A comprehensive threat profile on Leviathan, a Chinese-sponsored cyberespionage group, notorious for its sophisticated campaigns targeting both individuals and global entities.
Leviathan, an Advanced Persistent Threat (APT) group based in the Haikou, Hainan Province, People’s Republic of China (PRC), has been active since at least 2009. They have targeted governmental organizations, companies, and universities across a diverse array of industries, including biomedical, robotics, and maritime research. Their operations span the United States, Canada, Europe, the Middle East, and the South China Sea, as well as industries encompassed by China’s Belt and Road Initiative.
Leviathan frequently employs phishing emails with malicious attachments, often utilizing JavaScript to deploy malware like Cobalt Strike. Researchers have observed the group setting up fake websites impersonating defense contractors as part of its operations. It is particularly skilled at rapidly adapting proof-of-concept (POC) exploits for new vulnerabilities, targeting networks with specific infrastructure vulnerabilities.
Additionally, Leviathan conducts regular reconnaissance on networks of interest, including those in Western countries. This continuous surveillance enables them to swiftly identify and exploit vulnerable, outdated, or unmaintained devices. The group has a history of successfully exploiting vulnerabilities dating back to 2017, demonstrating its ability to capitalize on both new and existing security weaknesses.
Figure 1 – Cyble Vision Threat Library
Country of Origin
This APT group is of Chinese origin.
Targeted Nations
Belgium, Cambodia, Germany, Hong Kong, Indonesia, Laos, Malaysia, Myanmar, New Zealand, Norway, Philippines, Saudi Arabia, Switzerland, Thailand, UK, USA, Vietnam and Asia Pacific Economic Cooperation (APEC).
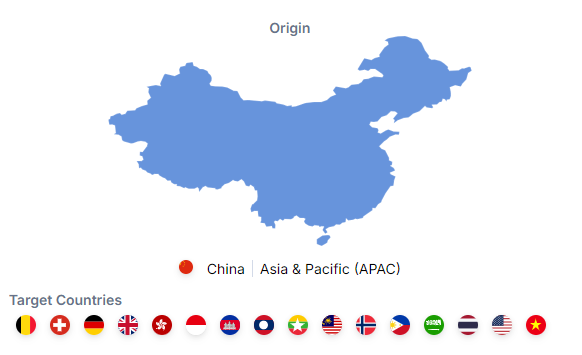
Figure 2 – Origin and Targeted Countries
Aliases
Leviathan has various aliases, including APT40, Kryptonite Panda, and TEMP.Periscope, TEMP.Jumper, Bronze Mohawk, Mudcarp, Gadolinium, ATK 29, ITG09, TA423, Red Ladon, Gingham Typhoon and ISLANDDREAMS.
Targeted Sectors
Leviathan has a diverse array of attack vectors and techniques that can be customized for its targets. So far, the group has been observed attacking the following sectors:
- Aerospace & Defense
- Education
- Government & LEA
- Manufacturing
- Technology
- Transportation & Logistics
Leviathan Lifecycle
Leviathan employs a variety of techniques for initial compromise, including exploiting web servers, spear phishing campaigns delivering both publicly available and custom backdoors, and strategic web compromises. They utilize an array of malware and tools, including those commonly used by other threat groups, to establish a foothold. The group sometimes uses executables with code-signing certificates to avoid detection. Leviathan leverages a mix of custom and publicly available credential-harvesting tools to escalate privileges and access other systems using compromised credentials. For internal reconnaissance and lateral movement, they use RDP, SSH, native Windows capabilities, legitimate software, custom scripts, web shells, and tunnelers. They maintain persistence through backdoors, compressing and encrypting stolen data with rar.exe before exfiltration. Leviathan has also developed tools like PAPERPUSH to enhance data targeting and theft.
Initial Infection
Leviathan employed a range of techniques for initial compromise, including spearphishing emails that often contained malicious attachments or links to Google Drive. These emails were crafted to lure targets into downloading and executing harmful content. Additionally, the group exploited vulnerabilities in public-facing infrastructure, such as exposed servers and applications, to gain unauthorized access.
Spearphishing
Leviathan has previously targeted high-profile individuals in the defense and government sectors through sophisticated spear-phishing campaigns. These operations often involved the use of newly created or compromised email and social media accounts. The group is known for leveraging PowerShell and Visual Basic scripts in their malicious payloads, typically embedded in macro-enabled Office documents or hyperlinks to malicious sites. These well-crafted social engineering tactics were designed to deceive recipients into executing malware, compromising their systems. The following figure illustrates an example of a Microsoft licensing-based lure used by Leviathan in a previous campaign.
