Read Cyble Analysis of APT29 “Cozy Bear”, its tactics, techniques, motivations, and affiliations, and how they are evolving in today’s threat landscape.
APT29 is a highly skilled and well-funded cyberespionage group believed to have operated on behalf of the Russian Federation since at least 2008. Their primary mission appears to be collecting intelligence to support Russia’s foreign and security policy decisions. APT29 predominantly targets Western governments and associated entities, including government ministries, agencies, political think tanks, and contractors. However, their operations have also extended to the governments of Commonwealth of Independent States members, as well as nations in Asia, Africa, and the Middle East.
Despite the high-profile exposure from the SolarWinds compromise in 2020, APT29 has persisted in executing multiple large-scale operations across different time zones. The group conducts extensive phishing campaigns targeting diplomatic entities in Europe, North America, and Asia, underscoring their substantial resources. Since the onset of the Russia-Ukraine conflict, APT29 has intensified its focus on Ukraine, demonstrating a strategic shift in its operations to align with evolving geopolitical interests.
APT29 has targeted Western and European governments, along with industries such as education, telecommunications, and medical research. Their focus extends to government-adjacent organizations, technology firms, and IT and business service providers that offer third-party access. APT29 consistently seeks to gain and maintain access to email systems while recently expanding its efforts to target cloud resources and source code repositories. These activities aim to gather intelligence relevant to Russian strategic interests and exploit third-party access for broader infiltration.

Figure 1 – Cyble Vision Threat Library
Country of Origin
APT29 is a threat group attributed to Russia’s Foreign Intelligence Service (SVR).
Targeted Nations
Australia, Azerbaijan, Belarus, Belgium, Brazil, Bulgaria, Canada, Chechnya, Chile, China, Cyprus, Czech, Denmark, France, Georgia, Germany, Hungary, India, Ireland, Israel, Italy, Japan, Kazakhstan, Kyrgyzstan, Latvia, Lebanon, Lithuania, Luxembourg, Mexico, Montenegro, Netherlands, New Zealand, Poland, Portugal, Romania, Russia, Singapore, Slovakia, Slovenia, Spain, South Korea, Switzerland, Thailand, Turkey, Uganda, UAE, UK, Ukraine, USA, Uzbekistan and NATO.
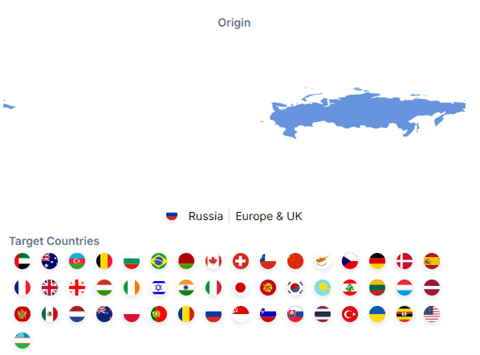
Figure 2 – Origin and Targeted Countries
Aliases
APT29 has various alias including ATK 7, Blue Dev 5, Blue Kitsune, BlueBravo, Cloaked Ursa, CloudLook, Cozy Bear, CozyDuke, Cranefly, Dark Halo, Grizzly Steppe, Group 100, ITG11, Iron Hemlock, Iron Ritual, Midnight Blizzard, Minidionis, Nobelium, NobleBaron, SilverFish, Solar Phoenix, SolarStorm, StellarParticle, TEMP.Monkeys, The Dukes, UNC2452, UNC3524 and Yttrium.
Targeted Sectors
APT29 has a diverse array of attack vectors and techniques that can be customized for its targets. So far, the group has been observed attacking the following sectors:
- Aerospace & Defense
- BFSI
- Education
- Energy & Utilities
- Government & LEA
- Healthcare
- Media & Entertainment
- Organization
- Pharmaceuticals & Biotechnology
- Telecommunication
- Transportation & Logistics
APT29 Lifecycle
APT29 employs a range of techniques for initial compromise, including phishing emails, supply chain attacks, exploiting publicly exposed infrastructure, and password spraying. Once inside, they often compromise service accounts or deploy backdoors to ensure persistence. APT29 is known to install malware on opaque network devices like SAN arrays, load balancers, and wireless access point controllers—systems that typically lack antivirus or endpoint detection tools. They use internal Windows applications like whoami, nlist, tasklist, netstat, wmic, and PowerShell for network reconnaissance. Additionally, APT29 leverages backdoors and malware to exfiltrate sensitive data, often abusing legitimate web services like Microsoft OneDrive and Notion APIs for stealthy command-and-control (C&C) communications.
