Since its inception in mid-2023, RipperSec has carved a name for itself as one of the most influential players in the world of hacktivism. The group is known for its politically motivated cyber operations that span globally.
Primarily motivated by pro-Palestinian sentiments, this group has quickly established a reputation for executing Distributed Denial of Service (DDoS) attacks, website defacements, and data breaches targeting government institutions, educational entities, and organizations perceived to be aligned against their cause.
Origins and Identity
RipperSec likely hails from Malaysia and operates predominantly across the Asia-Pacific region. The group first appeared on the cyber scene in June 2023 and rapidly gained traction, largely via its presence on Telegram, where it boasts a community of over 2,000 active members.
This platform has been serving both as a hub for communication and a recruitment ground, fueling their operations through collective participation rather than relying on complex, centralized infrastructure. The group is also known by several aliases, including RipperSecGroup, RipperSecIO, Satanofchacker, Suni, and TrashDono.
Ideological and Operational Focus
RipperSec is distinguished not only by its hacktivist ethos but also by its consistent focus on geopolitical targets. Its campaigns are particularly anti-Israel and anti-India in nature, reflecting wider regional conflicts and political stances.
The group has claimed responsibility for nearly 200 DDoS attacks, many directed at Israeli government and private sector websites. Their operational footprint extends beyond the Middle East, affecting countries like the United Arab Emirates, Australia, Canada, and the United States, among others.
This broad targeting suggests that RipperSec’s activities are not isolated to local grievances but are part of a larger effort to influence international narratives and apply pressure through cyber means.
Tools and Techniques

Central to RipperSec’s cyber arsenal is a proprietary DDoS tool named MegaMedusa, which has been adapted to security detection since its first iteration. Developed by the group’s administrator known as “TrashDono” or “KudaGila,” MegaMedusa is designed to circumvent web defenses such as Cloudflare and DDoS-Guard, enabling the group to sustain prolonged and effective disruption campaigns.
In addition to DDoS attacks, the group has expanded its tactics to include data breaches and unauthorized access to sensitive administrative portals. By mid-2024, RipperSec had demonstrated its capability to leak databases and manipulate backend systems.
Decentralized Resilience and Alliances
Despite the reported death of its leader in July 2024, RipperSec’s activities have not waned, indicating a decentralized and distributed command structure. This resilience suggests that while key figures might emerge, the group’s momentum is sustained through collective effort and possibly autonomous cells.
RipperSec has also aligned itself with other politically motivated hacking groups, notably pro-Russian entities such as NoName057(16) and the People’s Cyber Army. These collaborations have allowed them to pool resources, exchange intelligence, and coordinate attacks targeting Ukrainian infrastructure and entities perceived as adversaries.
Target Profiles and Sectors
The group’s targets span a diverse set of industries. These include:
- Government and Law Enforcement Agencies: Political and diplomatic entities often represent key targets, reflecting the group’s strategic focus on influencing government narratives.
- Education Sector: Universities and educational institutions, especially those seen as supporting opposing geopolitical interests, have frequently been victimized.
- Critical Infrastructure and Energy: Attacks on these sectors aim to disrupt essential services and create a broader societal impact.
- Media and Entertainment: By targeting these sectors, RipperSec seeks to challenge public perception and influence information dissemination.
- Financial Services and IT: Disrupting these industries can cause economic impact and undermine confidence in digital infrastructure.
Attack Strategies and Techniques
RipperSec’s approach is multifaceted, involving:
- Exploiting vulnerabilities in public-facing applications or compromising legitimate credentials to infiltrate networks.
- Leveraging scripting and command interpreters to execute malicious payloads.
- Using stolen credentials to maintain prolonged access, often without deploying malware to evade detection.
- Abusing account privileges, including inactive or dormant accounts, to move laterally within networks.
- Gathering information through screen captures or mining sensitive data from poorly secured repositories.
- Executing denial of service attacks, service stoppages, and website defacements to disrupt operations and amplify their message.
