Overview
TeamPCP is a cloud-focused cybercriminal operation that emerged as a large-scale exploitation platform in late 2025. Also tracked under the aliases of DeadCatx3, PCPcat, PersyPCP, and ShellForce, the group has been observed conducting systematic campaigns against exposed cloud infrastructure worldwide.
Rather than relying on zero-day exploits, TeamPCP differentiates itself through automation, integrating known vulnerabilities and common cloud misconfigurations into a scalable, self-propagating exploitation framework.

Beginning in late 2025, the group launched scanning activity targeting exposed Docker APIs, Kubernetes control planes, Ray dashboards, and Redis services. Once access is obtained, compromised systems are folded into a distributed network used for proxying traffic, conducting further scans, hosting command-and-control (C2) infrastructure, and generating illicit revenue through ransomware deployment and cryptomining.
Operational Model
TeamPCP’s operations are structured around cloud-native exploitation. Instead of exploiting end-user endpoints, the group prioritizes exposed administrative services and container orchestration environments. Observed attack chains typically begin with automated scanning for externally accessible services that lack authentication or are weakly secured.

Misconfigured services abused by the group include:
- Docker Remote API endpoints
- Kubernetes API servers and kubelets
- Ray dashboards
- Redis instances
Following initial access, TeamPCP conducts horizontal pivoting within the compromised environment. Activities observed post-compromise include:
- Data exfiltration
- Tunneling and proxy deployment
- Ransomware execution
- Cryptocurrency mining
- Deployment of additional scanning nodes
- Establishment of persistent C2 infrastructure
The operation’s strength lies in orchestration and automation rather than exploit development. Known weaknesses are weaponized at scale, enabling rapid expansion across exposed cloud environments.
Targeting Countries and Industries
Observed targeting includes the United Arab Emirates, Canada, South Korea, Serbia, the United States, and Vietnam, reflecting a geographically diverse footprint that suggests opportunistic exploitation of exposed infrastructure rather than politically motivated or country-specific campaigns.
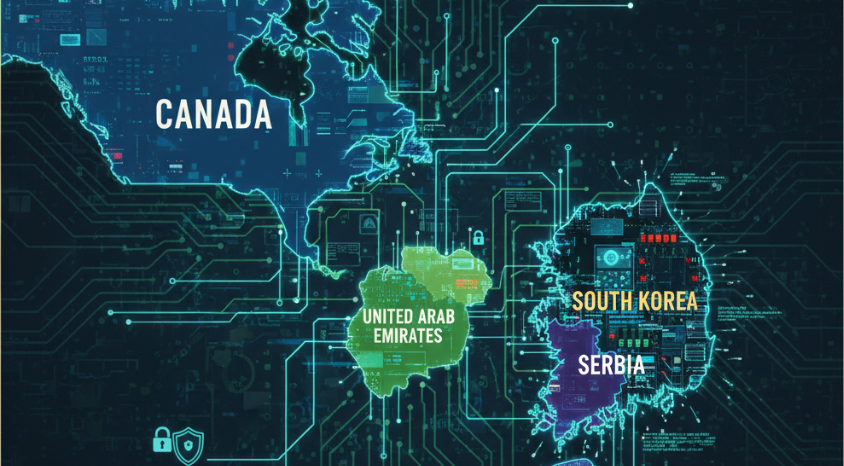
In terms of industry focus, TeamPCP has impacted organizations operating in Banking, Financial Services, and Insurance (BFSI), Consumer Goods, and Professional Services.
These sectors commonly rely on scalable, cloud-based environments and externally accessible services, making them particularly susceptible to automated scanning, misconfiguration abuse, and monetization-driven attacks such as ransomware deployment and unauthorized cryptomining.
Malware and Tooling
TeamPCP employs a combination of open-source and dual-use tools to support tunneling, exploitation, and monetization activities, primarily leveraging four malware and tooling families.
