Vice Society, also tracked by DEV-0832 and commonly referred to as Vanilla Tempest, is a financially motivated ransomware group that has been active since at least June 2021. The group has established a reputation for targeting a wide range of industries, with a particular focus on education, healthcare, and manufacturing, while also expanding operations across numerous other sectors worldwide.

Vice Society’s activity has drawn attention due to its operational maturity, heavy reliance on legitimate administrative tools, and technical overlaps with other ransomware families, including similarities to the Rhysida ransomware group.
Operational Motivation and Attack Lifecycle
Vice Society’s campaigns are driven primarily by financial extortion. The group typically conducts targeted intrusions rather than opportunistic mass attacks. In a common intrusion scenario, operators first identify organizations within preferred sectors and regions, then attempt to gain initial access through phishing, social engineering, or exploitation of exposed systems. Once inside a victim’s environment, they move laterally, harvest credentials, and prepare the network for ransomware deployment.

The end goal is twofold: encrypt critical systems to disrupt operations and exfiltrate sensitive data to enable double extortion. Victims are pressured to pay ransom not only to regain access to encrypted files but also to prevent the public release of stolen data.
Geographic Reach and Targeted Industries

Vice Society’s operations are global in scope. Confirmed target countries include the United States, United Kingdom, Canada, Australia, France, Germany, Spain, Italy, India, Singapore, Saudi Arabia, Brazil, Argentina, the Netherlands, Sweden, Poland, New Zealand, the United Arab Emirates, and dozens of others across Europe, the Americas, the Middle East, and Asia-Pacific. This geographic diversity indicates a broad victim selection strategy rather than a focus on any single political or regional objective.
The group has demonstrated an ability to operate across nearly all major economic sectors. Targeted industries include automotive, banking and financial services (BFSI), chemicals, construction, consumer goods, education, energy and utilities, government and law enforcement, healthcare, hospitality, IT and IT-enabled services, manufacturing, media and entertainment, mining, pharmaceuticals and biotechnology, professional services, retail, technology, telecommunications, and transportation and logistics. The breadth of targeting highlights Vice Society’s adaptability and the sector-agnostic nature of its ransomware operations.
Malware, Tools, and Living-off-the-Land Techniques
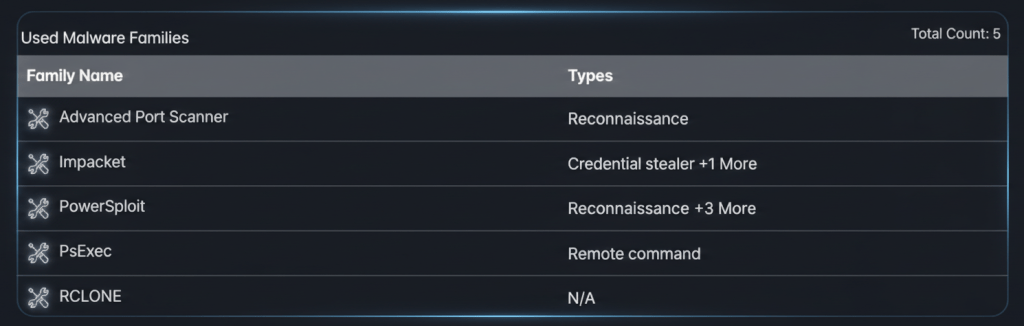
Vice Society relies on a mix of custom ransomware payloads and commodity tools, deliberately minimizing the use of bespoke malware to evade detection. Five primary malware and tool families have been consistently associated with the group.
Advanced Port Scanner is used extensively for reconnaissance. Although it is a legitimate network scanning utility, Vice Society leverages it to identify open ports, enumerate services, and locate vulnerable systems for further exploitation.
Impacket, an open-source Python toolkit for interacting with network protocols, plays a central role in lateral movement and remote command execution. Vice Society has abused Impacket’s WMIexec and atexec.py capabilities to execute commands via Windows Management Instrumentation and Task Scheduler, allowing stealthy remote execution across compromised networks.
PowerSploit, an offensive PowerShell framework developed for penetration testing, is used to automate reconnaissance, credential access, persistence, and defense evasion. Microsoft security researchers have observed multiple variations of DEV-0832 PowerShell scripts over time, indicating active development. Some scripts are limited to system discovery, while others are capable of persistence, data exfiltration, and even ransomware distribution.
PsExec, a legitimate Sysinternals remote execution tool created by Mark Russinovich, is routinely abused for lateral movement. Vice Society uses PsExec to remotely launch PowerShell commands, batch scripts, and ransomware payloads across networks.
Rclone is used during data exfiltration phases, allowing attackers to transfer large volumes of stolen data to attacker-controlled storage using encrypted channels.
Observations and Advanced Tradecraft
Microsoft has closely tracked DEV-0832 activity and identified several consistent operational behaviors. In many intrusions, the group stages ransomware payloads in hidden Windows shares, often using share names containing a “$”.

