APT 3 is a highly capable, state-linked cyber‑espionage group that has been active since at least 2010. Also known by several aliases, including Bronze Mayfair, Buckeye, Gothic Panda, Group 6, Red Sylvan, TG–0110, and UPS Team, the group consistently demonstrates high technical proficiency in targeting government organizations and critical industries worldwide.
APT 3 has been attributed to Chinese state operators. The actors’ campaigns appear motivated by economic espionage and intelligence gathering aligned with Chinese national priorities. The initial focus centered on the United States and the UK, later shifting toward Hong Kong’s political entities.
Primary sectors targeted include aerospace and defense, construction and engineering, Manufacturing, Telecommunications, Transportation and logistics, and high-tech.
Tools and Malware Arsenal
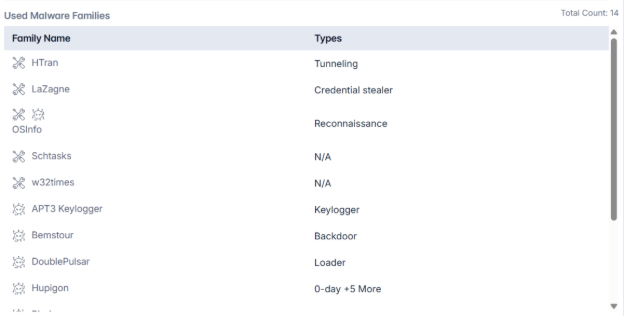
APT 3 employs an extensive toolkit comprising zero‑day exploits, credential harvesters, remote access trojans (RATs), tunneling tools, and reconnaissance utilities. Known malware families linked to the group include:
- HTran (tunneling utility)
- LaZagne (credential stealer)
- OSInfo (system reconnaissance)
- Schtasks (Windows utility used for persistence)
- w32time (Windows Time exploitation)
- APT 3 Keylogger
- Bemstour (zero‑day exploit)
- DoublePulsar (kernel‑mode loader)
- Hupigon
- Pirpi (backdoor)
- PlugX (reconnaissance/backdoor)
- shareip
- TTCalc (backdoor)
- EternalBlue (SMB exploit)
- Plus at least five additional, unnamed tools
Each tool has a distinct purpose. LaZagne retrieves stored credentials; OSInfo conducts reconnaissance; Schtasks establishes scheduled‑task persistence; w32time can be abused to manipulate system clocks; keyloggers harvest input; and kernel exploits like DoublePulsar and EternalBlue provide deep access.
Key Techniques & Procedures (TTPs)
APT 3 follows a well-structured approach aligned with the MITRE ATT&CK framework. Its attacks typically begin with spear-phishing emails containing malicious links, and it exploits known software vulnerabilities in tools like Adobe Flash and Internet Explorer to gain initial access.
Once inside a network, they execute malicious code using scheduled tasks, PowerShell scripts, and Windows command-line tools. Persistence is maintained through the use of stolen credentials, creation of new accounts, hijacked accessibility features, and placing malware in startup folders.
To avoid detection, APT 3 obfuscates files, deletes evidence, disguises accounts, and hides malicious processes. They also employ credential theft methods such as keylogging, password cracking, and dumping browser-stored passwords.
For internal reconnaissance, they scan network settings, user accounts, running processes, and system configurations. Lateral movement is achieved through remote desktop access and file transfers via administrative shares.
In the final phase, APT 3 collects sensitive data, especially Office documents, and stages it for exfiltration. Their operations are stealthy and persistent and aim at long-term access and intelligence gathering.
Conclusion
APT 3 remains one of the most dangerous cyber-espionage groups targeting global governments and industries. Known for using advanced tactics like zero-day exploits, credential theft, and long-term persistence, APT 3 continues to pose a challenge to national security and corporate assets.
Organizations must go beyond basic security, strengthen email defenses, patch systems quickly, and revisit old incidents to check for hidden compromises. As APT 3 evolves, only intelligence-driven strategies can keep pace.
Cyble offers powerful defense against APT threats. With AI-driven threat intelligence, dark web monitoring, vulnerability management, and brand protection, Cyble delivers a unified platform for early detection and rapid response. From digital forensics to executive monitoring, Cyble helps businesses stay protected from advanced threats like APT 3.
Schedule a demo to see how Cyble can secure your organization.
Defense and Mitigation Strategies
To protect against APT 3’s methods, targeted organizations should:
- Enforce phishing filtering and sandbox suspicious links
- Patch vulnerable software (e.g., Flash, IE, SMB services)
- Monitor scheduled tasks, registry entries, and sticky keys activity
- Use behavioral analytics to detect credential dumping or lateral movement
- Segment networks and limit admin privileges
- Deploy endpoint detection covering memory dumps and RDP/SMB usage
- Collect threat intelligence on APT 3 malware families, domains, and IOCs
MITRE ATT&CK Techniques Associated with APT 3
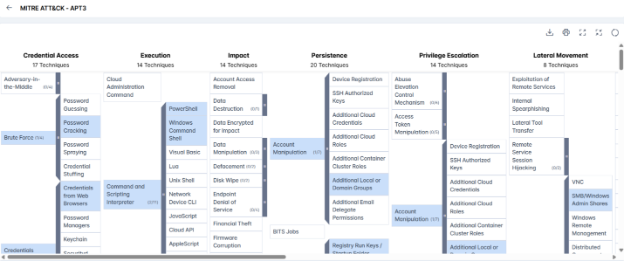
- Spearphishing Link (T1566.002): APT 3 has used spearphishing emails containing malicious links to gain initial access to target systems.
- Scheduled Task (T1053.005): A downloader sets up scheduled tasks to maintain persistence during system logon.
- PowerShell (T1059.001): APT 3 uses PowerShell scripts to download and execute malicious payloads after exploitation.
- Windows Command Shell (T1059.003): Executes commands such as “cmd.exe /C whoami” and runs remote instructions on compromised systems.
- Exploitation for Client Execution (T1203): Targets vulnerabilities in Adobe Flash Player (CVE-2015-3113) and Internet Explorer (CVE-2014-1776).
- Malicious Link (T1204.001): Victims are tricked into clicking harmful links sent via spearphishing emails.
- Domain Accounts (T1078.002): Leverages valid user accounts within the target’s domain to maintain access.
- Additional Local or Domain Groups (T1098.007): Adds compromised accounts to admin groups to retain elevated privileges.
- Local Account (T1136.001): Creates or enables accounts such as support_388945a0 for long-term access.
- Windows Service (T1543.003): Deploys custom tools to create and manage malicious services for persistence.
- Accessibility Features (T1546.008): This feature replaces system binaries like sethc.exe (Sticky Keys) to create unauthorized backdoor access.
- Registry Run Keys / Startup Folder (T1547.001): Places scripts in startup folders to automatically launch malware during system boot.
- DLL Search Order Hijacking (T1574.001): Uses DLL hijacking, including bundling malicious DLLs with trusted applications like Chrome.