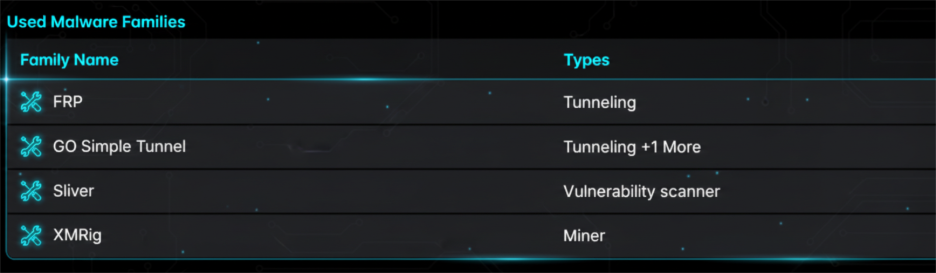
FRP
FRP (Fast Reverse Proxy) is used to create reverse proxy tunnels, providing persistent remote access to compromised systems, while GO Simple Tunnel facilitates traffic relay and maintains communication between infected infrastructure and operator-controlled systems.
Sliver
Sliver, an open-source, cross-platform adversary simulation and C2 framework originally designed for red team and penetration testing, enables command-and-control over Mutual TLS (mTLS), WireGuard, HTTP(S), and DNS, with dynamically compiled implants that can include unique X.509 certificates for each build, enhancing stealth and operational security.
Although designed for legitimate security testing, Sliver has been adopted by multiple threat actors. It enables operators to generate customized implants, establish encrypted C2 channels, and coordinate multi-operator campaigns.
Threat actors have previously used Sliver to exploit vulnerabilities in externally exposed devices such as VPN appliances, including Ivanti Connect Secure systems, to deploy ransomware payloads. By generating implants with unique certificates and leveraging encrypted channels, attackers can maintain stealthy and resilient C2 communications.
Other actors observed using Sliver include:
- APT29 (Last Seen: 08-Jan-2026)
- Head Mare (Last Seen: 09-May-2025)
- TA551 (Last Seen: 01-Oct-2021)
- TeamPCP (Last Seen: 10-Feb-2026)
XMRig
XMRig is an open-source Monero mining application frequently abused by cybercriminals. TeamPCP deploys XMRig on compromised hosts to mine Monero using the victim’s CPU resources without authorization.
Threat actors typically deliver XMRig by exploiting exposed services or bundling it with secondary payloads. Once deployed, the miner operates silently in the background, generating cryptocurrency revenue.
Other threat actors observed using XMRig include:
- TeamPCP (Last Seen: 10-Feb-2026)
- APT4 (Last Seen: 27-Jun-2025)
- APT41 (Last Seen: 23-Jul-2024)
- Kinsing (Last Seen: 13-Dec-2021)
- Pacha Group (Last Seen: 01-May-2019)
- ironern440
Tactics, Techniques, and Procedures (TTPs)
TeamPCP gains initial access by exploiting externally accessible services, including remote management interfaces, cloud control panels, and container environments, often taking advantage of exposed systems or compromised credentials. The group also targets Internet-facing applications with software flaws, misconfigurations, or weak access controls, allowing them to infiltrate cloud-hosted services and, in some cases, reach underlying hosts.
Once inside, TeamPCP maintains persistence by scheduling recurring execution of malicious tasks, using command-line and scripting environments to run payloads, download additional tools, and perform system reconnaissance. The group further manipulates container management interfaces to deploy compromised containers, execute commands within them, and pivot to other systems within the environment.
Conclusion
TeamPCP is a highly automated cloud-focused cybercriminal group combining ransomware, cryptomining, tunneling, and proxy infrastructure to exploit misconfigured cloud environments. Active as of 2026, the group converts compromised systems into distributed infrastructure for scanning, command-and-control, ransomware deployment, and cryptocurrency mining.

Organizations can strengthen defenses against such threats using Cyble’s AI-powered threat intelligence, which provides real-time visibility, threat detection, and actionable insights. Schedule a demo to see how Cyble helps protect cloud and enterprise environments.