Initial Infection
APT29 employed a range of techniques for initial compromise, including spearphishing emails that often contained malicious. These emails were crafted to lure targets into downloading and executing harmful content. Additionally, the group exploited vulnerabilities in public-facing infrastructure, such as exposed servers and applications, to gain unauthorized access. APT29 also used supply chain compromise.
Spearphishing
APT29 has a history of targeting high-profile individuals, including political parties, governments, and embassies, through sophisticated spearphishing campaigns. These operations often involve emails containing malicious links either within the email body or embedded in lure documents. Clicking these links initiates a multi-stage infection chain, often involving HTML and JavaScript components. The figure below illustrates an example from a previous APT29 campaign, where a seemingly legitimate invitation to a charity concert in Ukraine was used as a lure.

Figure 3 – Malicious Attachment related to Invitation to Concert (Source: Google)
Exploited Vulnerabilities
APT29 is known for exploiting vulnerabilities in its campaigns. The group has targeted a range of well-known vulnerabilities, including JetBrains, Fortinet, Zimbra, Pulse Secure, Citrix VMware, etc. The following are the vulnerabilities exploited by APT29.
- CVE-2023-42793: JetBrains TeamCity Authentication Bypass Vulnerability.
- CVE-2021-1879: Apple iOS, iPadOS, and watchOS WebKit Cross-Site Scripting (XSS) Vulnerability.
- CVE-2020-4006: Multiple VMware Products Command Injection Vulnerability.
- CVE-2019-19781: Citrix ADC, Gateway, and SD-WAN WANOP Appliance Code Execution Vulnerability.
- CVE-2019-11510: Ivanti Pulse Connect Secure Arbitrary File Read Vulnerability.
- CVE-2019-9670: Synacor Zimbra Collaboration (ZCS) Improper Restriction of XML External Entity Reference.
- CVE-2018-13379: Fortinet FortiOS SSL VPN Path Traversal Vulnerability.
Establish Foothold and Privilege Escalation
Beginning on February 26, 2024, APT29 launched phishing campaigns with attachments containing links to a compromised, actor-controlled website, which redirected victims to a ROOTSAW dropper. This dropper then requested the download and execution of the second-stage WINELOADER. In July 2023, APT29 employed ROOTSAW’s delivery mechanisms and victim filtering to deploy a new downloader, ICEBEAT, targeting European diplomatic entities. For persistence, APT29 compromised accounts and installed malware on opaque network devices like SAN arrays, load balancers, and wireless access point controllers.
Persistence
APT29 primarily relies on backdoors to maintain a foothold in compromised environments, ensuring ongoing control over critical systems. They use a temporary file replacement technique, substituting legitimate utilities with malicious versions to execute their payloads and then restoring the original files. Similarly, they manipulate scheduled tasks, modifying them to run their tools before reverting them to their original configurations. APT29 routinely cleans up by removing their tools and backdoors once legitimate remote access is secured, often deploying a web shell on Microsoft Exchange servers after a successful compromise.
Defense Evasion
APT29 employed various techniques to evade detection and maintain stealth within compromised environments. They used the service control manager on remote systems to disable security monitoring services and leveraged AUDITPOL to prevent audit logs from being collected. Additionally, APT29 used netsh to configure firewall rules that restricted certain UDP outbound packets and disabled Purview Audit on targeted accounts before exfiltrating emails from Microsoft 365 tenants. To cover their tracks, they used SDelete to erase artifacts and routinely removed their tools, including custom backdoors, once remote access was secured. They also erased evidence of email export requests using Remove-MailboxExportRequest.