Their use of legitimate credentials rather than relying solely on malware reduces their visibility, complicating detection and mitigation efforts.
Conclusion
RipperSec exemplifies the next generation of hacktivists, combining ideology with advanced technical skills, posing a continuous threat to world organizations. To effectively counter such threats, organizations must implement multi-layered security measures, including perimeter defenses, timely patching, anomaly detection, and strict credential management.
Cyble’s AI-native cybersecurity platform offers cutting-edge threat intelligence and autonomous response capabilities, empowering defenders to stay protected from modern cyber threats.
Cyble’s External Threat Profile Report provides critical insights into vulnerabilities, misconfigurations, data leaks, and dark web exposure, helping organizations quickly understand their unique risk posture, detect potential attacks, and take proactive steps to safeguard their assets and ensure business continuity.
Get Cyble’s External Threat Profile Report to uncover vulnerabilities, misconfigurations, data leaks, and dark web risks today!
Defense and Mitigation Strategies
- Use multi-layered security with firewalls, IDS/IPS, and web application firewalls.
- Regularly patch vulnerabilities in all public-facing systems.
- Enforce strong credential policies, including MFA and frequent password changes.
- Monitor for unusual activity to detect breaches early.
- Limit user privileges and disable inactive accounts.
- Deploy DDoS protection to defend against attacks like MegaMedusa.
- Monitor for data leaks and dark web exposure.
- Have an incident response plan that uses real-time threat intelligence like Cyble’s platform.
MITRE ATT&CK Techniques Associated with the RipperSec Group
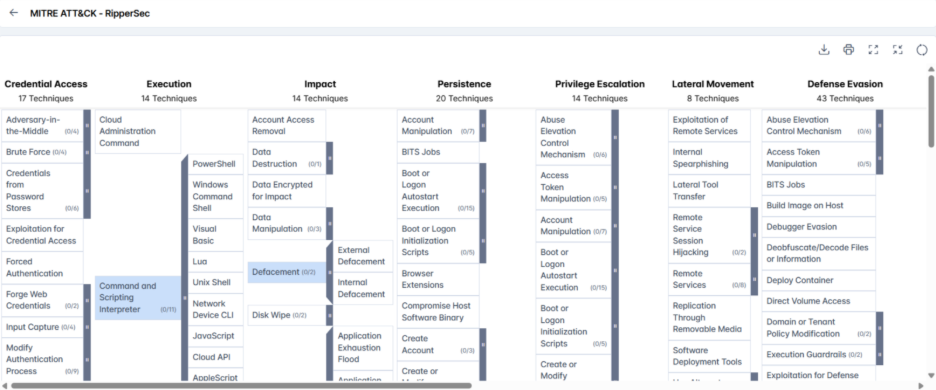
- Valid Accounts (T1078): Adversaries use stolen or inactive credentials to bypass access controls, evade detection, and escalate privileges across local, domain, and cloud accounts for lateral movement.
- Exploit Public-Facing Application (T1190): Adversaries exploit vulnerabilities or misconfigurations in internet-facing systems and edge devices to gain further access, including cloud APIs or host escape, often leveraging OWASP Top 10 and CWE Top 25 flaws.
- Command and Scripting Interpreter (T1059): Adversaries abuse command-line and scripting tools like PowerShell, Unix Shell, Python, and JavaScript to execute commands via payloads, interactive shells, or remote services.
- Valid Accounts (T1078): Using compromised or inactive credentials, adversaries maintain persistence and enable lateral movement through overlapping permissions.
- Screen Capture (T1113): Taking screenshots via native utilities or remote access tools to gather information during operations.
- Data from Information Repositories (T1213): Mining sensitive data like documents, credentials, and source code from collaboration platforms (e.g., SharePoint, Slack) exposed by misconfigurations or public access.
- Gather Victim Identity Information (T1589): Collecting personal and authentication data through phishing, probing, or public sources to aid targeting, social engineering, or initial access.
- Gather Victim Network Information (T1590): Obtain network details useful for further targeting.