Recommendation and Mitigation Strategies
- Secure Cloud and Container Environments: Regularly audit and harden cloud services, APIs, and container orchestration platforms to prevent unauthorized access. Disable unused endpoints and enforce strong authentication.
- Patch and Update Systems: Ensure all cloud-hosted applications, container platforms, and infrastructure are updated promptly to address known vulnerabilities and misconfigurations.
- Limit Administrative Access: Apply least-privilege principles for user and service accounts, and regularly review permissions to reduce the impact of compromised credentials.
- Monitor Network and Cloud Activity: Implement continuous monitoring for unusual outbound traffic, proxy usage, or container behavior that could indicate lateral movement or tunneling.
- Deploy Threat Detection and Response Tools: Utilize AI-driven threat intelligence platforms, endpoint monitoring, and anomaly detection to identify and respond to ransomware, cryptomining, or C2 activity in real time.
- Backup and Recovery Planning: Maintain offline, immutable backups of critical cloud and on-premises data to ensure rapid restoration in case of ransomware attacks or destructive malware activity.
- Restrict External Script Execution: Control and monitor the use of scripting and command-line interfaces across cloud and container environments to limit execution of unauthorized payloads.
- Threat Intelligence Integration: Continuously incorporate intelligence on emerging tools and techniques used by TeamPCP and similar actors to proactively update security policies and defensive measures.
MITRE ATT&CK Techniques Associated with TeamPCP
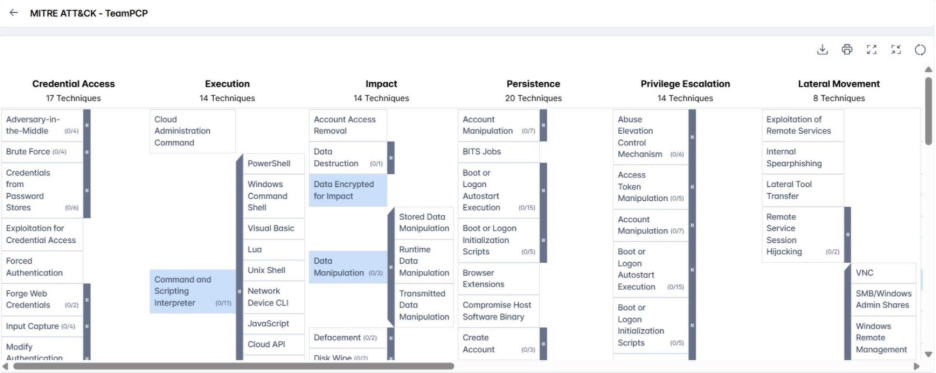
- External Remote Services (T1133): Adversaries leverage externally accessible services such as VPN gateways, Citrix, remote management interfaces, Docker APIs, Kubernetes control planes, and dashboards to gain initial access or maintain persistence.
- Exploit Public-Facing Application (T1190): Threat actors exploit Internet-facing applications with software flaws, misconfigurations, or weak access controls to infiltrate cloud-hosted services.
- Cron (T1053.003): The cron scheduler on Unix/Linux systems is abused to execute malicious tasks at startup or on a scheduled basis, supporting recurring execution for persistence.
- Command and Scripting Interpreter (T1059): Command-line and scripting environments are used to execute payloads, run scripts, download tools, perform system reconnaissance, and enable remote execution across different platforms, including Windows, macOS, and Linux.
- Container Administration Command (T1609): Container management interfaces such as Docker daemons or Kubernetes APIs are exploited to execute commands within containers, deploy malicious containers, and pivot to other systems within the environment.
- Deploy Container (T1610): Adversaries deploy containers to execute malicious processes, evade defenses, or facilitate lateral movement. Containers may be deployed from malicious or benign images, across multiple nodes, or configured without restrictions to bypass security controls.
- Implant Internal Image (T1525): Cloud or container images are modified to include malicious code, ensuring persistence and enabling re-infection or deployment of additional payloads after initial compromise.