First identified in June 2024, the Cicada3301 ransomware group has quickly carved out a place in the cybercrime world with a striking combination of advanced engineering and widespread targeting. In less than a year, the group has executed attacks against 30 organizations across critical sectors in over 15 countries, with the United States and the United Kingdom bearing the brunt of its operations.
Operating under a name reminiscent of the enigmatic online puzzle of the same name, Cicada3301 has managed to blend digital mystery with advanced malware capabilities. Despite the group’s public appearance being relatively new, online data suggest a deeper and more strategic development timeline behind the ransomware’s polished architecture.
Geographies and Industries

Cicada3301’s campaign has extended beyond English-speaking nations. According to incident telemetry and threat intelligence, Cicada3301 has targeted organizations across a wide range of countries, including the United States, the United Kingdom, Brazil, France, Italy, Spain, Japan, Canada, Switzerland, Singapore, Denmark, the Czech Republic, Jordan, the United Arab Emirates, and Tunisia.
The targeted sectors are just as diverse, ranging from BFSI (Banking, Financial Services, and Insurance), Government and Law Enforcement, Pharmaceuticals, and Manufacturing, to Telecommunications, IT and Professional Services, and even Agriculture and Livestock.
Technological Advancement and Rust-Based Development
Cicada3301 is among a growing cohort of threat actors developing ransomware in Rust, a modern, memory-safe programming language. This aligns them with other Rust-based threats, such as BlackCat, Hive, and RansomExx, all of which are known for their cross-platform compatibility and execution efficiency.
Cicada3301 supports multiple platforms, including Windows, Linux, VMware ESXi, and Network Attached Storage (NAS) systems. Even niche architectures like PowerPC are within its operational scope, a rare capability that demonstrates planning and technical depth.
Online data suggest that Cicada3301 shares structural and functional similarities with BlackCat ransomware, such as the parameter configuration interface, exception handling, and shadow copy deletion. However, Cicada3301’s distinguishing feature lies in its use of embedded credentials and a loader-key dependency, which raises the bar for defensive countermeasures.
Loader-Only Execution and Credential Innovation
The ransomware only activates upon receipt of a valid decryption key. This parameter ensures that the ransomware cannot be analyzed or executed by unintended parties, including researchers, unless they possess the correct key. This tight control over execution highlights Cicada3301’s advanced operational security and affiliate trust model.
An unusual and advanced technique employed by the group involves the use of a renamed Sysinternals PsExec tool (psexec0.exe) written to disk and executed from the C:\Users\Public\ directory. While PsExec is a common tool for remote execution, Cicada3301 integrates compromised credentials directly into the ransomware, eliminating the need for external access methods. This tactic is not commonly observed in current ransomware families and marks a notable evolution in lateral movement strategies.
Encryption Process and Readme Deployment
The ransomware begins by identifying valid drives using system calls, then recursively collecting files from directories. Specific exclusion patterns are matched to avoid encrypting essential or system-critical files. Each targeted file is first renamed with a .busy- [ProcessID] suffix before being queued for encryption.
The encryption pipeline includes:
- Public Key Deserialization via spki::traits::DecodePublicKey::from_public_key_pem
- RSA Encryption with OAEP padding
- Final renaming to filepath.[VictimID]
- Creation of a ransom note: RECOVER-[VictimID]-DATA.txt
This structured approach indicates high resource efficiency and the ability to rapidly encrypt environments without detection.
Tactics, Techniques, and Procedures (TTPs)
Cicada3301 employs a variety of tactics in its operations. It uses PowerShell scripting to execute code stealthily without triggering obvious system processes, often leveraging advanced frameworks to carry out its tasks.
To avoid detection, the ransomware deletes files and traces of its activity using native system commands, making forensic recovery more difficult. When stealing data, it exfiltrates information covertly over existing communication channels, disguising malicious traffic within normal network activity.
The group also communicates with its command servers using common internet protocols like HTTP/S, DNS, and SMB, blending in seamlessly with regular network traffic. Finally, Cicada3301 encrypts data extensively, locking files and even critical system components to maximize disruption and pressure victims into paying the ransom.
Affiliates and Underground Economy Ties
Cicada3301 also appears to operate as an affiliate model, offering a 20% commission for successful intrusions, specifically targeting skilled penetration testers. The group has set up a comprehensive web control panel, likely for managing deployments, affiliates, and ransom negotiations.
The combination of secure execution gates, advanced malware engineering, and monetization schemes aligns Cicada3301 more closely with professionalized cybercrime syndicates than with traditional ransomware gangs.
Conclusion
Cicada3301 represents a major advancement in ransomware, leveraging Rust’s efficiency, cross-platform reach, and innovative credential-based tactics to evade traditional defenses. It poses a serious threat to critical sectors like finance, healthcare, and infrastructure, demanding proactive, intelligence-driven security.
Cyble’s comprehensive threat intelligence platform offers real-time monitoring, vulnerability management, dark web surveillance, and incident response—all powered by AI and actionable insights. By integrating Cyble’s solutions, organizations can strengthen defenses, detect threats early, and respond quickly to ransomware like Cicada3301.
Don’t wait until it’s too late—schedule a FREE DEMO with Cyble today and take the first step toward protecting your defenses against ransomware risks.
Mitigations and Recommendations
Here are key mitigations to defend against Cicada3301 ransomware:
- Adopt Zero Trust: Continuously verify users and devices to limit lateral movement.
- Secure Credentials: Use multi-factor authentication and monitor for compromised credentials.
- Apply Least Privilege: Limit user permissions to reduce the attack surface.
- Use Endpoint Detection: Deploy tools to detect suspicious activities like PowerShell abuse and file renaming.
- Regular Backups: Maintain offline, tested backups to ensure quick recovery without ransom.
- Patch Systems: Keep all platforms updated and disable unnecessary services.
- Segment Networks: Restrict ransomware spread and monitor unusual network traffic.
- Plan Incident Response: Prepare and test ransomware-specific response plans.
- Leverage Threat Intelligence: Use services like Cyble for real-time threat insights and early warnings
MITRE Attack Techniques Associated with Cicada3301
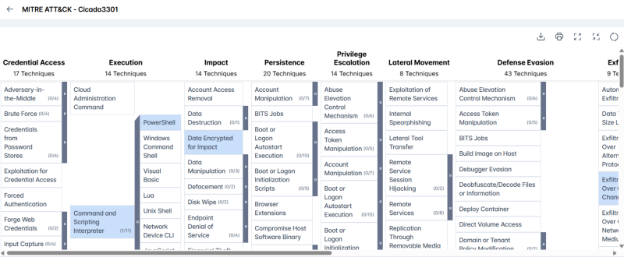
- Execution (TA0002) – PowerShell (T1059.001): Adversaries use PowerShell commands/scripts to execute code, discover info, and run payloads stealthily, often using tools like Empire and PowerSploit.
- Defense Evasion (TA0005) – File Deletion (T1070.004): Attackers delete files created during intrusions using OS commands like del, rm, or unlink to minimize forensic evidence.
- Exfiltration (TA0010) – Exfiltration Over C2 Channel (T1041): Data is stolen by embedding it within existing command and control communication channels.
- Command and Control (TA0011) – Application Layer Protocol (T1071): Adversaries communicate via common protocols (HTTP/S, DNS, SMB, SSH, RDP) to blend commands with regular network traffic.
- Impact (TA0040) – Data Encrypted for Impact (T1486): Ransomware encrypts user and system files, often propagates across networks, and may deface systems or send ransom notes to maximize disruption.