Tools used by APT29
APT29 utilizes a wide array of tools throughout its campaigns, each serving distinct purposes. Their toolkit includes 7-Zip, AdFind, ATI-Agent, AtNow, BEATDROP, BloodHound, CEELOADER, CloudDuke, Cobalt Strike, CosmicDuke, CozyDuke, Danfuan, EnvyScout, FatDuke, FoggyWeb, GeminiDuke, Geppei, GoldFinder, GoldMax, GraphicalNeutrino, GraphicalProton, HammerDuke, LiteDuke, MagicWeb, meek, Mimikatz, MiniDuke, OnionDuke, PinchDuke, PolyglotDuke, POSHSPY, PowerDuke, QUIETEXIT, RAINDROP, RegDuke, reGeorg, Rubeus, SeaDuke, Sharp-SMBExec, SharpView, Sibot, SoreFang, SUNBURST, SUNSPOT, SUPERNOVA, TEARDROP, TrailBlazer, WellMail, WellMess, WINELOADER and Living off the Land. These tools collectively enable them to conduct sophisticated and multifaceted operations.
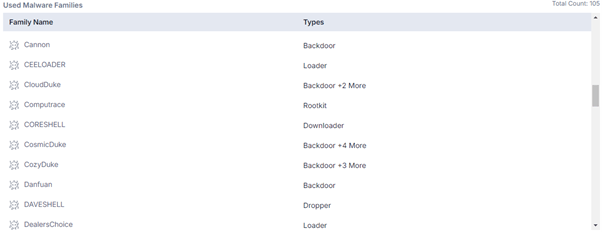
Figure 4 – APT29 Tools (Source: Cyble Vision)
AdFind: AdFind is a free command-line query tool designed for gathering information from Active Directory. APT29 leverages this tool to perform extensive enumeration of Active Directory environments.
AtNow: AtNow is a command-line utility that schedules programs and commands to run in the immediate future. Typically, commands are executed within 70 seconds or less after initiating the AtNow utility with the specified command.
BEATDROP: BEATDROP is a C-based downloader used by APT29, utilizing Trello for command-and-control (C&C). Upon execution, it maps its own copy of `ntdll.dll` into memory to execute shellcode within its process. BEATDROP creates a suspended thread with RtlCreateUserThread targeting NtCreateFile to download additional stages.
BloodHound: BloodHound is a tool designed to visualize Active Directory environments, featuring a front-end built on Electron and a back-end powered by a Neo4j database. It gathers data through ingestors, available in both PowerShell and C# versions. APT29 leverages BloodHound for thorough internal reconnaissance.
CEELOADER: CEELOADER is a downloader that decrypts and executes shellcode payloads directly in memory on the victim’s device. APT29 utilized the Cobalt Strike BEACON implant to persistently install CEELOADER as a Scheduled Task, configured to run as SYSTEM upon login on targeted systems.
CloudDuke: The CloudDuke toolset includes a loader, a downloader, and two backdoor variants, “BastionSolution” and “OneDriveSolution.” These backdoors enable remote command execution on compromised machines. APT29 deploys CloudDuke post-infection to establish and maintain a foothold within the network.
Cobalt Strike: Cobalt Strike is a commercial penetration testing tool that deploys an agent known as “Beacon” on victim machines. Beacon provides a wide range of capabilities, including command execution, keylogging, and lateral movement. It operates entirely in memory and supports multiple C&C and staging methods, such as HTTP, HTTPS, and DNS.
CosmicDuke: The CosmicDuke toolset is built around a primary information stealer, enhanced by various optional components. These components offer additional functionalities, such as persistence mechanisms and modules designed to exploit privilege escalation vulnerabilities, enabling CosmicDuke to execute with elevated privileges.
CozyDuke: CozyDuke is more than just a malware toolset; it is a modular malware platform centered around a core backdoor component. This core can receive instructions from the C&C server to download and execute various modules, which collectively equip CozyDuke with its extensive range of capabilities.
Danfuan: Danfuan is a DynamicCodeCompiler that compiles and executes C# code received in real-time, leveraging .NET dynamic compilation technology. The dynamically compiled code resides entirely in memory, never touching the disk. Danfuan functions as a backdoor on infected systems, providing covert access and control.
EnvyScout: EnvyScout is a dropper utilized by APT29 since at least 2021.
FatDuke: This advanced backdoor boasts a wide range of functionalities and highly flexible configuration options. Its code is extensively obfuscated with numerous opaque predicates, which are regularly recompiled and modified to evade detection by security products, enhancing its ability to bypass defenses.
FoggyWeb: FoggyWeb is a stealthy and highly targeted backdoor designed to silently exfiltrate sensitive information from a compromised AD FS server. It can also receive and execute additional malicious components delivered from a command-and-control (C&C) server, enhancing its capabilities and persistence.