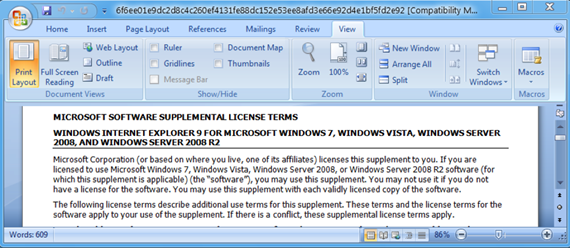
Figure 3 – Malicious Attachment related to Microsoft Licensing (Source: ProofPoint)
Exploited Vulnerabilities
Leviathan is known for quickly weaponizing vulnerabilities in its phishing campaigns, often exploiting them within days of their public disclosure. The group has targeted a range of well-known vulnerabilities, including those in Log4J, Atlassian Confluence, and Microsoft Exchange. Their strategy includes leveraging proof-of-concept (POC) exploits for newly disclosed high-profile vulnerabilities, enabling them to capitalize on these weaknesses almost immediately after they are made public. This rapid exploitation underscores Leviathan’s agility and sophistication in adapting to emerging security flaws, making them a persistent and evolving threat. The following are the vulnerabilities exploited by Leviathan.
- CVE 2021 44228
- CVE-2021-31207
- CVE-2021- 26084
- CVE-2021-31207
- CVE-2021-34523
- CVE-2021-34473
- CVE-2017-0199
- CVE-2017-8759
- CVE-2017-11882
- CVE-2012-0158
Establish Foothold and Privilege Escalation
Leviathan employs a diverse array of malware and tools to gain an initial foothold, often utilizing publicly available software or tools commonly used by other threat groups. In certain instances, they have deployed executables with code-signing certificates to evade detection. Leviathan frequently targets VPN and remote desktop credentials, allowing them to secure access to a targeted environment. This approach can be particularly effective, as obtaining these credentials reduces their reliance on malware, enabling them to continue their operations more covertly and efficiently.
Leviathan utilizes a combination of custom and publicly available tools for credential harvesting, enabling it to escalate privileges and extract password hashes. They employ custom utilities like HOMEFRY, a password dumper, and a cracker, often in conjunction with their AIRBREAK and BADFLICK backdoors. Additionally, they are known to use widely recognized tools such as the Windows Sysinternals ProcDump utility and the Windows Credential Editor (WCE) during their intrusions, further enhancing their capability to compromise targeted systems.
Persistence
Leviathan predominantly uses backdoors, including web shells, to maintain a foothold in compromised environments and ensure control over vital systems. They favor web shells, often opting for publicly available ones. Tools like AIRBREAK and PHOTO initially used for establishing access, continue to facilitate their presence. Additionally, some of their malware leverages legitimate sites like GitHub, Google, and Pastebin for command and control (C&C) communications, helping them evade typical network detection and blend in with normal traffic.
Defense Evasion
Leviathan employs sophisticated techniques to conceal and exfiltrate stolen data. They use steganography to hide data within other files stored on GitHub, making detection difficult. They also employ protocol impersonation, utilizing Dropbox API keys to upload stolen data, mimicking legitimate use of the service. Their methods include protocol tunneling and multi-hop proxies, such as Tor, to obscure their tracks. Additionally, they use domain typosquatting for C&C infrastructure. To facilitate exfiltration, they archive, encrypt, and stage collected data both locally and remotely, often exfiltrating it over the C&C channel.
Tools used by Leviathan
Leviathan utilizes a wide array of tools throughout its campaigns, each serving distinct purposes. Their toolkit includes AIRBREAK, BADFLICK, BlackCoffee, China Chopper, Cobalt Strike, DADJOKE, Dadstache, Derusbi, Gh0st RAT, GRILLMARK, HOMEFRY, LUNCHMONEY, MURKYTOP, NanHaiShu, PlugX, scanbox, SeDLL, Windows Credentials Editor, ZXShell, and various “living off the land” techniques. These tools collectively enable them to conduct sophisticated and multifaceted operations.

Figure 4 – Leviathan Tools (Source: Cyble Vision)
AIRBREAK: AIRBREAK, also known as Orz, is a JavaScript-based backdoor that retrieves commands embedded in hidden strings on compromised webpages and actor-controlled profiles on legitimate services. The threat actor uses AIRBREAK to establish an initial foothold in the target system.
