The Middle East and Africa (META) region is undergoing a significant digital transformation, with businesses, governments, and critical sectors rapidly adopting new technologies. However, this shift has also led to an increase in cyber threats, targeting essential infrastructure, financial institutions, and government organizations. As digital landscapes evolve, cybercriminals are adapting their tactics, making it crucial for businesses to implement cybersecurity measures to safeguard sensitive data and digital assets.
One of the most effective tools in combating these cyber threats is threat intelligence. By gathering and analyzing real-time data on emerging threats, businesses can stay ahead of potential risks. Threat intelligence helps organizations understand the tactics, techniques, and procedures used by cyber attackers, enabling them to take proactive measures to defend their systems. This is particularly important in the META region, where businesses face unique challenges such as an evolving threat landscape and the complexity of securing diverse and expanding digital infrastructures.
In this article, we will explore the critical role of threat intelligence in protecting businesses in the META region, the security challenges enterprises face, and the most effective strategies to enhance cybersecurity resilience.
The Cyber Threat Landscape in the Middle East and Africa
The META region is experiencing an increasing number of cyberattacks, including ransomware, phishing, and nation-state attacks. Some of the key threats impacting businesses in this region include:
- Ransomware Attacks – Cybercriminals target enterprises with ransomware, encrypting critical data and demanding ransom payments.
- Advanced Persistent Threats (APTs) – Advanced attacks aimed at stealing sensitive information from governments and corporations.
- Insider Threats – Employees and third-party vendors can pose security risks by mishandling or intentionally leaking data.
- Phishing and Social Engineering – Cybercriminals exploit human vulnerabilities to gain unauthorized access to systems.
- Cloud Security Risks – The rapid adoption of cloud services has increased concerns about data breaches and compliance issues.
Understanding these threats is essential for implementing strong security measures. Threat intelligence solutions for META enterprises provide valuable insights to detect and mitigate cyber risks before they cause significant damage.
Enterprise Security Challenges in the META Region
Enterprises in the META region face unique cybersecurity challenges due to geopolitical tensions, evolving regulatory requirements, and digital expansion. Some of the key enterprise security challenges in META include:
- Lack of Cybersecurity Awareness – Many organizations struggle with inadequate employee training on cybersecurity best practices.
- Regulatory Compliance – Businesses must adhere to various data protection laws and regulations, such as the UAE’s Data Protection Law and Saudi Arabia’s cybersecurity framework.
- Threat Actors – Cybercriminals and nation-state hackers continuously develop new attack techniques to bypass security defenses.
- Shortage of Cybersecurity Talent – Organizations face difficulties in hiring and retaining skilled cybersecurity professionals.
- Increased Attack Surface – The adoption of IoT, cloud computing, and remote work has expanded attack vectors, making enterprises more vulnerable to cyber threats.
To overcome these challenges, enterprises must adopt threat intelligence solutions that provide comprehensive insights into emerging threats and vulnerabilities.
Enhancing Cybersecurity with Threat Intelligence in META
Threat intelligence empowers businesses with actionable data to predict, prevent, and respond to cyber threats effectively. Some of the ways enterprises can enhance cybersecurity with threat intelligence in META include:
- Real-Time Threat Intelligence – Continuous monitoring and analysis of threat data help organizations detect malicious activities before they escalate.
- Executive Threat Intelligence – Provides business leaders with strategic insights on cyber risks that impact their organizations.
- Threat Hunting and Incident Response – Security teams can proactively search for threats and mitigate them before they cause harm.
- Dark Web Monitoring – Identifying leaked credentials and sensitive data on the dark web prevents unauthorized access.
- Security Automation – Integrating threat intelligence with security tools improves response times and reduces manual effort.
By leveraging advanced threat intelligence solutions, enterprises can build a resilient security framework that mitigates cyber risks efficiently.
Top Threat Intelligence Platforms for META Enterprises
A threat intelligence platform provides comprehensive visibility into cyber threats, allowing enterprises to strengthen their security posture. Some key features to look for in top threat intelligence platforms include:
- Real-Time Threat Feeds – Access to continuously updated threat intelligence feeds enhances security decision-making.