GeminiDuke: The GeminiDuke toolset features a core information stealer, a loader, and several persistence-related components. Unlike CosmicDuke and PinchDuke, GeminiDuke focuses primarily on gathering details about the victim’s computer’s configuration.
Geppei: Geppei employs PyInstaller to convert Python scripts into executable files. It reads commands disguised as web access requests from legitimate IIS logs, which typically record data from IIS, such as web pages and apps. These disguised commands are logged normally but interpreted as instructions by Trojan.Geppei.
GoldFinder: GoldFinder appears to function as a custom HTTP tracer tool designed to log the route or hops a packet takes to reach a predefined C&C server. Upon execution, the malware sends an HTTP request to a hardcoded IP address and records the HTTP response in a plaintext log file, such as `loglog.txt`, created in the current working directory.
HammerDuke: HammerDuke is a straightforward backdoor, intended for similar purposes as SeaDuke. It is primarily distributed through CozyDuke, as the only known method of infection involves being downloaded and executed by CozyDuke on systems already compromised by that toolset.
MiniDuke: The MiniDuke toolset includes various downloader and backdoor components, commonly categorized as “stage 1,” “stage 2,” and “stage 3.” Additionally, a dedicated loader, known as the “MiniDuke loader,” is frequently associated with this toolset.
OnionDuke: The OnionDuke toolset comprises at least a dropper, a loader, an information-stealing trojan, and several modular variants with associated modules. OnionDuke was distributed through a compromised Tor exit node, enhancing its ability to spread.
PinchDuke: The PinchDuke toolset includes several loaders and a core information-stealing trojan. Notably, the loaders used in the PinchDuke toolset have also been observed in conjunction with CosmicDuke.
POSHSPY: POSHSPY leverages built-in Windows features, employing a “Living off the Land” approach to create a highly stealthy backdoor. By using WMI for storage and persistence and executing a PowerShell payload, it remains nearly invisible. Its infrequent beaconing, traffic obfuscation, and extensive encryption, combined with the use of legitimate, geographically local websites for command and control, make detection challenging.
PowerDuke: The PowerDuke backdoor offers a comprehensive range of features that enable the Dukes to thoroughly examine and control a system. Its capabilities are an extension of the anti-VM measures found in the initial dropper files. PowerDuke includes several commands that facilitate detailed system information gathering.
QUIETEXIT: QUIETEXIT reverses traditional SSH client-server roles. On a compromised system, the client establishes a TCP connection and acts as the SSH server, while the threat actor’s component initiates the SSH connection and sends a password. Though QUIETEXIT lacks persistence, APT29 has been seen configuring startup scripts and running commands to ensure its execution on system boot.
RAINDROP: Raindrop is a loader designed to deliver Cobalt Strike payloads.
SDelete: SDelete is a tool from the Microsoft Sysinternals suite that securely erases data, rendering it irretrievable.
SeaDuke: SeaDuke is a straightforward backdoor that primarily executes commands received from its C&C server, including file uploads and downloads, system command execution, and evaluation of additional Python code. Notably, SeaDuke is written in Python and designed for cross-platform use, functioning on both Windows and Linux systems.
SUNBURST / Solorigate: SUNBURST is a trojanized DLL crafted to integrate seamlessly into the SolarWinds Orion software update framework. APT29 has been using this sophisticated malware since at least February 2020.
TEARDROP: Various SUNBURST samples have been identified, each delivering different payloads. In at least one case, attackers used a novel memory-only dropper, referred to by researchers as TEARDROP, to deploy Cobalt Strike BEACON.
WINELOADER: WINELOADER is likely a variant of the private BURNTBATTER and MUSKYBEAT code families, which Mandiant uniquely ties to APT29. It shares similar design elements and anti-analysis techniques but is significantly more customized. It moves away from public loaders like DONUT or DAVESHELL and features a unique C&C mechanism.
Network Activities
APT29 employs various techniques for network activities. In one campaign, they conducted blocklisting and connectivity checks, and if successful, the malware used a Domain Generation Algorithm (DGA) to continuously generate domains. Upon receiving a domain from a CNAME DNS response, a new thread was spawned to invoke the HttpHelper.Initialize method for C&C communications, with an initial delay set by the SetTime command. In another campaign, the malware mimicked the Orion Improvement Program (OIP) protocol, blending in with legitimate SolarWinds activity. APT29 used Cobalt Strike, Silver Red teaming framework, and Zulip for C&C, aligning with their pattern of using legitimate services like Dropbox and OneDrive. They also utilized open proxies in residential IP ranges to blend with expected IP address pools in access logs.