BADFLICK: BADFLICK is a versatile backdoor that can alter the file system, create a reverse shell, and adjust its command-and-control configuration. The threat actor employs BADFLICK to gain an initial foothold in the target system.
BlackCoffee: ZoxPNG is a minimalistic RAT that embeds data within PNG files for communication with the C2 server. It supports 13 native commands and can execute arbitrary code from the server, allowing attackers to extend its capabilities with custom shellcode.
China Chopper: China Chopper is a remote access tool that enables attackers to control systems running a web server application. The threat actor uses China Chopper to establish and maintain persistence on the compromised system.
Cobalt Strike: Cobalt Strike is a commercial penetration testing tool that deploys an agent called ‘Beacon’ on victim machines. Beacon offers extensive functionalities, including command execution, keylogging, and lateral movement. It operates in-memory and supports various C2 and staging methods, including HTTP, HTTPS, and DNS.
DADJOKE: DADJOKE was found distributed via email, targeting a Southeast Asian Ministry of Defense. It arrives as an embedded EXE within a Word document, utilizing remote templates and a macro with multiple GET requests. The payload is deployed through load-order hijacking of a benign Windows Defender executable, establishing an initial foothold.
Dadstache: Dadstache RAT is a remote access trojan used by TAs for persistence data collection and data exfiltration.
Derusbi: Derusbi is a backdoor Trojan utilized by a select group of attackers, including the Rancor group. This loader decrypts its functionality through an encrypted payload, requiring the loading executable to supply a 32-byte key via the command line for decryption.
Gh0st RAT: Gh0st RAT is a remote access trojan for Windows that has been employed to infiltrate some of the most sensitive computer networks worldwide.
GRILLMARK: This proxy-aware HTTP backdoor operates as a service, utilizing the compromised system’s proxy settings to access the internet. Its command-and-control (C&C) traffic is base64-encoded, and files sent to the server are compressed using aPLib.
HOMEFRY: HOMEFRY is a 64-bit Windows password dumper and cracker, often used with AIRBREAK and BADFLICK backdoors. It features XOR x56 obfuscation for some strings and accepts two command-line arguments: one for displaying cleartext credentials and another for displaying credentials, NTLM hashes, and malware version.
LUNCHMONEY: LUNCHMONEY is an uploader that exfiltrates files from infected systems to Dropbox.
MURKYTOP: MURKYTOP is a command-line reconnaissance tool that allows users to execute files under different user accounts, move or delete local files, schedule remote AT jobs, conduct network host discovery, scan for open ports, and gather OS, user, group, and share information on remote hosts.
NanHaiShu: NanHaiShu is malware used by TAs to exfiltrate the data from the infected system or network.
PlugX: PLUGX is a sophisticated remote access tool that has been active since around 2012. Although numerous variants have emerged over the years, many share common features and characteristics.
ZXShell: ZXSHELL is a backdoor commonly available from Chinese hacker sites, featuring capabilities like port scanning, keylogging, screenshot capture, HTTP/SOCKS proxy setup, reverse command shell initiation, SYN flooding, and file management. The tool includes a GUI and documentation in Simplified Chinese.
Network Activities
Leviathan’s network communication tactics involve leveraging SMB/Windows Admin Shares and network share directories for reconnaissance and actor activities. This includes mounting SMB shares, scanning, and enumerating domains over the network. The actors frequently use web shells for C&C, passing commands over HTTPS through existing web servers on compromised appliances. By installing web shells on legitimate websites, they blend their traffic with legitimate data and redirect it as needed. This approach enables them to use compromised devices as launch points for further cyber attacks while evading detection by blending in with seemingly innocuous network traffic.
Conclusion
Leviathan’s campaigns demonstrate a sophisticated and multifaceted approach to cyberattacks, combining spear-phishing, exploitation of vulnerabilities, and advanced malware techniques. Their use of custom and publicly available tools, along with their adept manipulation of network communications and web shells, allows them to maintain persistent access and control over targeted environments. By leveraging legitimate services for C&C and employing a variety of methods to evade detection, Leviathan continues to pose a significant threat to high-value targets, particularly in defense and government sectors.