- Integration with Security Tools – Seamless integration with SIEM, SOAR, and firewall solutions improves incident response capabilities.
- Automated Threat Detection – AI-driven analytics help identify suspicious activities and potential threats.
- Customized Threat Intelligence – Tailored threat insights based on industry-specific risks and attack patterns.
- Advanced Reporting and Analytics – Comprehensive reports provide security teams with actionable intelligence.
Selecting the right threat intelligence platform ensures businesses stay ahead of cyber threats while maintaining operational efficiency.
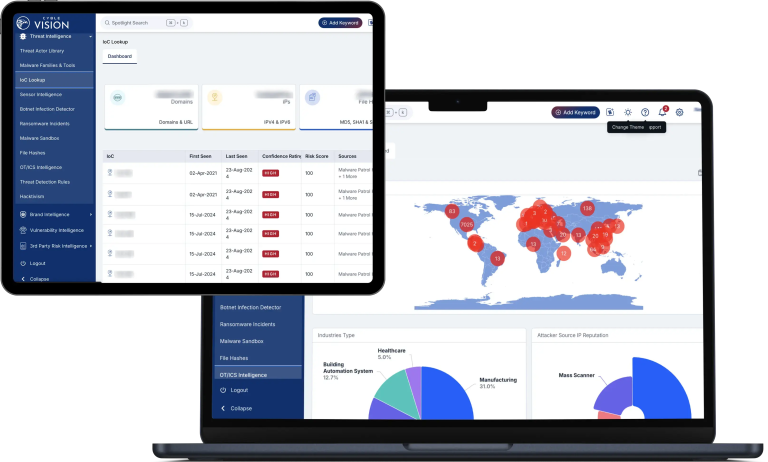
Cyble’s Cyber Threat Intelligence Platform
Cyble’s Cyber Threat Intelligence Platform provides organizations with real-time threat intelligence, helping them identify and respond to cyber threats effectively. The platform delivers:
- Comprehensive Threat Intelligence Feeds – Enables enterprises to detect and analyze emerging cyber threats.
- Dark Web and Deep Web Monitoring – Helps identify leaked credentials and compromised assets.
- Threat Hunting Capabilities – Empowers security teams to proactively investigate and mitigate cyber risks.
- AI-Powered Analytics – Enhances decision-making with data-driven threat intelligence insights.
By utilizing Cyble’s threat intelligence solutions, enterprises in the META region can gain valuable cybersecurity insights and safeguard their digital assets.
Conclusion
Threat intelligence solutions play a vital role in identifying emerging risks, preventing cyberattacks, and ensuring business continuity. By leveraging real-time threat intelligence and executive threat intelligence, organizations can enhance their security resilience and protect critical data.
The future of enterprise security in the META region depends on how well businesses can anticipate and respond to cyber threats. Are organizations ready to embrace advanced threat intelligence strategies to secure their digital assets? The time to act is now.
FAQs on Threat Intelligence Enterprise Security
What is threat intelligence and why is it important for businesses in the META region?
Threat intelligence involves gathering and analyzing data on emerging cyber threats to help organizations identify risks early. For businesses in the META region, it’s crucial for staying ahead of evolving threats targeting critical infrastructure and sensitive data.
How does threat intelligence improve enterprise security in the META region?
Threat intelligence helps organizations detect, analyze, and respond to cyber threats faster. By understanding attacker tactics, businesses in META can implement proactive security measures and better defend against targeted attacks.
What challenges do businesses in the META region face in implementing threat intelligence?
Businesses in the META region often deal with a rapidly evolving threat landscape, lack of skilled cybersecurity professionals, and diverse digital infrastructures, making it difficult to maintain effective threat intelligence programs.
How can threat intelligence help protect critical infrastructure in the META region?
Threat intelligence allows organizations to monitor and assess threats specifically targeting critical infrastructure. By identifying vulnerabilities early, businesses can deploy tailored defense strategies to safeguard essential services and systems.
What are the best strategies for leveraging threat intelligence in enterprise security?
The best strategies include integrating threat intelligence into security operations, automating threat detection, and fostering collaboration between teams. Regularly updating threat intelligence feeds and continuously monitoring emerging risks are key to maintaining security resilience.