TA0005): Impair Defenses (T1562): Disables security tools, monitoring, and routine operations (e.g., updates, shutdowns).
- Discovery (TA0007): File and Directory Discovery (T1083): Searches common file paths and reads .ini files to locate sensitive content.
- Command and Control (TA0011): Application Layer Protocol (T1071): Uses common protocols to blend with normal traffic and avoid detection.
- Resource Development (TA0042): Email Accounts (T1585.002): Communicates with victims and affiliates via qTox, Session, and Jabber.