After completing data exfiltration, ransomware is distributed across local devices, likely through Group Policy Objects (GPOs).
Vice Society also demonstrates cross-platform capabilities. Microsoft confirmed the deployment of a Vice Society Linux encryptor targeting ESXi servers, enabling the group to impact virtualized infrastructure.
In addition to ransomware, DEV-0832 has deployed commodity backdoors such as SystemBC and PortStarter. SystemBC is used as a remote access trojan and proxy, with one observed instance involving a PowerShell command launching a SystemBC session labeled “socks.”

PortStarter, written in Go, enables firewall modification and outbound connections to predefined command-and-control servers.
Credential Harvesting and Privilege Escalation
Credential theft is a critical phase of Vice Society’s operations. Rather than relying solely on tools like Mimikatz, DEV-0832 frequently abuses comsvcs.dll and MiniDump to extract LSASS memory dumps, obtaining cached credentials. When domain administrator privileges are achieved, attackers have been observed exfiltrating the NTDS.dit file for offline cracking.
The group has also used Kerberoasting, leveraging the PowerSploit module Invoke-Kerberoast to request and crack encrypted Kerberos service tickets. Because service account passwords often do not expire, this technique remains highly effective for persistent access. Microsoft 365 Defender is capable of detecting this activity through AMSI and machine learning, and alerts tied to Kerberoast activity often indicate a human-operated intrusion.
In at least one intrusion, DEV-0832 created new administrative accounts with naming conventions designed to blend in with legitimate admin users, allowing persistence without deploying additional malware.
Conclusion
Vice Society (DEV-0832) is a financially motivated ransomware actor that conducts targeted, human‑operated intrusions using legitimate administrative tools, PowerShell‑based tradecraft, and systematic credential harvesting to enable data theft and large‑scale encryption.

Cyble’s AI‑driven threat intelligence identifies Vice Society as a persistent and globally active ransomware threat, and organizations can reduce exposure by leveraging Cyble’s real‑time visibility into ransomware operations, attacker infrastructure, and emerging extortion campaigns.
Book a personalized demo today or explore how Cyble’s external threat assessment report aligns with your security stack.
Recommendation and Mitigation Strategies
- Harden Access: Patch internet-facing systems and enforce email/security controls to prevent phishing and exploitation.
- Control Administrative Tools: Monitor and restrict PowerShell, PsExec, WMI, and Impacket usage.
- Protect Credentials: Use MFA, least-privilege access, and monitor for LSASS dumps or Kerberoasting activity.
- Detect Lateral Movement: Watch for hidden shares, GPO changes, and abnormal network activity.
- Strengthen Endpoints: Enable EDR, tamper protection, and detect DLL side-loading or process injection.
- Limit Data Exfiltration: Segment networks, filter outbound traffic, and monitor large or unusual transfers.
- Prepare for Ransomware: Maintain offline backups and test incident response plans for double-extortion attacks.
MITRE ATT&CK Techniques Associated with Vice Society
- Exploit Public-Facing Application (T1190): Vice Society exploits vulnerabilities in internet-facing systems to gain an initial foothold in victim networks.
- Valid Accounts (T1078): The group abuses compromised legitimate user or administrator accounts to access environments and maintain persistence.
- Windows Management Instrumentation (T1047): Vice Society leverages WMI to execute commands as part of its “living-off-the-land” strategy, blending malicious activity with normal administrative behavior.
- Scheduled Task/Job (T1053): The group creates or modifies scheduled tasks to enable recurring execution of malicious code and ensure continued access.
- Registry Run Keys / Startup Folder (T1547.001): Vice Society establishes persistence by creating or modifying registry-based autostart entries that execute malware upon system reboot.
- Exploitation for Privilege Escalation (T1068): Vice Society exploits the PrintNightmare vulnerabilities (CVE-2021-1675 and CVE-2021-34527) to elevate privileges within compromised environments.
- Process Injection (T1055): The group injects malicious code into legitimate processes to evade security controls and maintain stealth.
- Sandbox Evasion (T1497): Vice Society employs evasion techniques, such as delayed execution, to hinder sandbox analysis and malware detection.
- Data Encrypted for Impact (T1486): The group encrypts data across victim systems to disrupt operations and force ransom payments.
- Account Access Removal (T1531): Vice Society changes victim account passwords to lock users out of systems and increase operational disruption.
Disclaimer: This profile is based on OSINT, Cyble research, and external sources. Cyble is not responsible for the accuracy of the data or any misuse of the information presented.