Conclusion
APT29 demonstrates a sophisticated and adaptive approach to cyber espionage, leveraging a range of techniques and tools to achieve its objectives. Its use of advanced methods, such as Domain Generation Algorithms, disguising traffic as legitimate protocols, and employing open-source platforms for command and control, highlights its capability to blend malicious activities with legitimate operations. By utilizing techniques like traffic obfuscation, residential proxies, and integrating with trusted services, APT29 effectively maintains stealth and persistence, posing a significant threat to targeted organizations and systems.
Recommendations:
To counter APT29’s activities effectively, consider the following recommendations:
Advanced Threat Detection: Deploy and regularly update advanced threat detection systems to identify and respond to sophisticated techniques used by APT29, such as Domain Generation Algorithms and disguised C&C traffic.
Network Traffic Analysis: Implement comprehensive network monitoring and analysis to detect anomalies in traffic patterns, including those mimicking legitimate protocols or using open-source platforms for C&C.
Endpoint Security: Strengthen endpoint protection by using advanced anti-malware tools that can detect and block custom backdoors and remote access tools.
Regular Patching and Updates: Ensure all software, including operating systems and applications, is up-to-date with the latest security patches to mitigate vulnerabilities exploited by APT29.
Enhanced Logging and Forensics: Increase the depth of logging and forensic analysis to identify malicious activities and trace the actions of APT29, including examining legitimate plugin configuration files for signs of compromise.
Secure Configuration Practices: Review and harden the configuration of critical systems and applications, particularly those that handle sensitive information or network traffic.
User Training and Awareness: Educate employees on recognizing phishing attempts and other social engineering tactics commonly used by APT29 to gain initial access.
Incident Response Planning: Develop and regularly test an incident response plan to ensure rapid containment and remediation of any security incidents involving APT29’s techniques.
MITRE attack Techniques Associated with APT29
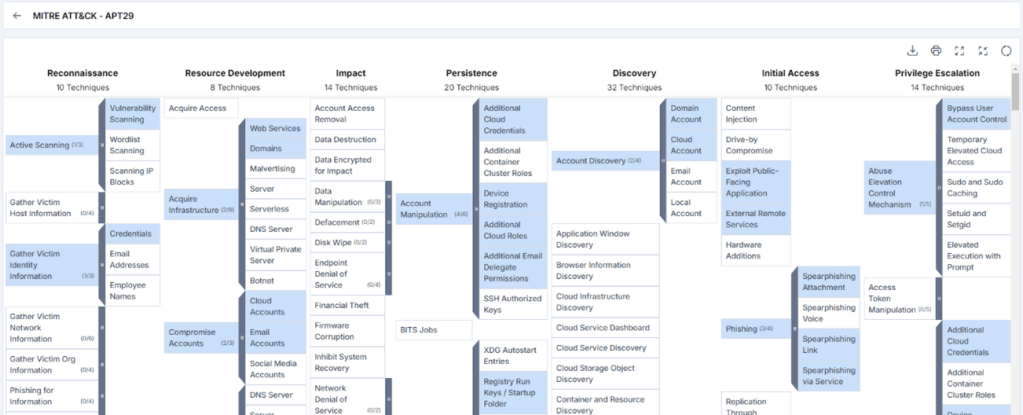
Figure 5 – MITRE ATT&CK (Source: Cyble Vision)
Phishing (T1566): APT29 uses spearphishing emails with malicious links or attachments to gain initial access.
Valid Accounts (T1078): APT29 may use stolen credentials to access networks or systems.
Exploit Public-Facing Application (T1190) – APT29 exploits vulnerabilities in public-facing infrastructure.
Command and Scripting Interpreter (T1059): APT29 uses PowerShell and other scripting languages for executing commands.
Scheduled Task/Job (T1053): APT29 installs persistence mechanisms such as scheduled tasks or startup scripts.
Registry Run Keys / Startup Folder (T1547): They modify registry keys or startup folders to ensure the backdoor runs on system boot.
Timestomping (T1099): They may manipulate timestamps to evade detection.