Recommendations:
To counter Leviathan’s campaigns effectively, organizations should implement the following recommendations:
Enhance Phishing Defenses: Educate employees on recognizing spear-phishing attempts and implement advanced email filtering solutions to block malicious attachments and links.
Patch Vulnerabilities Promptly: Regularly update and patch all systems and applications to mitigate the risk from newly discovered vulnerabilities that Leviathan exploits.
Strengthen Credential Security: Employ multi-factor authentication (MFA) and regularly update passwords to protect against credential theft and unauthorized access.
Monitor Network Traffic: Use advanced network monitoring tools to detect unusual activity and command-and-control traffic, particularly through legitimate services like GitHub or Google.
Implement Web Shell Detection: Regularly scan web servers for web shells and use anomaly detection to identify unauthorized changes or uploads.
Restrict Remote Access: Limit the use of remote desktop and VPN services to essential personnel and ensure they are secured with strong authentication methods.
Conduct Regular Security Audits: Regularly carry out security evaluations and penetration tests to discover and mitigate possible vulnerabilities before they become exploitable.
Employ Endpoint Protection: Use comprehensive endpoint security solutions to detect and block advanced threats, including in-memory and file-less malware.
Enhance Data Encryption: Encrypt sensitive data both in transit and at rest to protect against exfiltration attempts.
Develop an Incident Response Plan: Remember to develop and consistently revise a plan for responding to incidents in order to promptly manage and reduce the effects of any security violations.
By adopting these measures, organizations can bolster their defenses against Leviathan’s sophisticated tactics and reduce the risk of successful cyberattacks.
MITRE attack Techniques Associated with Leviathan
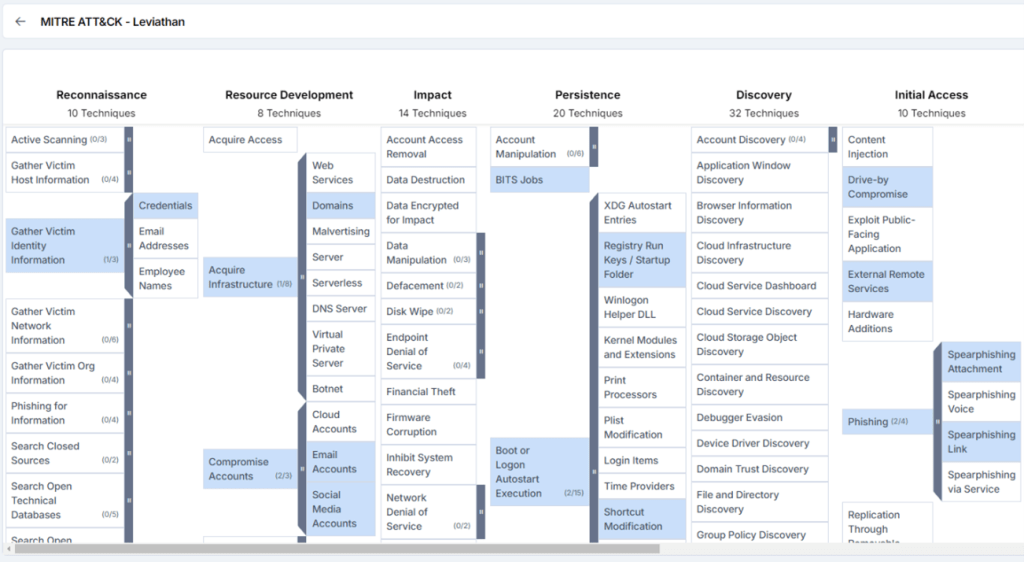
Figure 5 – MITRE ATT&CK (Source: Cyble Vision)
Gather Victim Identity Information Credentials (T1589.001): The Leviathan group uses various social engineering attacks to obtain victim credentials.
Phishing (T1566): Leviathan uses spear-phishing emails with malicious attachments or links.
Valid Accounts (T1078): They gain access through compromised credentials and social engineering.
Exploit Public-Facing Application (T1190) – Leviathan exploits vulnerabilities in web applications like Log4J and Microsoft Exchange.
Command and Scripting Interpreter (T1059): Use of PowerShell (T1059.001) and Visual Basic to execute malicious code.
Credential Dumping (T1003) – Tools like HOMEFRY are used to dump and crack credentials.
Obfuscated Files or Information (T1027) – Use of obfuscation and encryption in tools like ZoxPNG and GODADY.py.
Network Service Scanning (T1046) – Use of tools like MURKYTOP for network discovery.